Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
An engineer discovered a breach, identified the threat’s entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?
Which metric should be used when evaluating the effectiveness and scope of a Security Operations Center?
An automotive company provides new types of engines and special brakes for rally sports cars. The company has a database of inventions and patents for their engines and technical information Customers can access the database through the company's website after they register and identify themselves. Which type of protected data is accessed by customers?
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
Which attack method is being used when an attacker tries to compromise a network with an authentication system that uses only 4-digit numeric passwords and no username?
An employee received an email from a colleague’s address asking for the password for the domain controller. The employee noticed a missing letter within the sender’s address. What does this incident describe?
Which incidence response step includes identifying all hosts affected by an attack?
During which phase of the forensic process are tools and techniques used to extract information from the collected data?
A security incident occurred with the potential of impacting business services. Who performs the attack?
An engineer received an alert affecting the degraded performance of a critical server Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
Which security principle is violated by running all processes as root or administrator?
Which signature impacts network traffic by causing legitimate traffic to be blocked?
What is the difference between discretionary access control (DAC) and role-based access control (RBAC)?
Drag and drop the uses on the left onto the type of security system on the right.
A user received a malicious attachment but did not run it. Which category classifies the intrusion?
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
Which element is included in an incident response plan as stated m NIST SP800-617
Refer to the exhibit.
A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source After the attacker produces many of failed login entries, it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
What is the difference between inline traffic interrogation (TAPS) and traffic mirroring (SPAN)?
An engineer is working on a ticket for an incident from the incident management team A week ago. an external web application was targeted by a DDoS attack Server resources were exhausted and after two hours it crashed. An engineer was able to identify the attacker and technique used Three hours after the attack, the server was restored and the engineer recommended implementing mitigation by Blackhole filtering and transferred the incident ticket back to the IR team According to NIST SP800-61, at which phase of the incident response did the engineer finish work?
What are the two differences between stateful and deep packet inspection? (Choose two )
Refer to the exhibit.
A security analyst is investigating unusual activity from an unknown IP address Which type of evidence is this file1?
A company encountered a breach on its web servers using IIS 7 5 Dunng the investigation, an engineer discovered that an attacker read and altered the data on a secure communication using TLS 1 2 and intercepted sensitive information by downgrading a connection to export-grade cryptography. The engineer must mitigate similar incidents in the future and ensure that clients and servers always negotiate with the most secure protocol versions and cryptographic parameters. Which action does the engineer recommend?
A company is using several network applications that require high availability and responsiveness, such that milliseconds of latency on network traffic is not acceptable. An engineer needs to analyze the network and identify ways to improve traffic movement to minimize delays. Which information must the engineer obtain for this analysis?
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
Which system monitors local system operation and local network access for violations of a security policy?
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
Which vulnerability type is used to read, write, or erase information from a database?
What is the impact of false positive alerts on business compared to true positive?
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmatware2022-12-22.pcaps file. The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?
Refer to the exhibit.
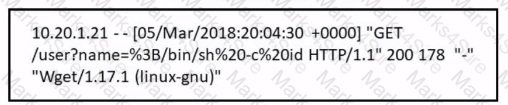
Which attack is being attempted against a web application?
An engineer needs to configure network systems to detect command and control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications. Which technology should be used to accomplish the task?
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
A SOC analyst detected connections to known C&C and port scanning activity to main HR database servers from one of the HR endpoints via Cisco StealthWatch. What are the two next steps of the SOC team according to the NISTSP800-61 incident handling process? (Choose two)
Drag and drop the security concept from the left onto the example of that concept on the right.
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
Drag and drop the elements from the left into the correct order for incident handling on the right.
A security engineer must protect the company from known issues that trigger adware. Recently new incident has been raised that could harm the system. Which security concepts are present in this scenario?
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
What is the impact of false positive alerts on business compared to true positive?
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
Refer to the exhibit.
Which stakeholders must be involved when a company workstation is compromised?
Drag and drop the access control models from the left onto the correct descriptions on the right.
Refer to the exhibit.
An attacker gained initial access to the company s network and ran an Nmap scan to advance with the lateral movement technique and to search the sensitive data Which two elements can an attacker identify from the scan? (Choose two.)
A developer is working on a project using a Linux tool that enables writing processes to obtain these required results:
If the process is unsuccessful, a negative value is returned.
If the process is successful, 0 value is returned to the child process, and the process ID is sent to the parent process.
Which component results from this operation?
Refer to the exhibit.
An engineer received an event log file to review. Which technology generated the log?
Which filter allows an engineer to filter traffic in Wireshark to further analyze the PCAP file by only showing the traffic for LAN 10.11.x.x, between workstations and servers without the Internet?
Refer to the exhibit.
A company employee is connecting to mail google.com from an endpoint device. The website is loaded but with an error. What is occurring?
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
Which evasion method involves performing actions slower than normal to prevent detection?
A security engineer notices confidential data being exfiltrated to a domain "Ranso4134-mware31-895" address that is attributed to a known advanced persistent threat group The engineer discovers that the activity is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Cyber Kill Chain?
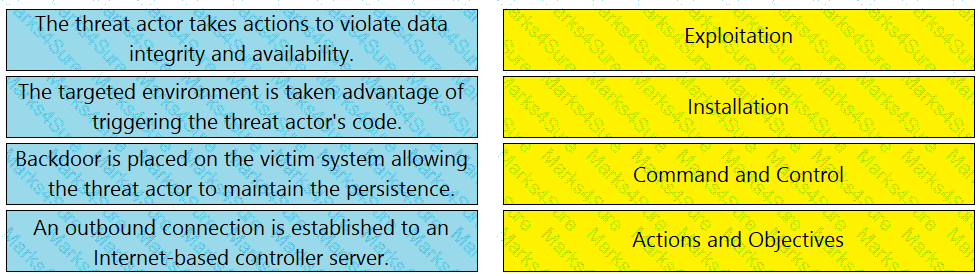
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
The SOC team has confirmed a potential indicator of compromise on an endpoint. The team has narrowed the executable file's type to a new trojan family. According to the NIST Computer Security Incident Handling Guide, what is the next step in handling this event?
A network engineer discovers that a foreign government hacked one of the defense contractors in their home country and stole intellectual property. What is the threat agent in this situation?
Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
Refer to the exhibit. An attacker scanned the server using Nmap. What did the attacker obtain from this scan?