Refer to the exhibit.
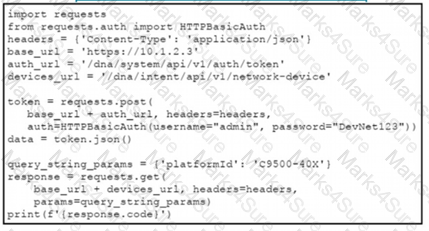
A network engineer must manage the network devices. The engineer prepares a Python scripts to authenticate to the Cisco to DNA Center API and request a device list. The device request fails and returns errors code 401. Which action solves the problem?
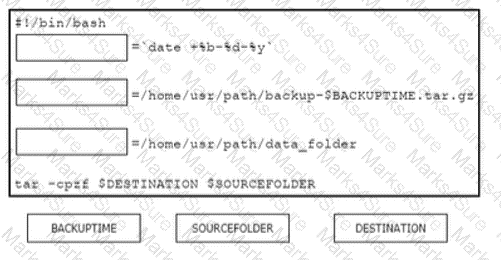
Drag and drop the code from the bottom onto the box where the code is missing in the Bash script to complete the missing assignment.
Refer to the exhibit.
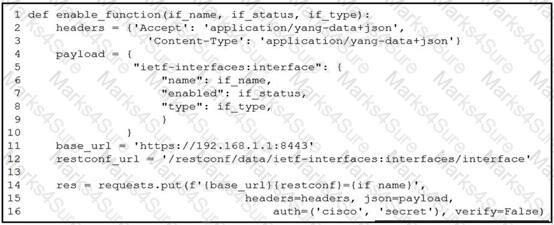
A network engineer wants to automate the port enable/disable process on specific Cisco switches. The engineer creates a script to send a request through RESTCONF and uses ietf as the YANG model and JSON as payload. Which command enables an interface named Loopback1?
A developer creates a script that configured multiple Cisco IOS XE devices in a corporate infrastructure. The internal test environment is unavailable, and no maintenance window is available to test on a low-priority production environment. Which resource is used to test the code before it is applied to the production environment?
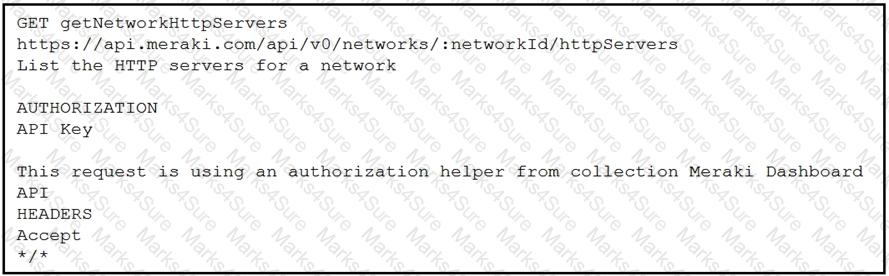
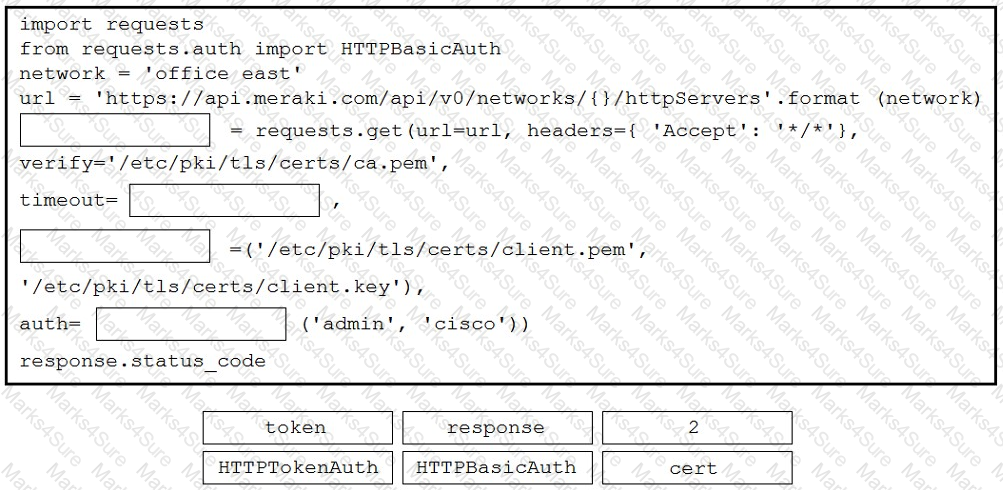
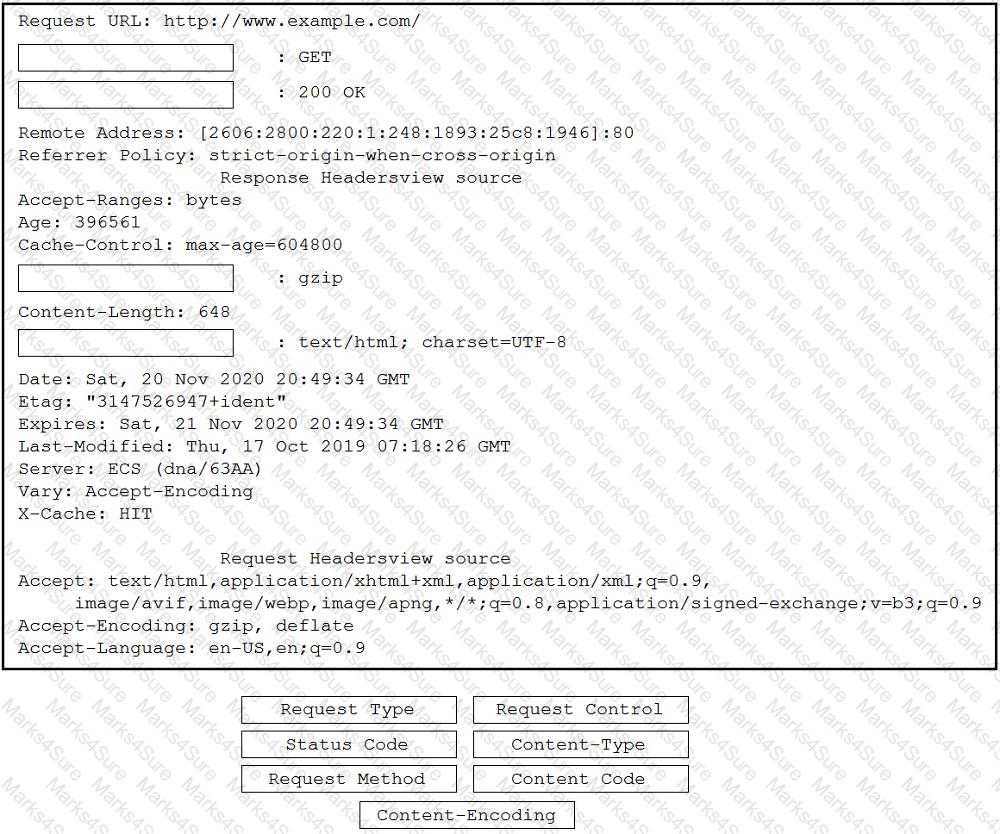
Refer to the exhibit. A developer is creating a Python script to obtain a list of HTTP servers on a network named office_east by using the Cisco Meraki API. The request has these requirements:
• Must time out if the response is not received within 2 seconds.
• Must utilize client certificates and SSL certificate verification.
• Must utilize basic authentication that uses a username of admin and a password of cisco.
• Must save the response to an object named response.
Drag and drop the code snippets from the bottom onto the blanks in the code to meet the requirements. Not all options are used.
A new application is being developed with specific platform requirements. The platform and application deployment and the ongoing platform management must be fully automated. The application includes a large database component that has significant disk I/O requirements. Which application deployment type meets the requirements?
Refer to the exhibit.
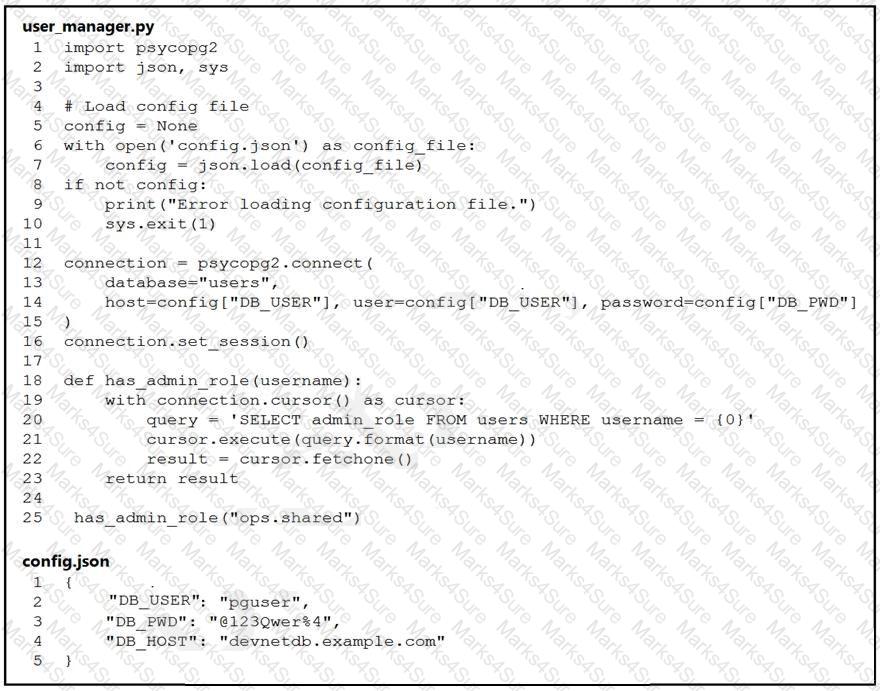
An engineer must check the admin rights of users on a database regularly and prepares
the Python script to automate the process. The script connects to the database and runs a query. What is a security issue about the secrets in the code that relates to secret protection?
A developer needs a list of clients connected to a specific device in a Meraki network. After making a REST API call, the developer receives an unfamiliar response code. Which Cisco DevNet resource should be used to identify the meaning of the response code?
Refer to the exhibit.
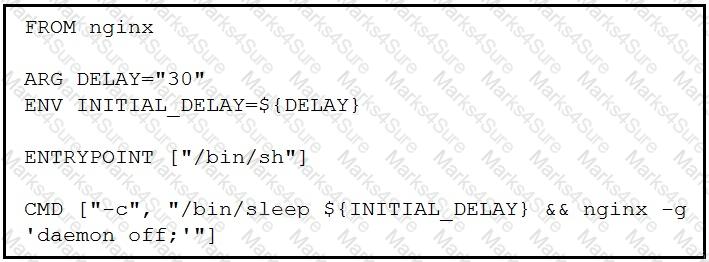
Which command, including arguments, is executed when the container starts?
Refer to the exhibit.
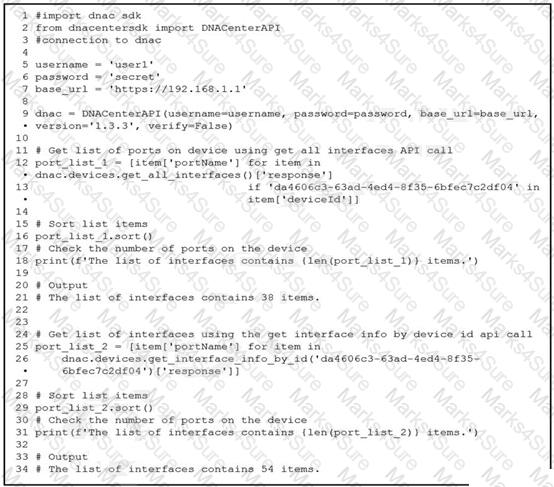
An engineer writes a Python script that uses two different API calls to query Cisco DNA Center for the number of interfaces on a device. The engineer notices that the two API calls produce different results. Why are fewer interfaces returned for the same device when the 'get_all_interfaces' API call is used?
A file that already exists in a local repository is updated. Which command must be executed to ensure that the changes in the file are included in the next Git commit?
Where is an IP packet routed if the packet does not match any routes in the routing table?
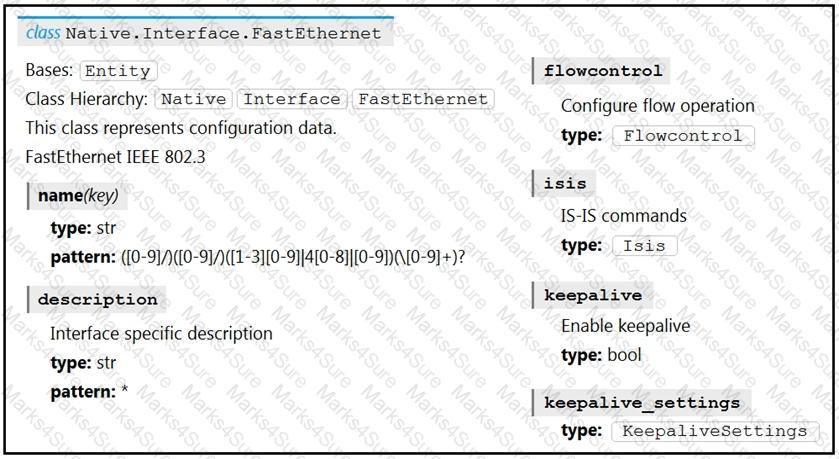
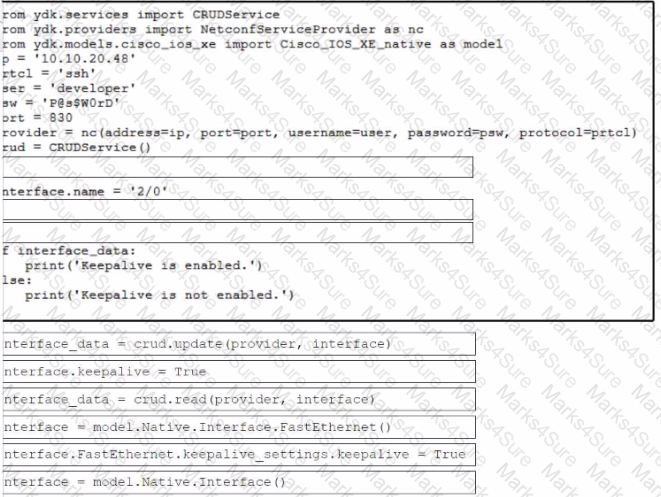
Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used.
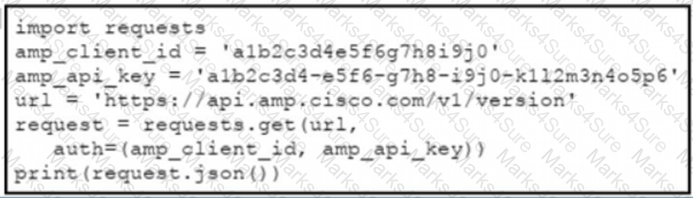
Refer to the exhibit.
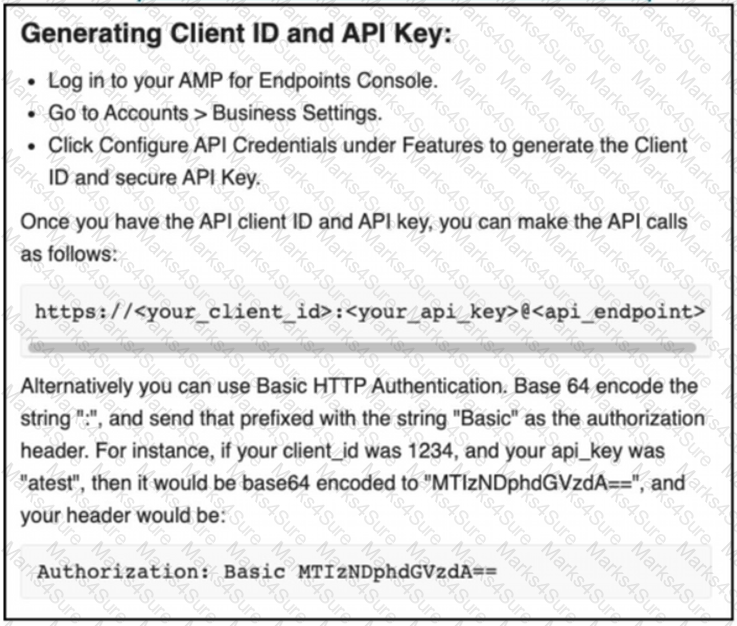
The documentation outlines how to use credentials for the AMP API Which script successfully performs an API call using basic authentication?
A)
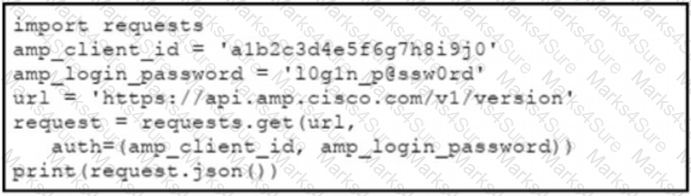
B)

C)
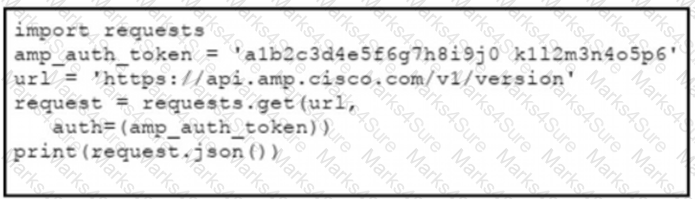
D)
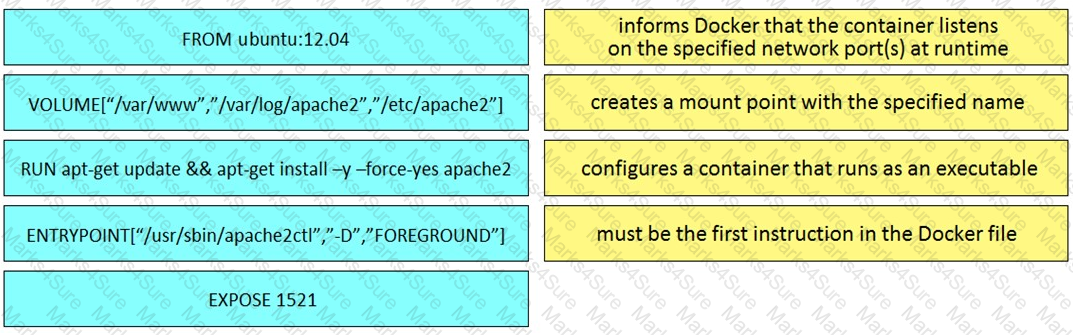
Drag and drop the Dockerfile instructions from the left onto the descriptions on the right. Not at options are used.
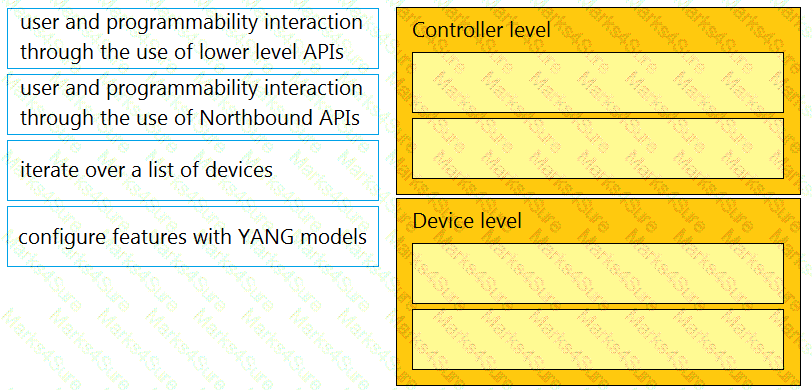
Drag and drop the types of management from the left onto the levels at which they are performed on the right.
Drag and drop the code snippets from the bottom to the blanks in the code to complete the HTTP response. Not all options are used.
Which platform is used to programmatically create a space and invite users for collaboration?
A new application is being developed that must be hardware independent. The application includes an administrative component which is accessed using a Windows desktop GUI. Installation and management of the environment must be fully automated. Which application deployment type meets the requirements?
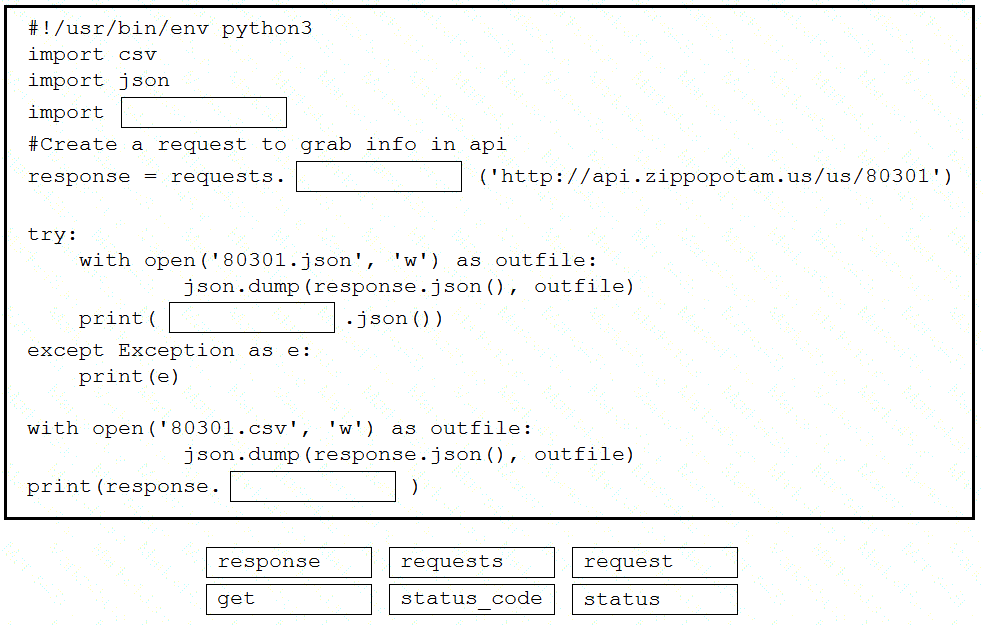
Drag and drop the code snippets from the bottom into the Python script to write API output to a csv file. Not all options are used.
Refer to the exhibit.
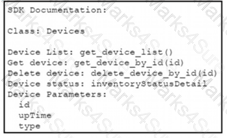
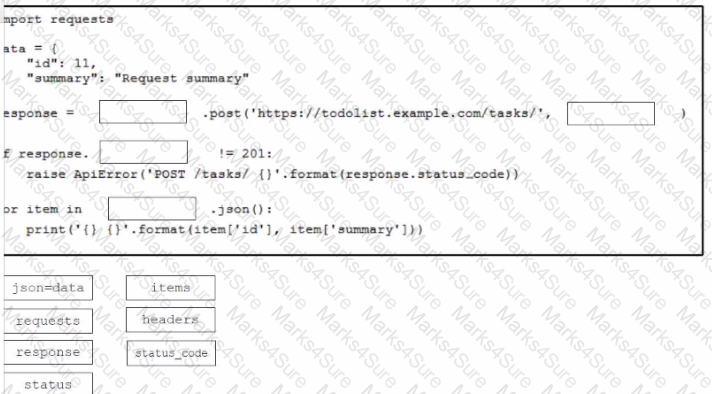
A Python script must delete all Cisco Catayst 9300 Series switches that have an uptime that is greater than 90 days The script must also query for the status of all the other devices Drag and drop the code from the bottom onto the bottom box the code is missing to complete the script Not at options are used

Refer to the exhibit.
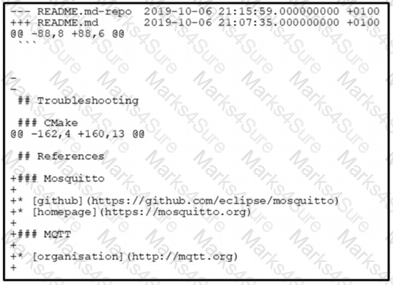
The output of the diff-u README.md-repo README.md command is shown. The original file was 165 lines long How many lines are in the edited copy of the file?
Which protocol must be allowed on the firewall so that NTP services work properly?
Which HTTP response code should be returned when the request is completed, but there is no content to send for the request?
Access to the management interface of devices must be restricted by using SSH and HTTPS. Which two ports must be included in the ACLs for the protocols to work? (Choose two.)
An engineer must configure Cisco Nexus devices and wants to automate this workflow. The engineer enables the Cisco NX-OS REST API to configure the devices by using an Ansible playbook. Before running the code,
which resource must be used to verify that the code works correctly?
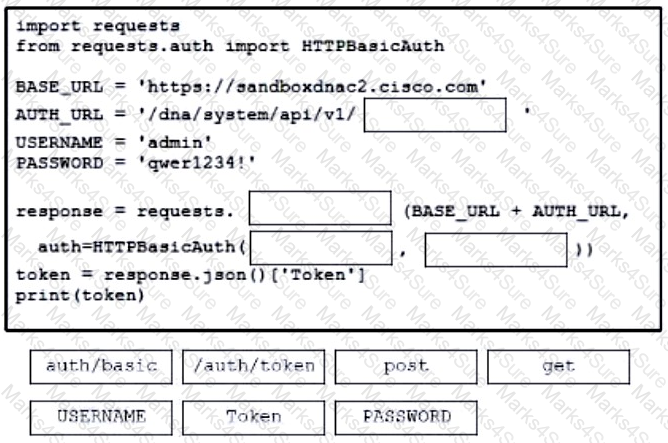
Drag and drop the code from the bottom onto the box where the code is missing to authenticate with the Cisco DNA Center REST API by using basic authentication. Then generate a token for later use. Not all options are used.
How does a developer create and switch to a new branch called "my-bug-fix" to develop a product fix?
What is a capability of model-driven programmability for infrastructure automation?
Refer to the exhibit.
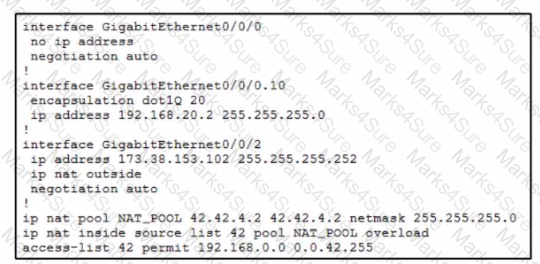
A company recently acquired new IP-based security cameras. After discussion with the engineering team, they decide to segment the security camera traffic m the rest…The engineer assigns the new VLAN 10 for the security camera traffic. After all the devices are configured, it seems as if the cameras cannot access the Internet, .. a few minutes of debugging, the engineer restricts the problem to the router configuration. What is the cause of the issue?
An engineer prepares a set of Python scripts to interact with network devices. To avoid network performance issues, the engineer wants to run them in a test environment. Which resource must be used to monitor the
live execution of code in an always-available environment?
Refer to the exhibit.
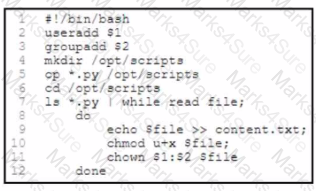
An engineer must add new users and set privileges for executing a few Python scripts. The engineer prepares a Bash script to automate this task. The script ds a user and a group from the command-line arguments, creates a directory, and copies the Python scripts to it. The script then changes to the directory and lists the scripts, used on the script workflow, which process is being automated within the loop by using the list of Python scripts?
What is the purpose of running tests before writing code in test-driven development?
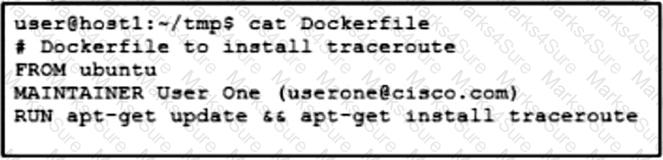
Refer to the exhibit. Drag and drop the Dockerfile contents from the left onto the functions on the right that create a container image to run traceroute to track network path to specific targets. Not all options are used.

During which step of the CI/CD pipeline for infrastructure automation is code from multiple developers combined to compile and test different components?
Refer to the exhibit.
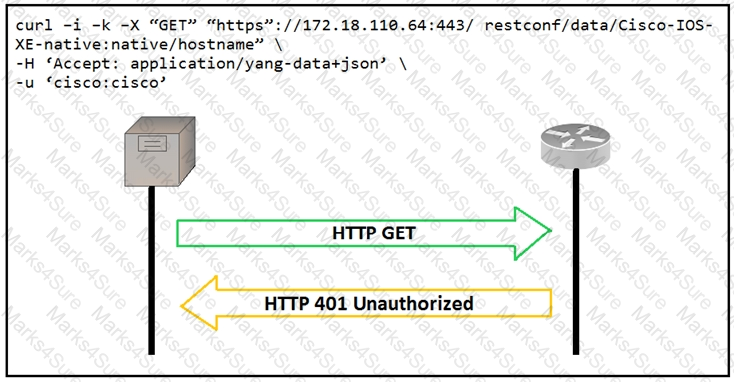
An administrator attempts to perform a GET operation by using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram in the exhibit illustrates the HTTP messages observed. Which change to the API request resolves the issue?
Which IP service is responsible for automatically assigning an IP address to a device?
Which solution reduces costs from MPLS, improves application performance, and simplifies operations?
A company requires a new platform to store large volumes of log data that is generated in their assembly plant. The platform must be scalable, so the underlying technology must provide a path for fast deployment of new nodes for data and indexing? The data contains sensitive information, so specialist encryption tools must be used to secure the data. Which application deployment model meets the requirements?
Refer to the exhibit.
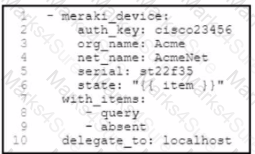
A security team observes an attack that originates from a Cisco Meraki device. To mitigate the attack, the team requests that the engineering team remove the /ice from the network. The security team also requests information about the device, such as Its name and location. Which tool must the engineering team use to meet the luirements by using tasks?
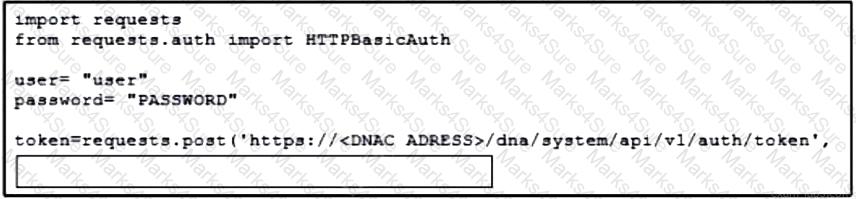
Refer to the exhibit. A developer must use a token to collect data from Cisco DNA Center API and prepares a Python script to send requests. Which line of code needs to be placed on the snippet where the code is missing to obtain a token from the Cisco DNA Center API?
Which network constraint causes the performance of the application to decrease as the number of users accessing the application increases?
Drag and drop the common API styles from the left onto the requirement on the right.
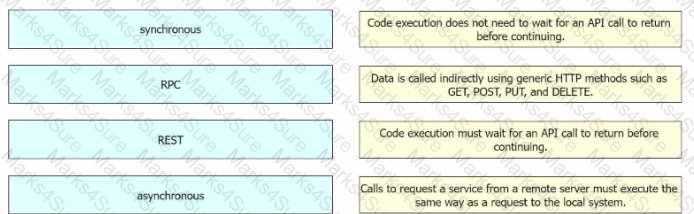
A developer writes an application that refines data in temporary secure file storage hosted on the public cloud. Data will be deleted after processing and does not contain any private information. What is the advantage that a public cloud deployment provides to the developer?
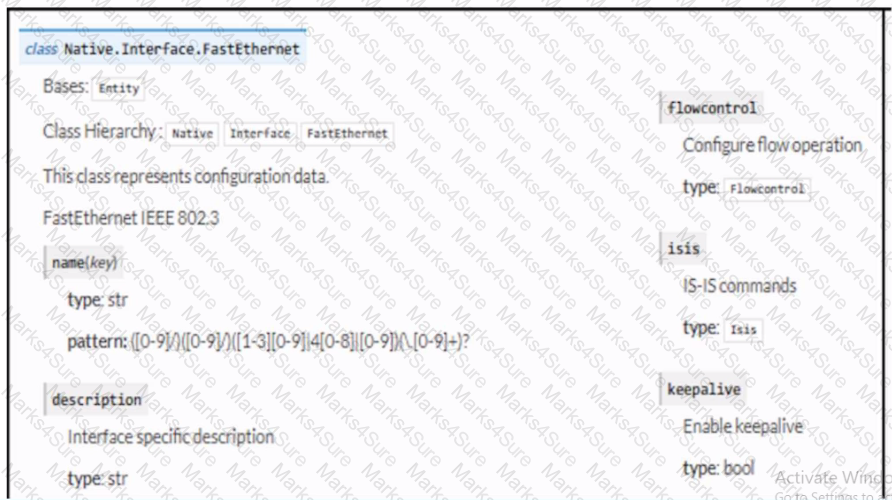
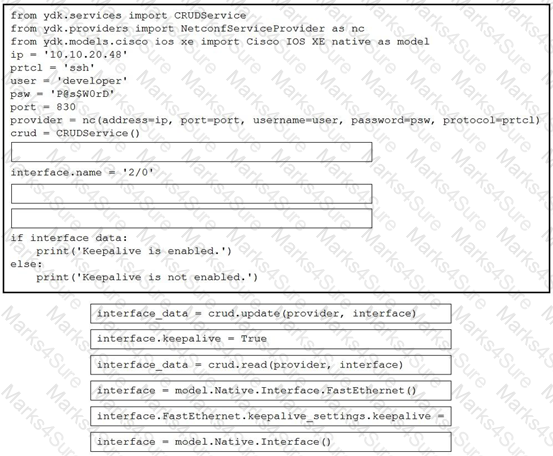
Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used.

Refer to the exhibit. A developer creates a Python script by using the Cisco Meraki API. The solution must:
• Obtain a list of HTTP servers for a network named "netl".
• Print the response body if the HTTP status code is 200.
• Handle the timeout requests as exceptions, and print Timeout Error next to the exception to stdout.
Which block of code completes the script?
A)
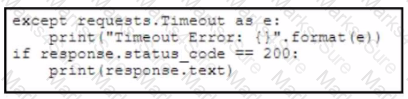
B)
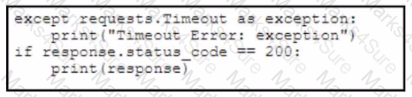
A developer plans to deploy a new application that will use an API to implement automated data collection from Webex with these requirements:
The application was created by using the request library.
Requires HTTP basic authentication.
Provides data in JSON or XML formats.
Which Cisco DevNet resource helps the developer with how to use the API?
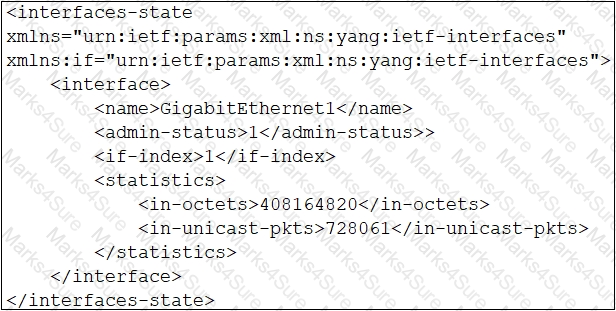
Refer to the exhibit.
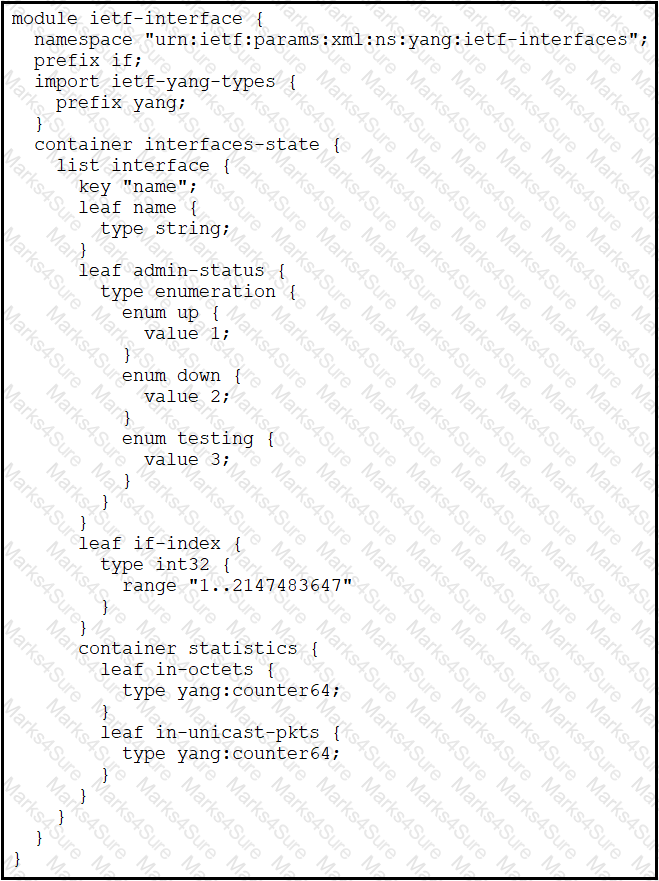
Which XML snippet has interface information that conforms to the YANG model?
A)
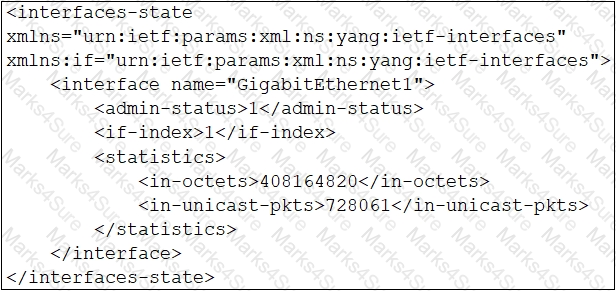
B)
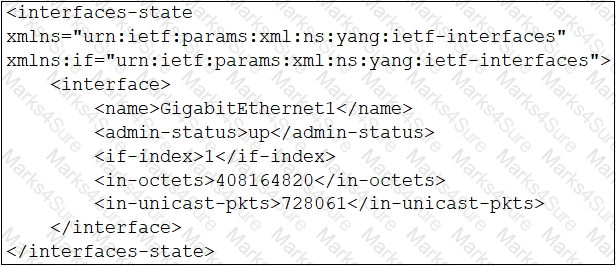
C)
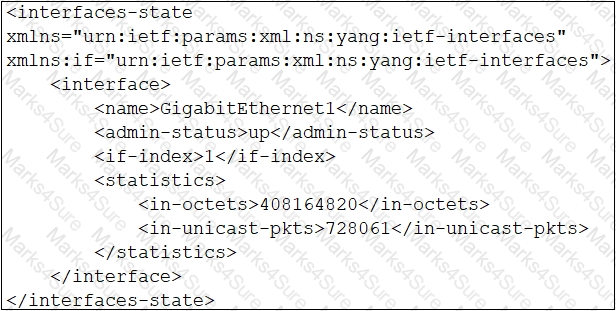
D)
An engineer needs to retrieve a list of locally available Firepower Threat Defense upgrade packages by using the Firepower Management Center REST API. The engineer uses a GET request with the URL:
/api/fmc_platform/v1/updates/upgradepackages/f413afeb-e6f6-75f4-9169-6d9bd49s625e
What does “f413afeb-e6f6-75f4-9169-6d9bd49s625e” represent?
Refer to the exhibit. An engineer is comparing two files by using the unified diff format. Which cade snippet belongs to the new.py file?
A developer checks the performance of a web application. The application is in the local data center and uses a REST-based API. Based on the API logs, it is discovered that many its abandon API requests. Also, the response is taking too long to get back. What is the reason for this issue?
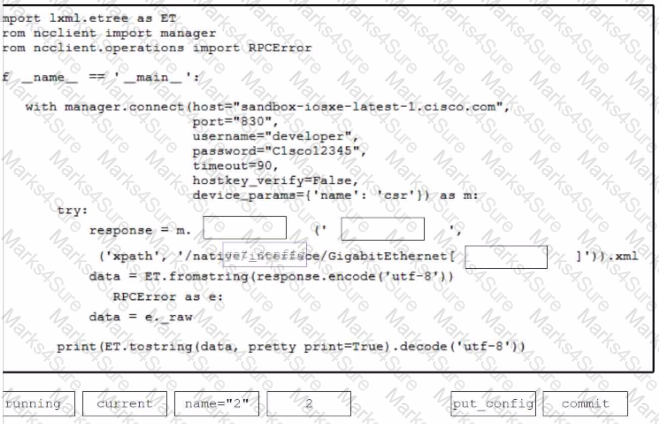
Drag and drop the code from the bottom onto the box where the code is missing to present GigabilEthernet2 details in the XML format. Not all options are used.

Refer to the exhibit. A network engineer makes a RESTCONF API call to Cisco IOS XE to retrieve information. Which HTTP method and URL does the engineer use to make the ..call?
A)

B)

C)

D)

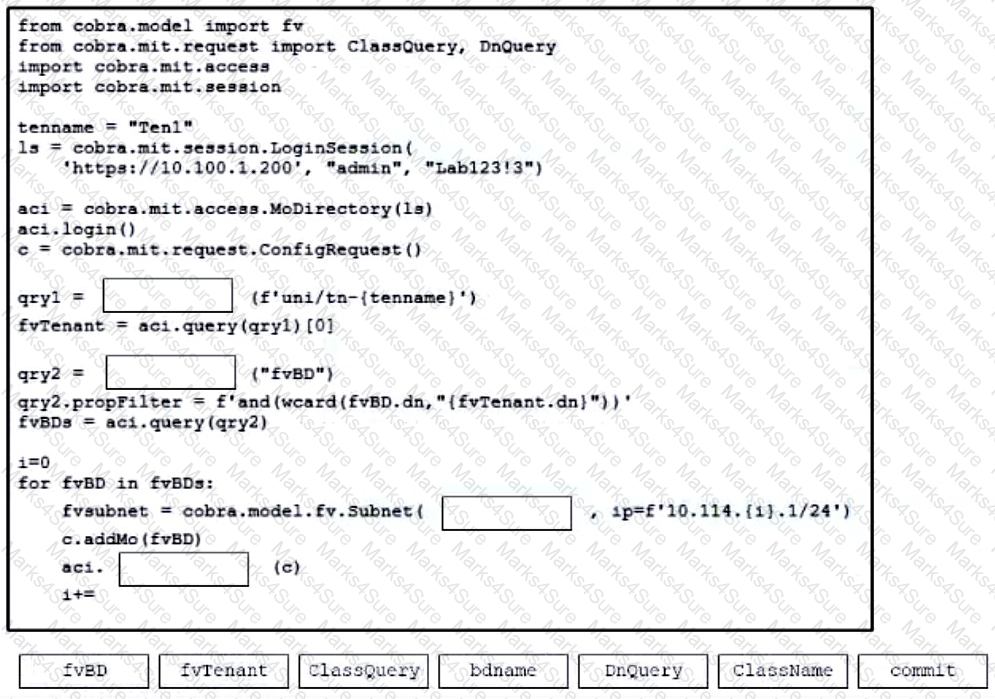
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to add a subnet to each bridge domain in the Ten1 tenant. Not all options are used.
Drag and drop the code from the bottom onto the box where the code is missing to enable ports on a switch by using RESTCONF. Not all options are used.

Which technology is responsible for matching a name to an IP address of an application running on a host?
When a Cisco IOS XE networking device is configured by using RESTCONF, what is the default data encoding method?
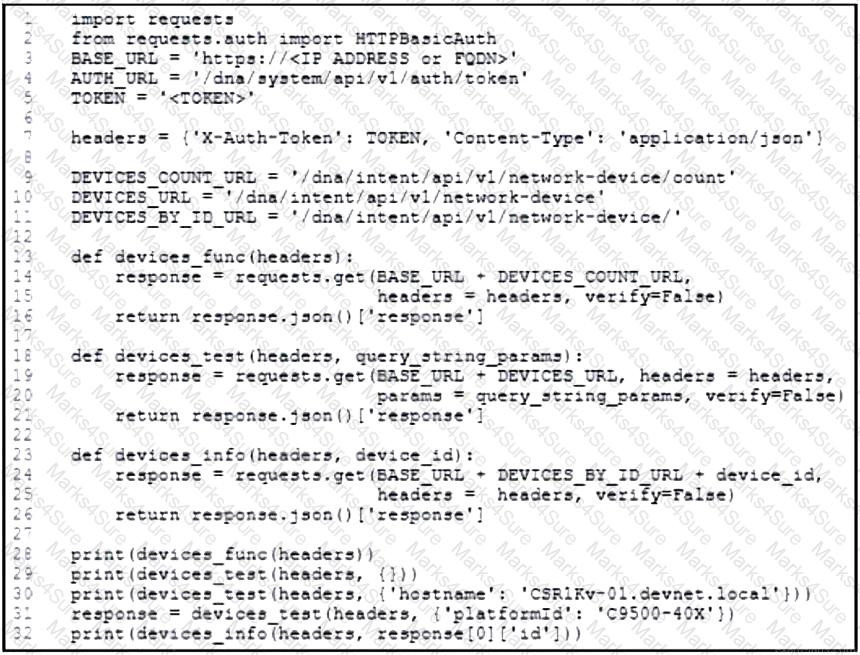
Refer to the exhibit. An engineer prepares a script to automate workflow by using Cisco DNA Center APIs to display:
total count of devices
list of the network devices
information of one device with a hostname filter
What is displayed in the final step after the Python script is executed?
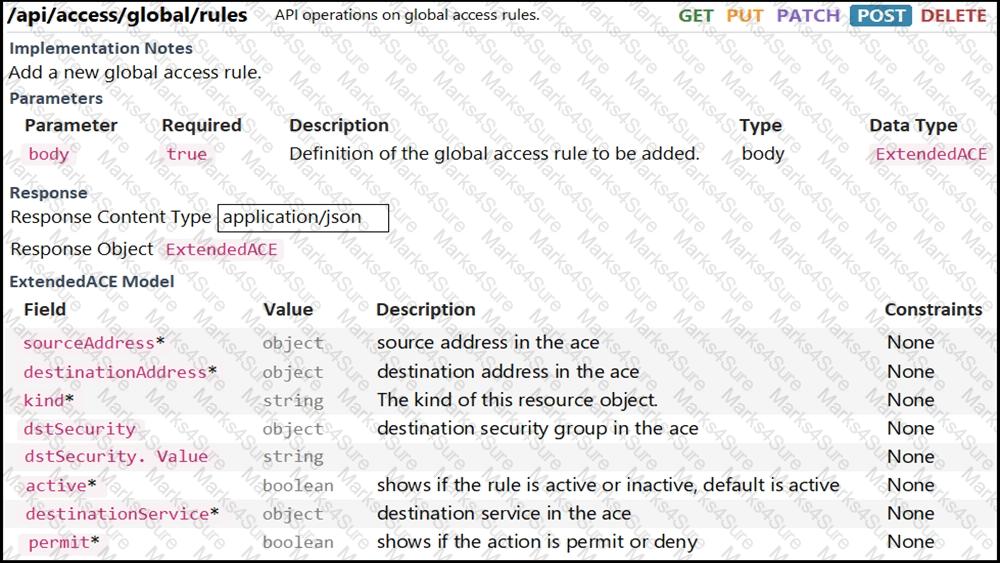
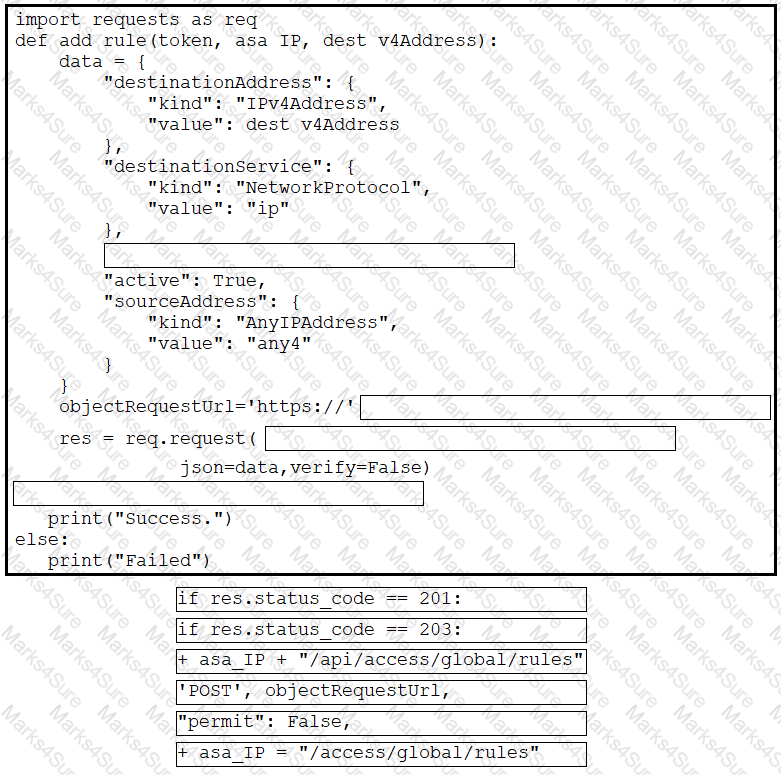
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to complete the function that adds a new global access rule that denies traffic using the Cisco ASA REST API. Not all options are used.
An engineer clones a repository that contains a Python script from GitLab to a laptop. After modifying the code, the engineer wants to validate the changes. Which command starts … CI/CD pipeline and runs the automated tests?
Which platform has an API that has the capability to obtain a list of vulnerable software on user devices?
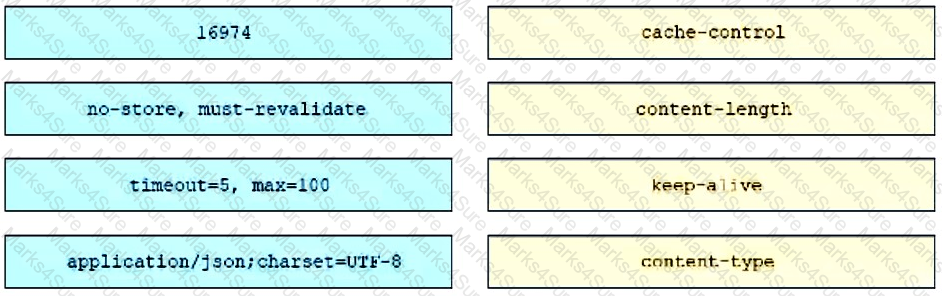
An engineer must make changes on a network device through the management platform API. The engineer prepares a script to send the request and analyze the response, check headers, and read the body according to information inside response headers. Drag and drop the HTTP header values from the left onto the elements of an HTTP response on the right.
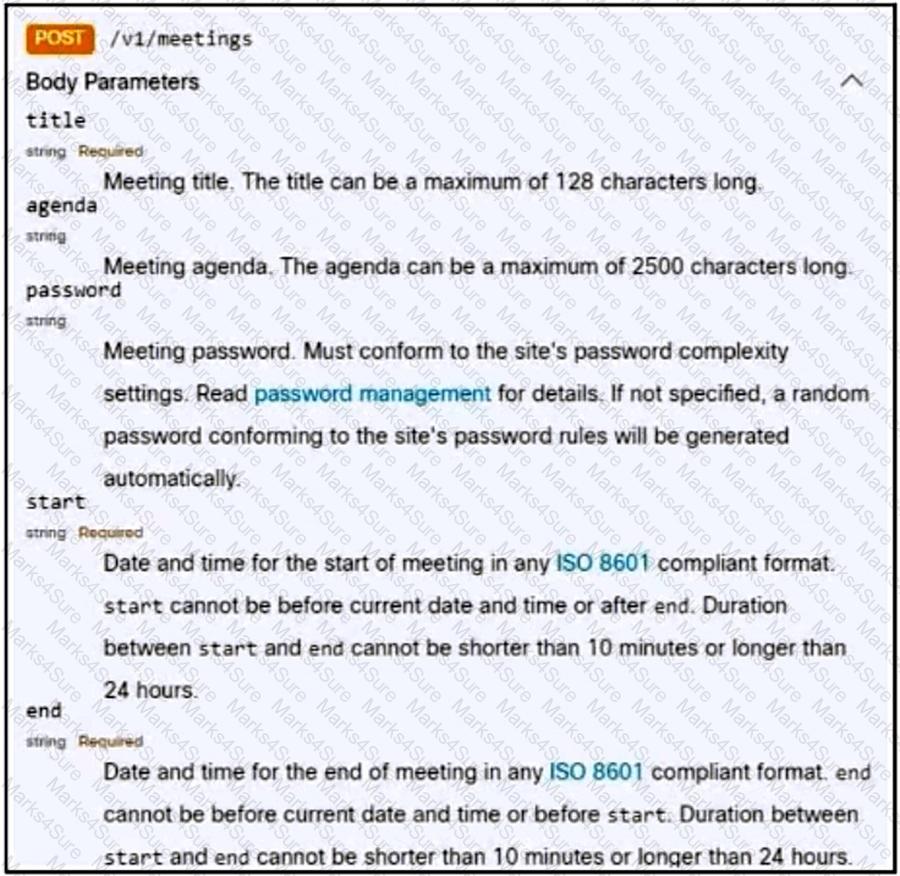
Refer to the exhibit. A bespoke meeting booking system must be integrated with Cisco Webex so that meetings are created automatically. Drag and drop the code from the bottom onto the box where the code is missing to create a sample meeting. Not all options are used.

Refer to the exhibit.
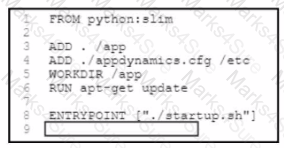
A developer needs to create a Docker image that listens on port 5000. Which code snippet must be placed onto the blank in the code?
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
Which Python function is used to parse a string that contains JSON data into a Python dictionary?
Which RFC 1918 address space includes a subnet of 172.16.0.0 that uses a mask of 255.255.0.0?
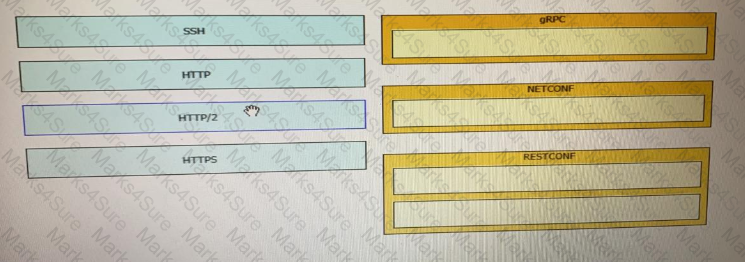
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right.
Refer to the exhibit.

A REST API retune this JSON output for a GET HTTP request, Which has assigned to a variable called “vegetables” Using python, which output is the result of this command?
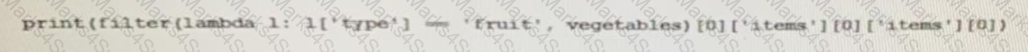
A small company has 5 servers and 50 clients. What are two reasons an engineer should spilt this network into separate client and server subnets? (Choose two)
Refer to the exhibit.
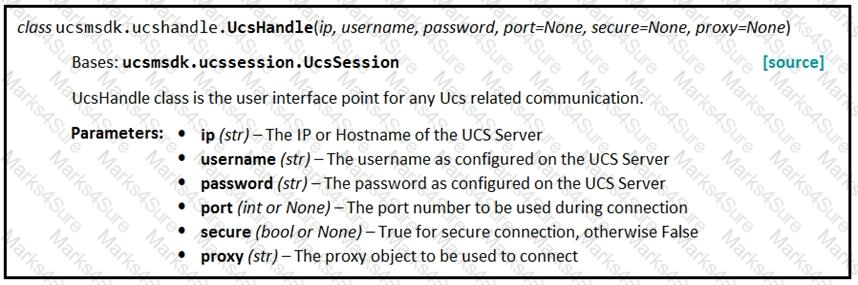
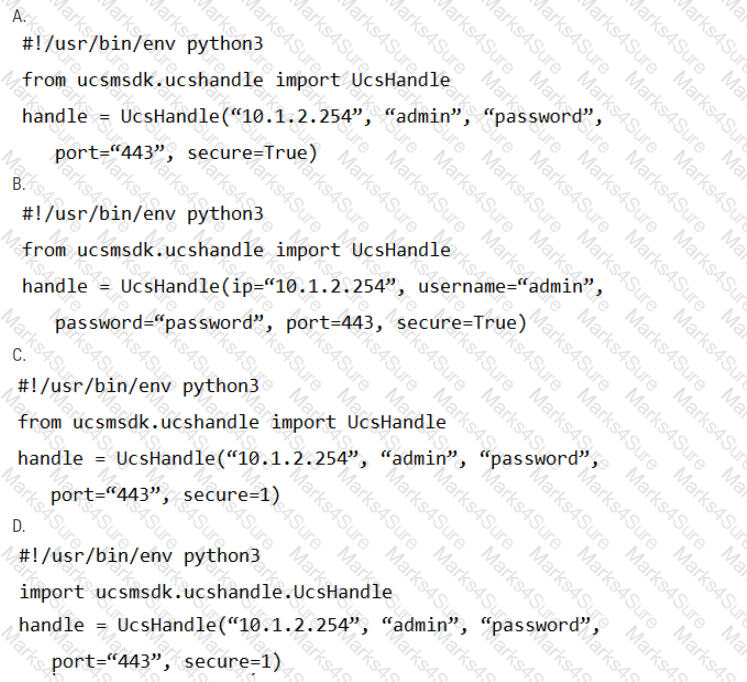
Given the API documentation for the UCS SDK python class, UcsHandle, which code snippet creates a handle instance?
Which network device monitors incoming and outgoing traffic and decides whether to allow or block specific traffic based on a defined set of rules?
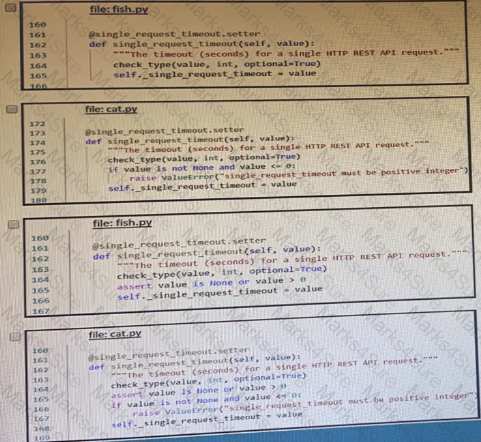
Refer to the exhibit.

The output of a unified diff when comparing two versions of a python script is shown. Which two “single_request _timeout ()”
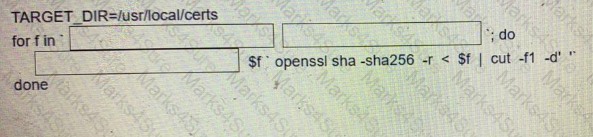
Fill in the blanks to complete the Bash script in which each file in a directory is renamed to Its SHA256 hash?
Drag and drop the Python code from the left onto the correct step on the right to call a REST API.

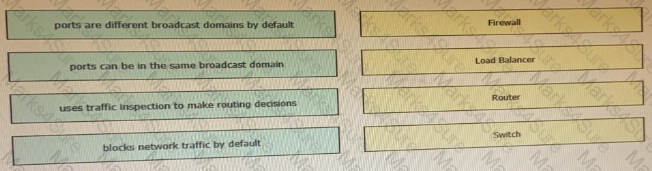
Drag and drop the functionalities from the left onto correct networking devices on the right.
Refer to the exhibit.
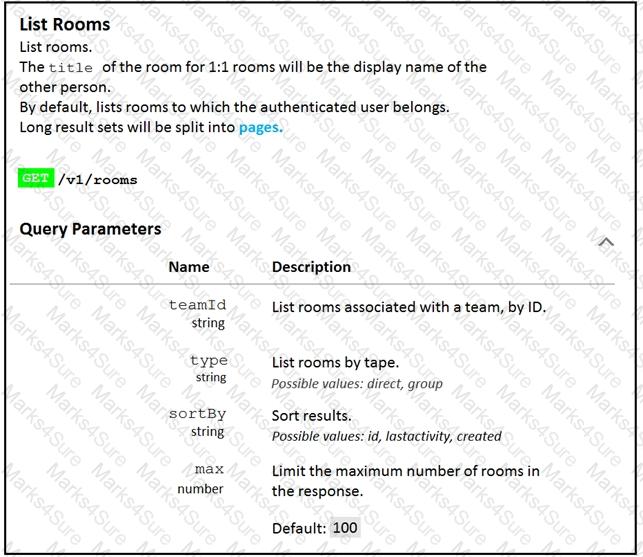
Fill in the blank to complete the query parameter and value so that the result set is returned in reverse chronological order (most recent first) based on when message were entered.

Which two statements describe the traits of an asynchronous API call? (Choose two.)
Refer to the exhibit.
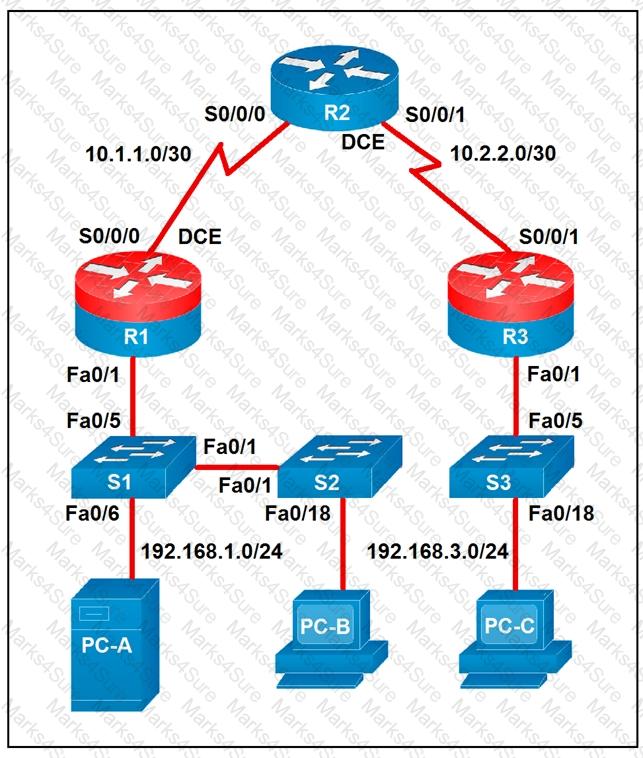
Which two statements about the network diagram are true? (Choose two.)
Which CI/CD tool is an automation tool used to build, test, and deploy software?
Drag and drop elements of the RESTCONF protocol stack from the left onto the correct description on the right. Not all elements on the left are used.

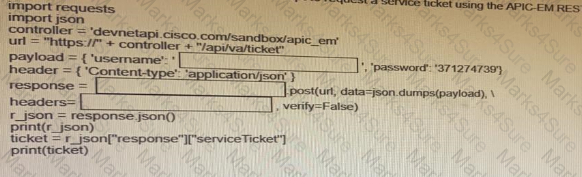
Fill in the blanks to complete the python script to request a service ticket using the APIC-EM rest API for the user “devnetuser”.
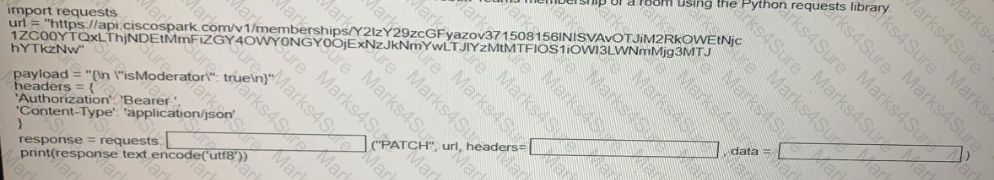
Fill in the blanks to complete the Python script to update the Webex Teams membership of a room using the Python requests library import requests
Which two statements describe the advantages of using a version control system? (Choose two.)
A developer needs to prepare the file README.md in the working tree for the next commit operation using Git. Which command needs to be used to accomplish this?
The project is migrated to a new codebase, the “old_project” directory must be deleted. The directory has multiple read-only files, and it must be deleted recursively without prompting for confirmation. Which bash command must be used?
Refer to the exhibit.
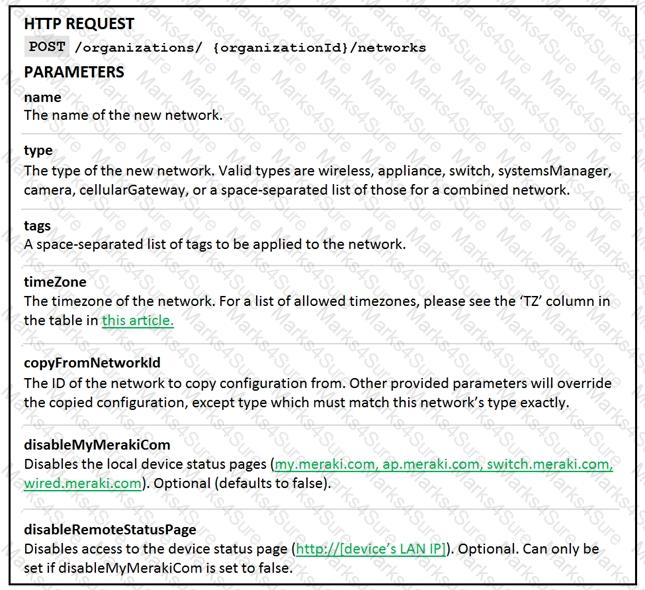
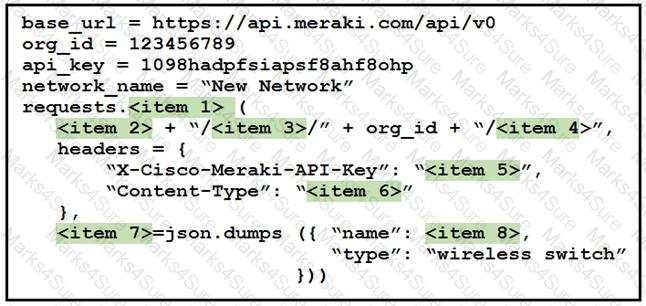
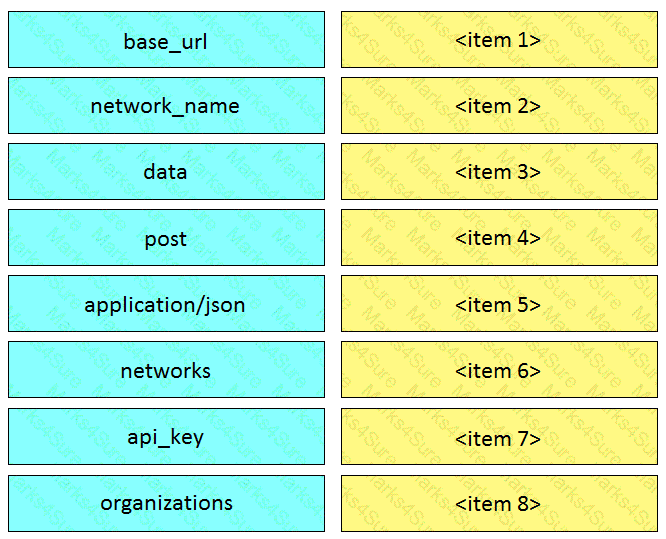
Drag and drop the code from the left onto the item numbers on the right to complete to Meraki python script shown in the exhibit.
How does requesting a synchronous API operation differ from requesting an asynchronous API operation?
Which platform has an API that be used to obtain a list of vulnerable software on user devices?
Refer to the exhibit.
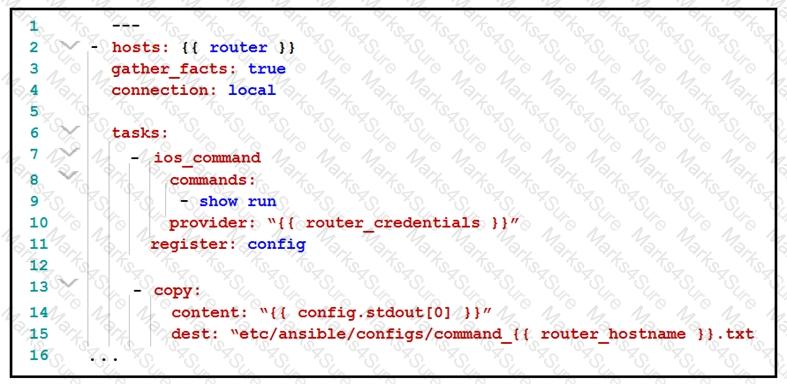
What is the effect of this Ansible playbook on an IOS router?
A developer is reviewing a code that was written by a colleague. It runs fine, but there are many lines of code to do a seemingly simple task repeatedly. Which action organizes the code?
Refer to the exhibit.
A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
Which two statements are true about Cisco UCS manager, Cisco Intersight APIs? (Choose two.)
Which status code is used by a REST API to indicate that the submitted payload is incorrect?
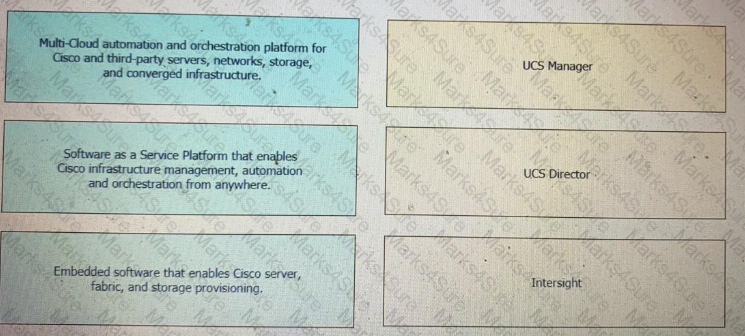
Drag and drop the capability on the left onto the Cisco compute management platform that supports the capability on the right.
Which two statement describe the role of an artifact repository in a CI/CD pipeline? (Choose two.)
A REST API service requires authentication based on the username and password. The user “john” has the password “384279060” and the Base64 encoding of those credentials is “am9objowMTIzNDU2Nzg=”. Which method completes an authentication request?
Which response status code is used by a RESTful interface to indicate successful execution of a request?
In python, which expression checks whether the script returns a success status code when the Requests library is used?