A user attempts to open some files, but a message appears stating that the files are encrypted. The user was able to access these files before without receiving this message and no changes have been made within the company. Which of the following has infected the computer?
A change advisory board did not approve a requested change due to the lack of alternative actions if implementation failed. Which of the following should be updated before requesting approval again?
A user contacted the help desk to report pop-ups on a company workstation indicating the computer has been infected with 137 viruses and payment is needed to remove them. The user thought the company-provided antivirus software would prevent this issue. The help desk ticket states that the user only receives these messages when first opening the web browser. Which of the following steps would MOST likely resolve the issue? (Select TWO)
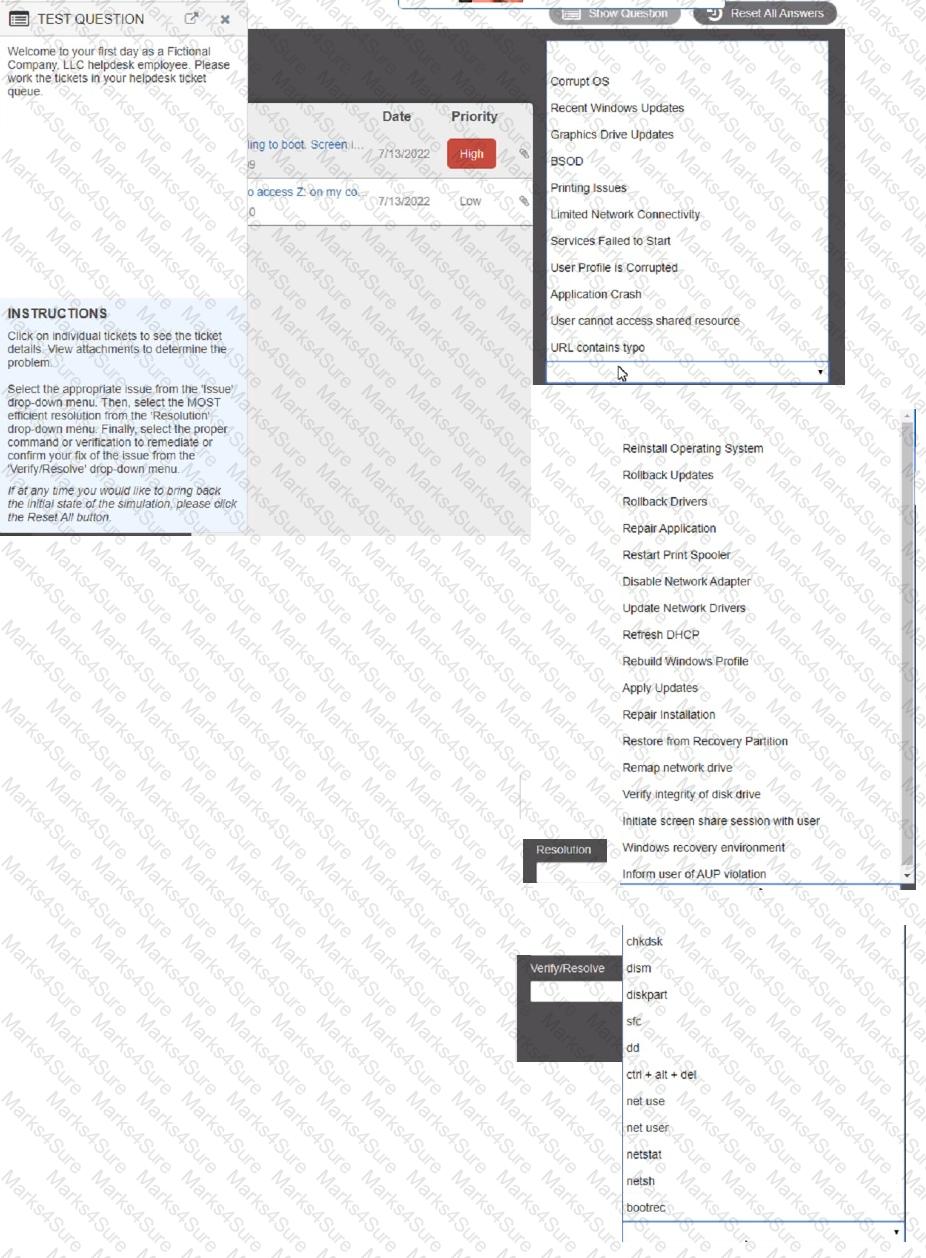
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.
Which of the following could be used to implement secure physical access to a data center?
An Android user contacts the help desk because a company smartphone failed to complete a tethered OS update A technician determines there are no error messages on the device Which of the following should the technician do NEXT?
The command cac cor.ptia. txt was issued on a Linux terminal. Which of the following results should be expected?
An organization is centralizing support functions and requires the ability to support a remote user's desktop. Which of the following technologies will allow a technician to see the issue along with the user?
A company needs to securely dispose of data stored on optical discs. Which of the following is the MOST effective method to accomplish this task?
A technician needs to recommend the best backup method that will mitigate ransomware attacks. Only a few files are regularly modified, however, storage space is a concern. Which of the following backup methods would BEST address these concerns?
A user enabled a mobile device's screen lock function with pattern unlock. The user is concerned someone could access the mobile device by repeatedly attempting random patterns to unlock the device. Which of the following features BEST addresses the user's concern?
Which of the following is the MOST cost-effective version of Windows 10 that allows remote access through Remote Desktop?
Ann, a CEO, has purchased a new consumer-class tablet for personal use, but she is unable to connect it to the company’s wireless network. All the corporate laptops are connecting without issue. She has asked you to assist with getting the device online.
INSTRUCTIONS
Review the network diagrams and device configurations to determine the cause of the problem and resolve any discovered issues.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
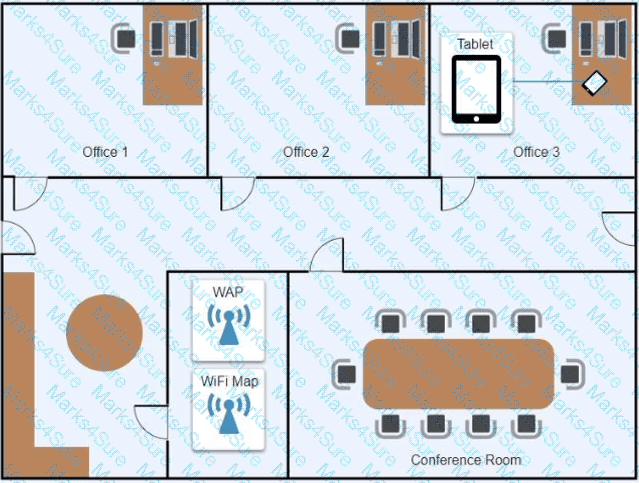
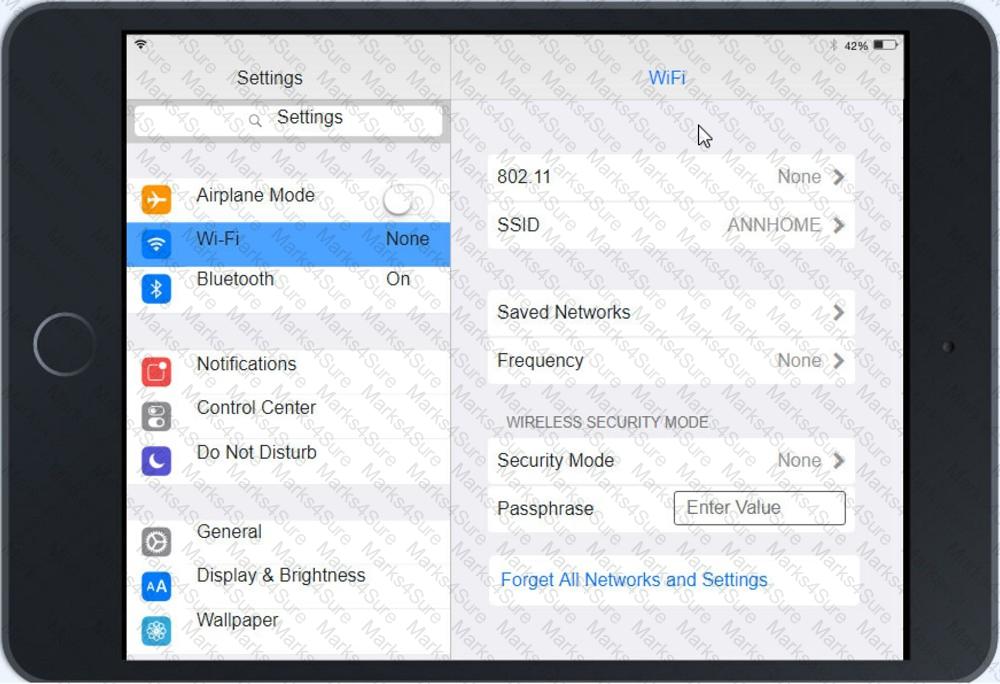
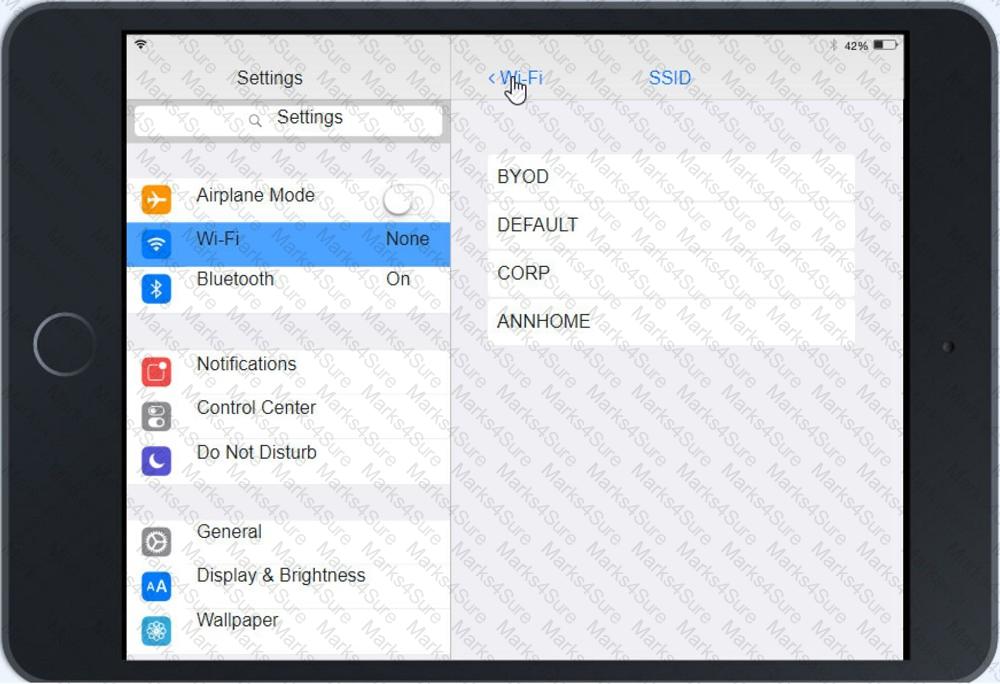
A technician is investigating an employee's smartphone that has the following symptoms
• The device is hot even when it is not in use.
•Applications crash, especially when others are launched.
• Certain applications, such as GPS, are in portrait mode when they should be in landscape mode.
Which of the following can the technician do to MOST likely resolve these issues with minimal impact? (Select TWO).
A user reports that antivirus software indicates a computer is infected with viruses. The user thinks this happened white browsing the internet. The technician does not recognize the interface with which the antivirus message is presented. Which of the following is the NEXT step the technician should take?
A technician is setting up a SOHO wireless router. The router is about ten years old. The customer would like the most secure wireless network possible. Which of the following should the technician configure?
A company wants to remove information from past users' hard drives in order to reuse the hard drives Witch of the following is the MOST secure method
A user is experiencing frequent malware symptoms on a Windows workstation. The user has tried several times to roll back the state but the malware persists. Which of the following would MOST likely resolve the issue?
A user reports that a workstation is operating sluggishly Several other users operate on the same workstation and have reported that the workstation is operating normally. The systems administrator has validated that the workstation functions normally. Which of the following steps should the systems administrator most likely attempt NEXT?
A technician is unable to join a Windows 10 laptop to a domain Which of the following is the MOST likely reason?
A user corrects a laptop that is running Windows 10 to a docking station with external monitors when working at a desk. The user would like to close the laptop when it is docked, but the user reports it goes to sleep when it is closed. Which of the following is the BEST solution to prevent the laptop from going to sleep when it is closed and on the docking station?
A user reports that the hard drive activity light on a Windows 10 desktop computer has been steadily lit for more than an hour, and performance is severely degraded. Which of the following tabs in Task Manager would contain the information a technician would use to identify the cause of this issue?
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
Click on individual tickers to see the ticket details. View attachments to determine the problem.
Select the appropriate issue from the 'issue' drop-down menu. Then, select the MOST efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.
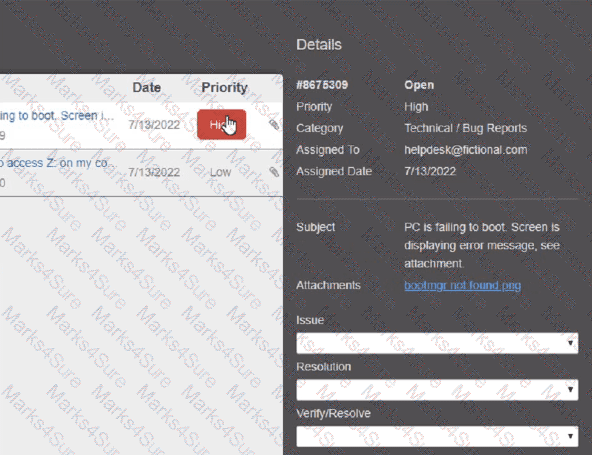
A change advisory board just approved a change request. Which of the following is the MOST likely next step in the change process?
A company using Active Directory wants to change the location of all users' "Documents" to a file server on the network. Which of the following should the company set up to accomplish this task?
A technician suspects a rootkit has been installed and needs to be removed. Which of the following would BEST resolve the issue?
A user wants to set up speech recognition on a PC. In which of the following Windows Settings tools can the user enable this option?
A technician is doing a bare-metal installation of the Windows 10 operating system. Which of the following prerequisites must be in place before the technician can start the installation process?
An organization wants to deploy a customizable operating system. Which of the following should the organization choose?
A company was recently attacked by ransomware. The IT department has remediated the threat and determined that the attack method used was email. Which of the following is the most effective way to prevent this issue from reoccurring?
A customer, whose smartphone's screen was recently repaired, reports that the device has no internet access through Wi-Fi. The device shows that it is connected to Wi-Fi, has an address of 192.168.1.42. and has no subnet mask. Which of the following should the technician check next?
A customer service representative is unable to send jobs to a printer at a remote branch office. However, the representative can print successfully to a local network printer. Which of the following commands should a technician use to view the path of the network traffic from the PC?
A network administrator is setting up the security for a SOHO wireless network. Which of the following options should the administrator enable to secure the network?
A PC is taking a long time to boot Which of the following operations would be best to do to resolve the issue at a minimal expense? (Select two).
A user connected an external hard drive but is unable to see it as a destination to save files. Which of the following tools will allow the drive to be formatted?
A user called the help desk lo report an Issue with the internet connection speed on a laptop. The technician thinks that background services may be using extra bandwidth. Which of the following tools should the technician use to investigate connections on the laptop?
A technician needs to ensure that USB devices are not suspended by the operating system Which of the following Control Panel utilities should the technician use to configure the setting?
A salesperson's computer is unable to print any orders on a local printer that is connected to the computer Which of the following tools should the salesperson use to restart the print spooler?
A user reports an issue when connecting a mobile device to Bluetooth. The user states the mobile device's Bluetooth is turned on. Which of the following steps should the technician take NEXT to resolve the issue?
A remote user is having issues accessing an online share. Which of the following tools would MOST likely be used to troubleshoot the Issue?
A desktop technician has received reports that a user's PC is slow to load programs and saved files. The technician investigates and discovers an older HDD with adequate free space. Which of the following should the technician use to alleviate the issue first?
A user installed a new computer game. Upon starting the game, the user notices the frame rates are low. Which of the following should the user upgrade to resolve the issue?
A technician has been tasked with troubleshooting audiovisual issues in a conference room. The meeting presenters are unable to play a video with sound. The following error is received:
The Audio Driver is not running.
Which of the following will MOST likely resolve the issue?
A user reported that a laptop's screen turns off very quickly after silting for a few moments and is also very dim when not plugged in to an outlet Everything else seems to be functioning normally. Which of the following Windows settings should be configured?
A technician is troubleshooting a customer's PC and receives a phone call. The technician does not take the call and sets the phone to silent. Which of the following BEST describes the technician's actions?
In which of the following scenarios would remote wipe capabilities MOST likely be used? (Select TWO).
A user's system is infected with malware. A technician updates the anti-malware software and runs a scan that removes the malware. After the user reboots the system, it once again becomes infected with malware. Which of the following will MOST likely help to permanently remove the malware?
A user is attempting to browse the internet using Internet Explorer. When trying to load a familiar web page, the user is unexpectedly redirected to an unfamiliar website. Which of the following would MOST likely solve the issue?
A macOS user needs to create another virtual desktop space. Which of the following applications will allow the user to accomplish this task?
A user is being directed by the help desk to look up a Windows PC's network name so the help desk can use a remote administration tool to assist the user. Which of the following commands would allow the user to give the technician the correct information? (Select TWO).
A user in a corporate office reports the inability to connect to any network drives. No other users have reported this issue. Which of the following is the MOST likely reason the user is having this issue?
Before leaving work, a user wants to see the traffic conditions for the commute home. Which of the following tools can the user employ to schedule the browser to automatically launch a traffic website at 4:45 p.m.?
An administrator has received approval for a change request for an upcoming server deployment. Which of the following steps should be completed NEXT?
A user receives a notification indicating the data plan on the user's corporate phone has reached its limit. The user has also noted the performance of the phone is abnormally slow. A technician discovers a third-party GPS application was installed on the phone. Which of the following is the MOST likely cause?
A junior administrator is responsible for deploying software to a large group of computers in an organization. The administrator finds a script on a popular coding website to automate this distribution but does not understand the scripting language. Which of the following BEST describes the risks in running this script?
Sensitive data was leaked from a user's smartphone. A technician discovered an unapproved application was installed, and the user has full access to the device's command shell. Which of the following is the NEXT step the technician should take to find the cause of the leaked data?
A systems administrator needs to reset a users password because the user forgot it. The systems administrator creates the new password and wants to further protect the user's account Which of the following should the systems administrator do?
A technician has just used an anti-malware removal tool to resolve a user's malware issue on a corporate laptop. Which of the following BEST describes what the technician should do before returning the laptop to the user?
A user reports a workstation has been performing strangely after a suspicious email was opened on it earlier in the week. Which of the following should the technician perform FIRST?
Which of the following file extensions are commonly used to install applications on a macOS machine? (Select THREE).
A user calls the help desk and reports a workstation is infected with malicious software. Which of the following tools should the help desk technician use to remove the malicious software? (Select TWO).
Security software was accidentally uninstalled from all servers in the environment. After requesting the same version of the software be reinstalled, the security analyst learns that a change request will need to be filled out. Which of the following is the BEST reason to follow the change management process in this scenario?
A technician is setting up a backup method on a workstation that only requires two sets of tapes to restore. Which of the following would BEST accomplish this task?
A Windows user reported that a pop-up indicated a security issue. During inspection, an antivirus system identified malware from a recent download, but it was unable to remove the malware. Which of the following actions would be BEST to remove the malware while also preserving the user's files?
A Microsoft Windows PC needs to be set up for a user at a targe corporation. The user will need access to the corporate domain to access email and shared drives. Which of the following versions of Windows would a technician MOST likely deploy for the user?
A suite of security applications was installed a few days ago on a user's home computer. The user reports that the
computer has been running slowly since the installation. The user notices the hard drive activity light is constantly solid. Which of the following should be checked FIRST?
A user is setting up a computer for the first time and would like to create a secondary login with permissions that are different than the primary login. The secondary login will need to be protected from certain content such as games and websites. Which of the following Windows settings should the user utilize to create the secondary login?
A user turns on a new laptop and attempts to log in to specialized software, but receives a message stating that the address is already in use. The user logs on to the old desktop and receives the same message. A technician checks the account and sees a comment that the user requires a specifically allocated address before connecting to the software. Which of the following should the technician do to MOST likely resolve the issue?
A technician downloaded software from the Internet that required the technician to scroll through a text box and at the end of the text box, click a
button labeled Accept Which of the following agreements IS MOST likely in use?
An organization's Chief Financial Officer (CFO) is concerned about losing access to very sensitive, legacy unmaintained PII on a workstation if a
ransomware outbreak occurs. The CFO has a regulatory requirement to retain this data for many years. Which of the following backup methods
would BEST meet the requirements?
A company has just refreshed several desktop PCs. The hard drives contain PII. Which of the following is the BEST method to dispose of the drives?
A user has a license for an application that is in use on a personal home laptop. The user approaches a systems administrator about using the same license on
multiple computers on the corporate network. Which of the following BEST describes what the systems administrator should tell the user?
A call center handles inquiries into billing issues for multiple medical facilities. A security analyst notices that call center agents often walk away from their workstations, leaving patient data visible for anyone to see. Which of the following should a network administrator do to BEST prevent data theft within the call center?
A bank would like to enhance building security in order to prevent vehicles from driving into the building while also maintaining easy access for customers. Which of the following BEST addresses this need?
A police officer often leaves a workstation for several minutes at a time. Which of the following is the BEST way the officer can secure the workstation quickly when walking away?
Which of the following is a data security standard for protecting credit cards?
While browsing a website, a staff member received a message that the website could not be trusted. Shortly afterward, several other colleagues reported the same issue across numerous other websites. Remote users who were not connected to corporate resources did not have any issues. Which of the following is MOST likely the cause of this issue?
A new spam gateway was recently deployed at a small business However; users still occasionally receive spam. The management team is concerned that users will open the messages and potentially
infect the network systems. Which of the following is the MOST effective method for dealing with this Issue?
Following the latest Windows update PDF files are opening in Microsoft Edge instead of Adobe Reader. Which of the following utilities should be used to ensure all PDF files open in Adobe Reader?
A technician received a call stating that all files in a user's documents folder appear to be Changed, and each of the files now has a look file
extension Which pf the following actions is the FIRST step the technician should take?
A user reports that text on the screen is too small. The user would like to make the text larger and easier to see. Which of the following is the BEST way for the user to increase the size of text, applications, and other items using the Windows 10 Settings tool?
A desktop specialist needs to prepare a laptop running Windows 10 for a newly hired employee. Which of the following methods should the technician use to refresh the laptop?
An Android user reports that when attempting to open the company's proprietary mobile application it immediately doses. The user states that the issue persists, even after rebooting the phone. The application contains critical information that cannot be lost. Which of the following steps should a systems administrator attempt FIRST?
A user purchased a netbook that has a web-based, proprietary operating system. Which of the following operating systems is MOST likely installed on the netbook?
A technician needs to transfer a large number of files over an unreliable connection. The technician should be able to resume the process if the connection is interrupted. Which of the following tools can be used?
The network was breached over the weekend System logs indicate that a single user's account was successfully breached after 500 attempts with a dictionary attack. Which of the following would BEST mitigate this threat?
A technician at a customer site is troubleshooting a laptop A software update needs to be downloaded but the company's proxy is blocking traffic to the update site. Which of the following should the technician perform?
A technician wants to enable BitLocker on a Windows 10 laptop and is unable to find the BitLocker Drive Encryption menu item in Control Panel. Which of the following explains why the technician unable to find this menu item?
Which of the following features can a technician use to ensure users are following password length requirements?
A user received an alert from a Windows computer indicating low storage space. Which of the following will best resolve this issue?
A technician needs to troubleshoot a user's computer while the user is connected to the system. The technician must also connect to the user's system using remote access tools built in to Windows Which of the following is the best option to troubleshoot the user's computer?
While browsing the internet, a customer sees a window stating antivirus protection is no longer functioning Which of the following steps should a technician take next? (Select two).
A technician needs to upgrade a legacy system running on a 32-bit OS with new applications that can work both on a 32-bit and a 64-bit system. The legacy system is critically important to the organization. The IT manager cautions that the new applications must not have a detrimental effect on company finances. Which of the following impacts is the IT manager most concerned with?
A technician needs to configure a computer for a user to work from home so the user can still securely access the user’s shared files and corporate email. Which of the following tools would best accomplish this task*?
A user’s Windows 10 workstation with an HDD is running really slowly. The user has opened, closed, and saved many large files over the past week. Which of the following tools should a technician use to remediate the issue?
A user clicked a link in an email, and now the cursor is moving around on its own. A technician notices that File Explorer is open and data is being copied from the local drive to an unknown cloud storage location. Which of the following should the technician do first?
A technician is following the ticketing system’s best practices when handling user support requests. Which of the following should the technician do first when responding to a user support request that contains insufficient information?
A user is unable to start a computer following a failed Windows 10 update. When trying to start the computer, the user sees a blue screen of death. Which of the following steps should a technician take to diagnose the issue?
A technician is troubleshooting a PC that is unable to perform DNS lookups. Utilizing the following firewall output:
Protocol/PortActionDirection
1 AllowOut
445 BlockOut
53 BlockOut
123 BlockOut
80 BlockOut
Which of the following ports should be opened to allow for DNS recursion?
A technician is setting up a new PC in a SOHO. Which of the following should the technician most likely configure on the PC?
An employee has been using the same password for multiple applications and websites for the past several years. Which of the following would be best to prevent security issues?
A technician is installing software on a user's workstation. The installation fails due to incompliance with the HCL. Which of the following components is most likely causing the installation to fail? (Select two).
A user is experiencing the following issues with Bluetooth on a smartphone:
•The user cannot hear any sound from a speaker paired with the smartphone.
•The user is having issues synchronizing data from their smart watch, which is also connected via Bluetooth.
A technician checked the Bluetooth settings, confirmed it is successfully paired with a speaker, and adjusted the volume levels, but still could not hear anything. Which of the following steps should the technician take next to troubleshoot the Bluetooth issues?
Which of the following Linux commands would help to identify which directory the user is currently operating in?
An employee using an Apple MacBook is receiving frequent, random pop-up requests from other Apple devices wanting to share photos and videos and asking whether the user would like to accept the request Which of the following configurations should the technician advise the user to change first"?
A technician is troubleshooting a Windows system that is having issues with the OS loading at startup. Which of the following should the technician do to diagnose the issue?
A technician wants to improve password security after several users admitted to using very simple passwords. Which of the following is the best way to resolve this issue?
Which of the following operating systems was the app file type designed to run under as an application file bundle?
When a user attempts to open an email using a company-issued smartphone, the user receives a message stating the email is encrypted and cannot be opened. The user forwards the email to a personal account and receives the same message. The user then contacts the IT department for assistance. The technician instructs the user to contact the sender to exchange information in order to decode the message. Which of the following will the user receive from the sender?
A developer reports that a workstation's database file extensions have been changed from .db to .enc. The developer is also unable to open the database files manually. Which of the following is the best option for recovering the data?
Accessing a restore point
A technician requires graphical remote access to various Windows, Linux, and macOS desktops on the company LAN. The security administrator asks the technician to utilize a single software solution that does not require an external internet connection. Which of the following remote access tools is the technician most likely to install?
After a security event, a technician removes malware from an affected laptop and disconnects the laptop from the network. Which of the following should the technician do to prevent the operating system from automatically returning to an infected state?
Which of the following Windows 10 editions is the most appropriate for a single user who wants to encrypt a hard drive with BitLocker?
Which of the following filesystems replaced FAT as the preferred filesystem for Microsoft Windows OS?
Which of the following is the best way to limit the loss of confidential data if an employee's company smartphone is lost or stolen?
Which of the following is the most likely to use NTFS as the native filesystem?
Which of the following should be documented to ensure that the change management plan is followed?
A remote user's smartphone is performing very slowly. The user notices that the performance improves slightly after rebooting but then reverts back to performing slowly. The user also notices that the phone does not get any faster after connecting to the company's corporate guest network. A technician sees that the phone has a large number of applications installed on it. Which of the following is the most likely cause of the issue?
A technician successfully removed malicious software from an infected computer after running updates and scheduled scans to mitigate future risks. Which of the following should the technician do next?
Which of the following involves sending arbitrary characters in a web page request?
A laptop that was in the evidence room of a police station is missing. Which of the following is the best reason to refer to chain of custody documentation?
A branch office suspects a machine contains ransomware. Which of the following mitigation steps should a technician take first?
A user's iPhone was permanently locked after several failed log-in attempts. Which of the following authentication methods are needed to restore access, applications, and data to the device?
When visiting a particular website, a user receives a message stating, "Your connection is not private." Which of the following describes this issue?
Malware is installed on a device after a user clicks on a link in a suspicious email. Which of the following is the best way to remove the malware?
A large organization is researching proprietary software with vendor support for a multiuser environment. Which of the following EULA types should be selected?
Which of the following statements describes the purpose of scripting languages?
To access the hardware of the computer it is running on
A technician is hardening a company file server and needs to prevent unauthorized LAN devices from accessing stored files. Which of the following should the technician use?
A technician has verified a computer is infected with malware. The technician isolates the system and updates the anti-malware software. Which of the following should the technician do next?
A user's Windows computer seems to work well at the beginning of the day. However, its performance degrades throughout the day, and the system freezes when several applications are open. Which of the following should a technician do to resolve the issue? (Select two).
Install the latest GPU drivers.
A customer calls desktop support and begins yelling at a technician. The customer claims to have submitted a support ticket two hours ago and complains that the issue still has not been resolved. Which of the following describes how the technician should respond?
Place the customer on hold until the customer calms down.
Which of the following commands can a technician use to get the MAC address of a Linux distribution?
net use
An employee has repeatedly contacted a technician about malware infecting a work computer. The technician has removed the malware several times, but the user's PC keeps getting infected. Which of the following should the technician do to reduce the risk of future infections?
A corporate smartphone was stored for five months after setup. During this time, the company did not have any system updates. When the phone is turned on, an application runs, but it crashes intermittently. Which of the following should a technician do next?
Restart the phone.
A computer technician is investigating a computer that is not booting. The user reports that the computer was working prior to shutting it down last night. The technician notices a removable USB device is inserted, and the user explains the device is a prize the user received in the mail yesterday. Which of the following types of attacks does this describe?
Which of the following would typically require the most computing resources from the host computer?
Chrome OS
Which of the following environments allows for the testing of critical systems without the risk of them being negatively impacted by changes?
An office is experiencing constant connection attempts to the corporate Wi-Fi. Which of the following should be disabled to mitigate connection attempts?
SSID
A technician has verified that a user's computer has a virus and the antivirus software is out of date. Which of the following steps should the technician take next?
A user reports seeing random, seemingly non-malicious advertisement notifications in the Windows 10 Action Center. The notifications indicate the advertisements are coming from a web browser. Which of the following is the best solution for a technician to implement?
The calendar application on an employee's smartphone is experiencing frequent crashes, and the smartphone has become unresponsive. Which of the following should a technician do first to resolve the issue?
A company-owned mobile device is displaying a high number of ads, receiving data-usage limit notifications, and experiencing slow response. After checking the device, a technician notices the device has been jailbroken. Which of the following should the technician do next?
A technician wants to mitigate unauthorized data access if a computer is lost or stolen. Which of the following features should the technician enable?
A user reports that an air-gapped computer may have been infected with a virus after the user transferred files from a USB drive. The technician runs a computer scan with Windows Defender but does not find an infection. Which of the following actions should the technician take next? (Select two).
A user's computer unexpectedly shut down immediately after the user plugged in a USB headset. Once the user turned the computer back on, everything was functioning properly, including the headset. Which of the following Microsoft tools would most likely be used to determine the root cause?
A remote user contacts the help desk about an email that appears to be distorted. The technician is unsure what the user means and needs to view the email to assist with troubleshooting. Which of the following should the technician use to assist the user?
A neighbor successfully connected to a user's Wi-Fi network. Which of the following should the user do after changing the network configuration to prevent the neighbor from being able to connect again?
A technician needs to transfer a file to a user's workstation. Which of the following would BEST accomplish this task utilizing the workstation's built-in protocols?
A kiosk, which is running Microsoft Windows 10, relies exclusively on a numeric keypad to allow customers to enter their ticket numbers but no other information. If the kiosk is idle for four hours, the login screen locks. Which of the following sign-on options would allow any employee the ability to unlock the kiosk?
A technician needs to add an individual as a local administrator on a Windows home PC. Which of the following utilities would the technician MOST likely use?
A user calls the help desk to report that Windows installed updates on a laptop and rebooted overnight. When the laptop started up again, the touchpad was no longer working. The technician thinks the software that controls the touchpad might be the issue. Which of the following tools should the technician use to make adjustments?
A company needs employees who work remotely to have secure access to the corporate intranet. Which of the following should the company implement?
Which of the following is used to integrate Linux servers and desktops into Windows Active Directory environments?
A technician is in the process of installing a new hard drive on a server but is called away to another task. The drive has been unpackaged and left on a desk. Which of the following should the technician perform before leaving?
A user needs assistance changing the desktop wallpaper on a Windows 10 computer. Which of the following methods will enable the user to change the wallpaper using a Windows 10 Settings tool?
A user notices a small USB drive is attached to the user's computer after a new vendor visited the office. The technician notices two files named grabber.exe and output.txt. Which of the following attacks is MOST likely occurring?
A user receives a call from someone who claims to be from the user's bank and requests information to ensure the user's account is safe. Which of the following social-engineering attacks is the user experiencing?
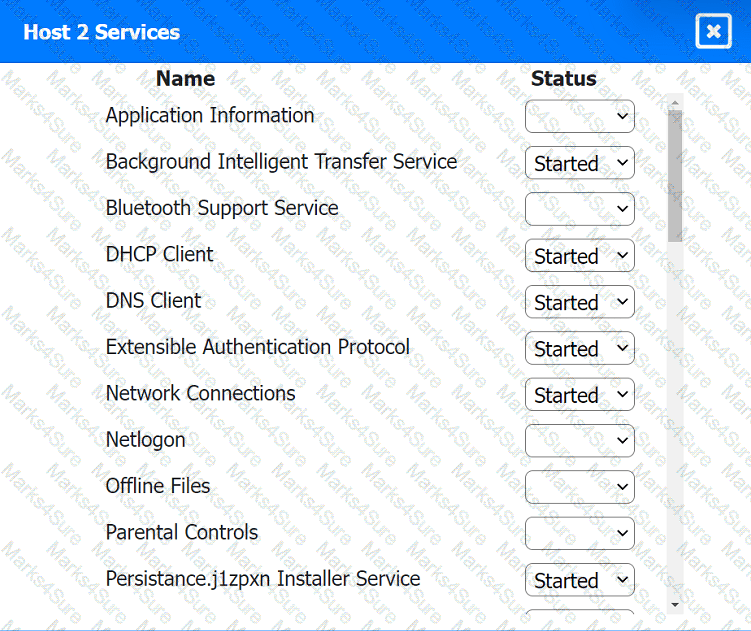
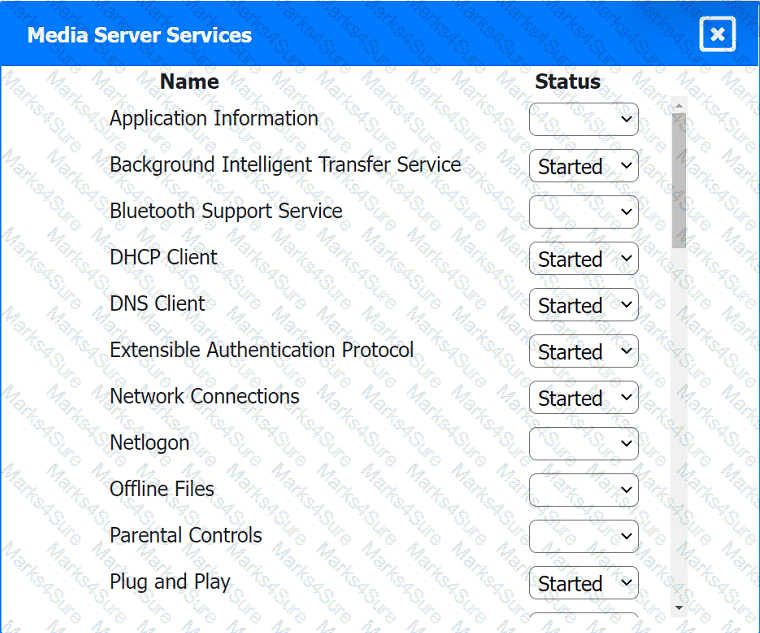
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users' audio issues are
resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.
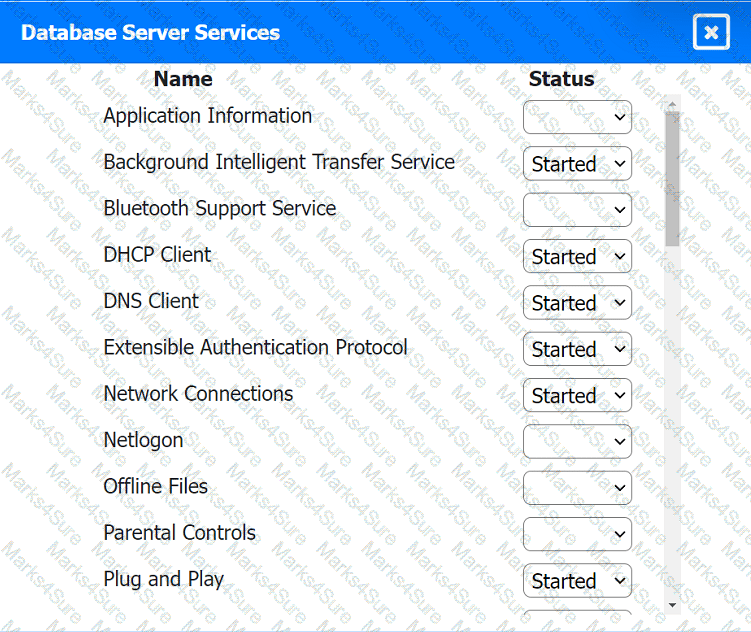
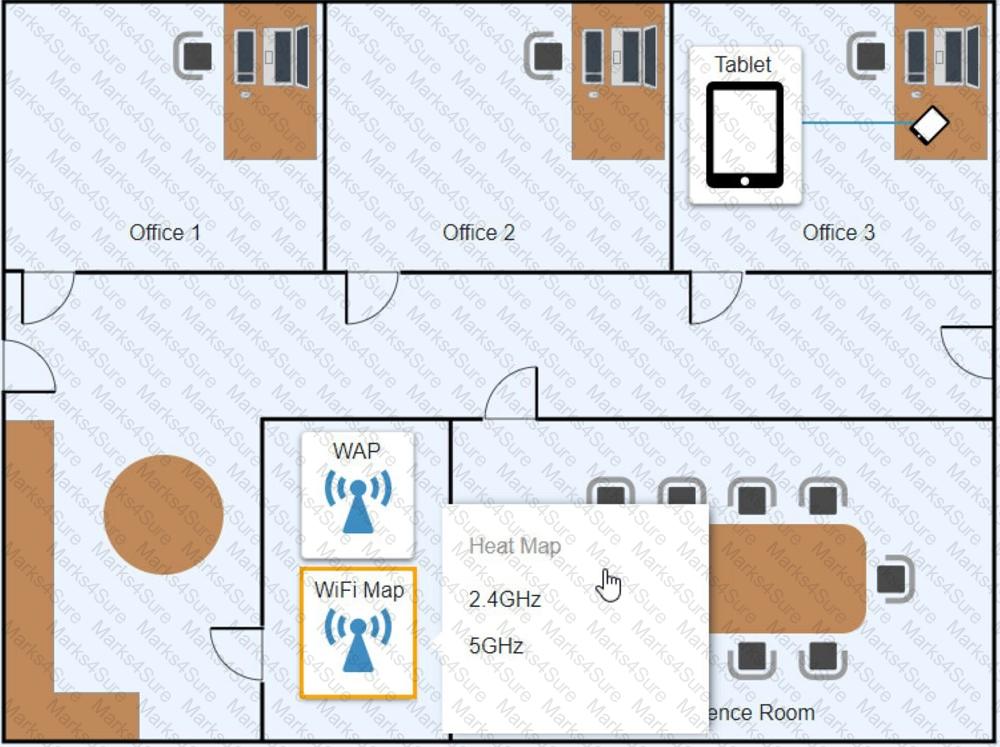
A technician needs to implement a system to handle both authentication and authorization. Which of the following meets this requirement?
A company uses shared drives as part of a workforce collaboration process. To ensure the correct access permissions, inheritance at the top-level folder is assigned to each department. A manager's team is working on confidential material and wants to ensure only the immediate team can view a specific folder and its subsequent files and subfolders. Which of the following actions should the technician most likely take?
A company installed WAPs and deployed new laptops and docking stations to all employees. The docking stations are connected via LAN cables. Users are now reporting degraded network service. The IT department has determined that the WAP mesh network is experiencing a higher than anticipated amount of traffic. Which of the following would be the most efficient way to ensure the wireless network can support the expected number of wireless users?
All the desktop icons on a user's newly issued PC are very large. The user reports that the PC was working fine until a recent software patch was deployed. Which of the following would BEST resolve the issue?
A company acquired a local office, and a technician is attempting to join the machines at the office to the local domain. The technician notes that the domain join option appears to be missing. Which of the following editions of Windows is MOST likely installed on the machines?
A user reports being unable to access a sports team's website on an office computer. The administrator tells the user this blocked access is intentional and based on company guidelines. Which of the following is the administrator referring to?
Which of the following script types is used with the Python language by default?
Which of the following often uses an SMS or third-party application as a secondary method to access a system?
A technician installed Windows 10 on a workstation. The workstation only has 3.5GB of usable RAM, even though the technician installed 8GB. Which of the following is the MOST likely reason this system is not utilizing all the available RAM?
A technician is troubleshooting boot times for a user. The technician attempts to use MSConfig to see which programs are starting with the OS but receives a message that it can no longer be used to view startup items. Which of the following programs can the technician use to view startup items?
A BSOD appears on a user's workstation monitor. The user immediately presses the power button to shut down the PC, hoping to repair the issue. The user then restarts the PC, and the BSOD reappears, so the user contacts the help desk. Which of the following should the technician use to determine the cause?
A technician is installing a program from an ISO file. Which of the following steps should the technician take?
A technician is troubleshooting an issue with a computer that contains sensitive information. The technician determines the computer needs to be taken off site for repair. Which of the following should the technician do NEXT?
A Windows user recently replaced a computer The user can access the public internet on the computer; however, an internal site at https7/companyintranet.com:8888 is no longer loading. Which of the following should a technician adjust to resolve the issue?
A technician is troubleshooting a PC that has been performing poorly. Looking at the Task Manager, the technician sees that CPU and memory resources seem fine, but disk throughput is at 100%.
Which of the following types of malware is the system MOST likely infected with?
A technician receives a call from a user who is unable to open Outlook. The user states that Outlook worked fine yesterday, but the computer may have restarted sometime overnight. Which of the following is the MOST likely reason Outlook has stopped functioning?
Which of the following editions of Windows 10 requires reactivation every 180 days?
A technician installed Windows 10 on a workstation. The workstation only has 3.5GB of usable RAM, even though the technician installed 8GB. Which of the following is the MOST likely reason this system is not utilizing all the
available RAM?
A systems administrator is creating a new document with a list of the websites that users are allowed to access. Which of the following types of documents is the administrator MOST likely creating?
Which of the following options should MOST likely be considered when preserving data from a hard drive for forensic analysis? (Select TWO).
A computer on a corporate network has a malware infection. Which of the following would be the BEST method for returning the computer to service?
An implementation specialist is replacing a legacy system at a vendor site that has only one wireless network available. When the specialist connects to Wi-Fi. the specialist realizes the insecure network has open authentication. The technician needs to secure the vendor's sensitive data. Which of the following should the specialist do FIRST to protect the company's data?
A new employee was hired recently. Which of the following documents will the new employee need to sign before being granted login access to the network?
A user contacts a technician about an issue with a laptop. The user states applications open without being launched and the browser redirects when trying to go to certain websites. Which of the following is MOST likely the cause of the user's issue?
A customer calls a service support center and begins yelling at a technician about a feature for a product that is not working to the customer's satisfaction. This feature is not supported by the service support center and requires a field technician to troubleshoot. The customer continues to demand service. Which of the following is the BEST course of action for the support center representative to take?
A technician needs to provide recommendations about how to upgrade backup solutions for a site in an area that has frequent hurricanes and an unstable power grid. Which of the following should the technician recommend implementing?
Which of the following can be used for multifactor authentication when logging in to a computer system? (Select two).
Which of the following Windows 10 editions is the most cost-effective and appropriate for a single user who needs to access their computer remotely?
A Windows user wants a filesystem that protects confidential data from attackers who have physical access to the system. Which of the following should the user choose?
A customer needs to verify an executable file that the customer downloaded from a website. Which of the following should the customer use to verify the file?
Which of the following is the most significant drawback of using the WEP protocol for wireless security?
Which of the following script file types is typically used to install Windows packages?
A user has been adding data to the same spreadsheet for several years. After adding a significant amount of data, they are now unable to open the file. Which of the following should a technician do to resolve the issue?
A user's PC is performing slowly after the user clicked on a suspicious email attachment. The technician notices that a single process is taking 100% of RAM, CPU, and network resources. Which of the following should the technician do first?
A user is unable to browse a website on a PC. Which of the following commands should a technician use to verify the PC's DNS resolution for the website?
A customer reports that an Android phone will not allow the use of contactless electronic payment. Which of the following needs to be enabled to resolve the issue?
A company is opening several remote offices and would like to have the capability for its systems administrator to automate patch management and software deployment. Which of the following would meet this requirement?
A technician recently installed a new router for a small business. Afterwards, the technician completed an external port scan and generated the following information:
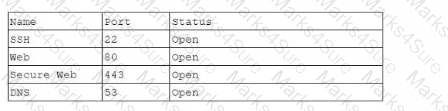
Which of the following should the technician perform next in order to follow best practices?
A technician is trying to perform an in-place upgrade of a Windows OS from a file. When the technician double-clicks the file, the technician receives a prompt to mount a drive. Which of the following file types did the technician download?
A technician reports that a SOHO wireless network was compromised by an attacker who brute forced a password to gain access. The attacker was able to modify the DNS settings on the router and spread malware to the entire network. Which of the following configurations would most likely have allowed the attack to take place? (Select two).
A technician has been tasked with installing a workstation that will be used for point-of-sale transactions. The point-of-sale system will process credit cards and loyalty cards. Which of the following encryption technologies should be used to secure the workstation in case of theft?
Which of the following features can be used to ensure a user can access multiple versions of files?
An MDM report shows that a user's company cell phone has unauthorized applications installed. The device has recently checked into the MDM server, and the company still has access to remotely wipe the device. Which of the following describes the action the user has performed?
An application's performance is degrading over time. The application is slowing but never gives an error and does not crash. Which of the following tools should a technician use to start troubleshooting?
A technician is reusing several hard drives to increase local storage on company workstations. The drives contain PII that is no longer needed. Which of the following should the technician do to prevent unauthorized access to the data?
Which of the following filesystems is most likely to be used for the boot volume on a Linux desktop?
A technician is troubleshooting a user's PC that is displaying pop-up windows advertising free software downloads. When the technician tries to open a document, the system displays an error message: "Not enough memory to perform this operation." Which of the following should be the technician's next step to resolve this issue?
Which of the following commands should a technician use to change user permissions?
A technician is creating a Windows splash screen that details login expectations. Which of the following should the technician most likely use?
Employees want their Windows 10 laptops to wirelessly connect when they take them home. Which of the following should the employees configure so the laptops can automatically connect wirelessly?
A systems administrator needs to access a hypervisor that went offline. After doing a port scan, the administrator notices that company policy is blocking the RDP default port. Which of the following ports should the administrator use to access the machine?
A technician is working at a client office site, and the technician’s family member repeatedly calls and texts about a non-emergency situation. Which of the following should the technician do?
Which of the following file types should be used to install software on a macOS computer? (Select two).
A user with a disability needs to be able to press the Ctrl+Alt+Del keyboard sequence one key at a time. Which of the following turns on this Ease of Access feature?
A technician is updating the OS on a number of Windows workstations. After successfully updating several workstations, the technician receives an error indicating that the upgrade takes more space than is available on one of the PCs. Which of the following should the technician do to proceed with the upgrade? (Select two).
A network administrator is showing an email application on a personal cell phone to a coworker. The cell phone is enrolled in the company's MDM program. When launching the application store to download the email application, the coworker receives a security warning stating the device violates company policies due to root-level access. Which of the following should the coworker perform next to resolve the issue?
Which of the following will automatically map network drives based on Group Policy configuration?
A support specialist needs to decide whether to install a 32-bit or 64-bit OS architecture on a new computer. Which of the following specifications will help the specialist determine which OS architecture to use?
After access to a server room was breached, a technician needs to implement a secure method to prevent unauthorized access. Which of the following is the most secure solution?
A user calls the help desk to report an issue with their smartphone. After the user returns from a business trip, the user is no longer able to access email or visit websites without a Wi-Fi connection on the smartphone. Which of the following could the user do to most likely resolve the issue?
A technician thinks that a computer on the network has been infected with malware. The technician attempts several times to use a malware removal tool, but the issue persists. Which of the following should the technician do next?
A user visits a game vendor's website to view the latest patch notes, but this information is not available on the page. Which of the following should the user perform before reloading the page?
A user's iPhone was permanently locked after several tailed login attempts. Which of the following will restore access to the device?
A user attempts to install additional software and receives a UAC prompt. Which of the following is the BEST way to resolve this issue?
A technician installs specialized software on a workstation. The technician then attempts to run the software. The workstation displays a message indicating the software is not authorized to run. Which of the following should the technician do to most likely resolve the issue?
A department manager submits a help desk ticket to request the migration of a printer's port utilization from USB to Ethernet so multiple users can access the printer. This will be a new network printer; thus a new IP address allocation is required. Which of the following should happen immediately before network use is authorized?
A company is experiencing a DDoS attack. Several internal workstations are the source of the traffic. Which of the following types of infections are the workstations most likely experiencing? (Select two).
A help desk technician determines a motherboard has failed. Which of the following is the most logical next step in the remediation process?
A developer receives the following error while trying to install virtualization software on a workstation:
VTx not supported by system
Which of the following upgrades will MOST likely fix the issue?
A company is looking lot a solution that provides a backup for all data on the system while providing the lowest impact to the network. Which of the following backup types will the company MOST likely select?
A customer has a USB-only printer attached to a computer. A technician is configuring an arrangement that allows other computers on the network to use the printer. In which of the following locations on the customer's desktop should the technician make this configuration?
During a network outage, a technician discovers a new network switch that was not listed in the support documentation. The switch was installed during a recent change window when a new office was added to the environment. Which of the following would most likely prevent this type of mismatch after next month's change window?
A workstation is displaying a message indicating that a user must exchange cryptocurrency for a decryption key. Which of the following is the best way for a technician to return the device to service safely?
A systems administrator is tasked with configuring desktop systems to use a new proxy server that the organization has added to provide content filtering. Which of the following Windows utilities is the best choice for accessing the necessary configuration to complete this goal?
During an enterprise rollout of a new application, a technician needs to validate compliance with an application's EULA while also reducing the number of licenses to manage. Which of the following licenses would best accomplish this goal?
Which of The following refers to the steps to be taken if an Issue occurs during a change Implementation?
A corporation purchased new computers for a school. The computers are the same make and model and need to have the standard image loaded. Which of the following orchestration tools should a desktop administrator use tor wide-scale deployment?