What is the BEST command to view configuration details of all interfaces in Gaia CLISH?
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer
If the Active Security Management Server fails or if it becomes necessary to change the Active to Standby, the following steps must be taken to prevent data loss. Providing the Active Security Management Server is responsible, which of these steps should NOT be performed:
To quickly review when Threat Prevention signatures were last updated, which Threat Tool would an administrator use?
You have enabled "Extended Log" as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
Examine the sample Rule Base.
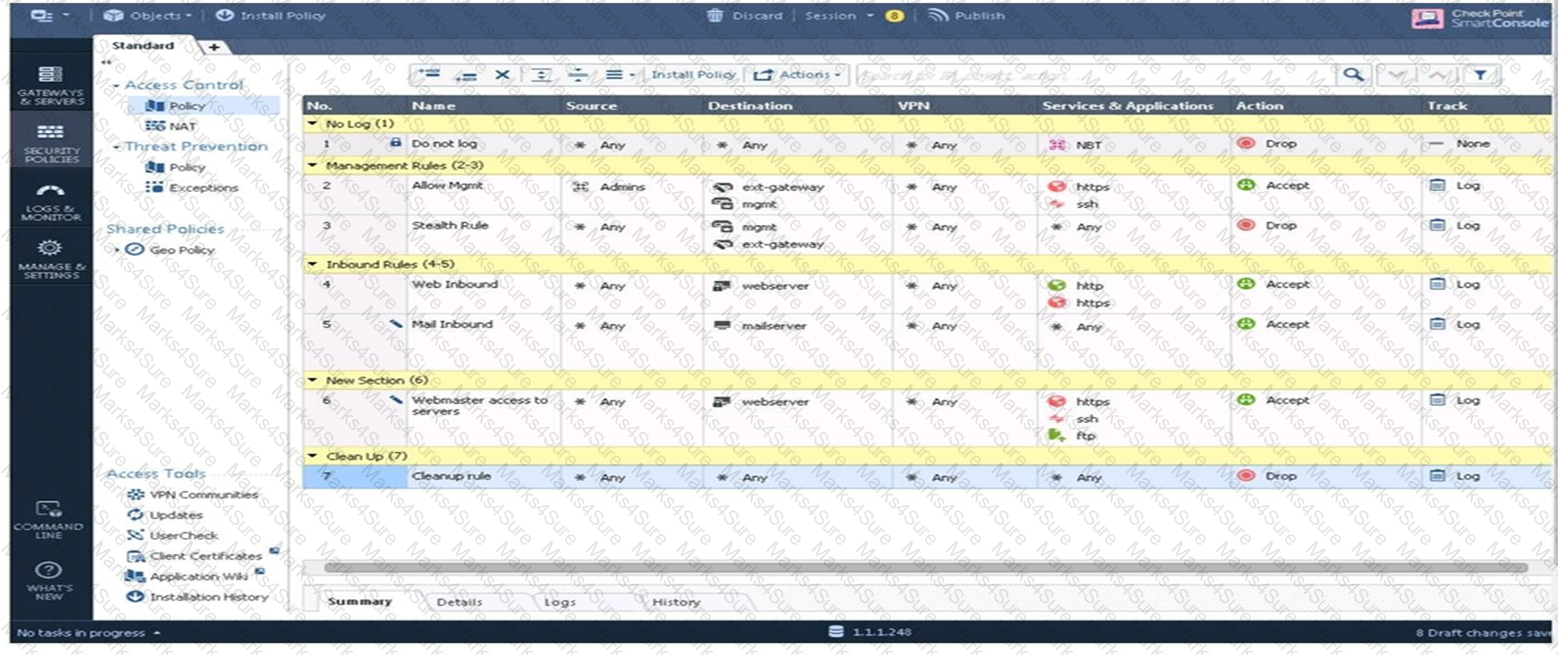
What will be the result of a verification of the policy from SmartConsole?
In the Check Point Security Management Architecture, which component(s) can store logs?
True or False: The destination server for Security Gateway logs depends on a Security Management Server configuration.
Fill in the blank: An identity server uses a ___________ for user authentication.
The competition between stateful inspection and proxies was based on performance, protocol support, and security. Considering stateful Inspections and Proxies, which statement is correct?
Which one of the following is a way that the objects can be manipulated using the new API integration in R80 Management?
Name the file that is an electronically signed file used by Check Point to translate the features in the license into a code?
Which option, when applied to a rule, allows all encrypted and non-VPN traffic that matches the rule?
When configuring LDAP User Directory integration, Changes applied to a User Directory template are:
Which Threat Prevention Software Blade provides comprehensive protection against malicious and unwanted network traffic, focusing on application and server vulnerabilities?
Gaia has two default user accounts that cannot be deleted. What are those user accounts?
Which type of Check Point license ties the package license to the IP address of the Security Management Server?
Which of the following is considered a "Subscription Blade", requiring renewal every 1-3 years?
Which Check Point supported authentication scheme typically requires a user to possess a token?
Which tool provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
Which method below is NOT one of the ways to communicate using the Management API’s?
True or False: More than one administrator can log into the Security Management Server with SmartConsole with write permission at the same time.
Session unique identifiers are passed to the web api using which http header option?
If an administrator wants to restrict access to a network resource only allowing certain users to access it, and only when they are on a specific network what is the best way to accomplish this?
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ___________.
What needs to be configured if the NAT property ‘Translate destination on client side’ is not enabled in Global properties?
What are valid authentication methods for mutual authenticating the VPN gateways?
In Logging and Monitoring, the tracking options are Log, Detailed Log and Extended Log. Which of the following options can you add to each Log, Detailed Log and Extended Log?
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
The purpose of the Communication Initialization process is to establish a trust between the Security Management Server and the Check Point gateways. Which statement best describes this Secure Internal
Communication (SIC)?
When configuring Anti-Spoofing, which tracking options can an Administrator select?
The ______ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
To ensure that VMAC mode is enabled, which CLI command you should run on all cluster members? Choose the best answer.
You had setup the VPN Community NPN-Stores' with 3 gateways. There are some issues with one remote gateway(l .1.1.1) and an your local gateway. What will be the best log filter to see only the IKE Phase 2 agreed networks for both gateways.
Phase 1 of the two-phase negotiation process conducted by IKE operates in ______ mode.
In a Distributed deployment, the Security Gateway and the Security Management software are installed on what platforms?
Fill in the blank: When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.
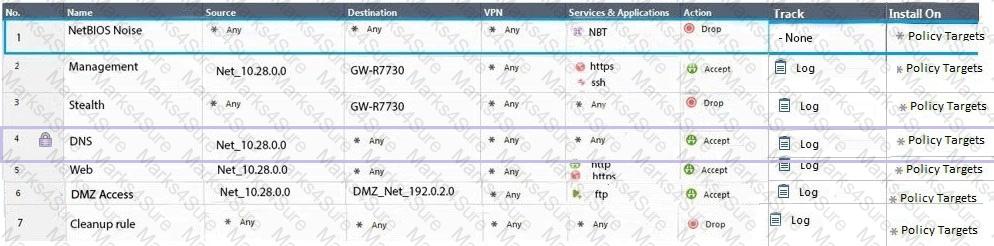
What is the possible explanation for this?
When installing a dedicated R80 SmartEvent server, what is the recommended size of the root partition?
Fill in the blanks: A Check Point software license consists of a__________ and _______.
In SmartConsole, objects are used to represent physical and virtual network components and also some logical components. These objects are divided into several categories. Which of the following is NOT an objects category?
A security zone is a group of one or more network interfaces from different centrally managed gateways. What is considered part of the zone?
Which Check Point Software Wade provides visibility of users, groups and machines while also providing access control through identity-based policies?
Which is a suitable command to check whether Drop Templates are activated or not?
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server (SMS). While configuring the VPN community to specify the pre-shared secret, the administrator did not find a box to input the pre-shared secret. Why does it not allow him to specify the pre-shared secret?
Which SmartConsole application shows correlated logs and aggregated data to provide an overview of potential threats and attack patterns?
When a gateway requires user information for authentication, what order does it query servers for user information?
To provide updated malicious data signatures to all Threat Prevention blades, the Threat Prevention gateway does what with the data?
URL Filtering employs a technology, which educates users on web usage policy in real time. What is the name of that technology?
The Network Operations Center administrator needs access to Check Point Security devices mostly for troubleshooting purposes. You do not want to give her access to the expert mode, but she still should be able to run tcpdump. How can you achieve this requirement?
Is it possible to have more than one administrator connected to a Security Management Server at once?
Which of the following is used to extract state related information from packets and store that information in state tables?
Fill in the blank: The position of an implied rule is manipulated in the __________________ window.
Full synchronization between cluster members is handled by Firewall Kernel. Which port is used for this?
Fill in the blank: A(n)_____rule is created by an administrator and configured to allow or block traffic based on specified criteria.
In HTTPS Inspection policy, what actions are available in the "Actions" column of a rule?
Which option will match a connection regardless of its association with a VPN community?
How many users can have read/write access in Gaia Operating System at one time?
Which one of the following is the preferred licensing model? Select the BEST answer
The default shell of the Gaia CLI is cli.sh. How do you change from the cli.sh shell to the advanced shell to run Linux commands?
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
There are four policy types available for each policy package. What are those policy types?
Fill in the bank: In Office mode, a Security Gateway assigns a remote client to an IP address once___________.
Both major kinds of NAT support Hide and Static NAT. However, one offers more flexibility. Which statement is true?
You want to set up a VPN tunnel to a external gateway. You had to make sure that the IKE P2 SA will only be established between two subnets and not all subnets defined in the default VPN domain of your gateway.
After the initial installation on Check Point appliance, you notice that the Management interface and default gateway are incorrect. Which commands could you use to set the IP to 192.168.80.200/24 and default gateway to 192.168.80.1.
Which one of these features is NOT associated with the Check Point URL Filtering and Application Control Blade?