An administrator has a requirement to have consistent policy configuration and enforcement across NSX instances.
What feature of NSX fulfills this requirement?
Which table on an ESXi host is used to determine the location of a particular workload for a frame-forwarding decision?
Which TraceFlow traffic type should an NSX administrator use for validating connectivity between App and DB virtual machines that reside on different segments?
Where can an administrator see a visual overview of network connections between different VMs and different networks, within the NSX domain?
Which command is used to set the NSX Manager’s logging-level to debug mode for troubleshooting?
Where in the NSX UI would an administrator set the time attribute for a time-based Gateway Firewall rule?
Which of the following settings must be configured in an NSX environment before enabling stateful active-active SNAT?
What are four NSX built-in role-based access control (RBAC) roles? (Choose four.)
Which NSX CLI command is used to change the authentication policy for local users?
Which NSX feature can be leveraged to achieve consistent policy configuration and simplicity across sites?
A customer is preparing to deploy a VMware Kubernetes solution in an NSX environment.
What is the minimum MTU size for the UPLINK profile?
An NSX administrator is using ping to check connectivity between VM1 running on ESXi1 to VM2 running on ESXi2. The ping tests fail. The administrator knows the maximum transmission unit size on the physical switch is 1600.
Which command does the administrator use to check the VMware kernel ports for tunnel end point communication?
A customer has a network where BGP has been enabled and the BGP neighbor is configured on the Tier-0 Gateway. An NSX administrator used the get gateways command to retrieve this information:

Which two commands must be executed to check BGP neighbor status? (Choose two.)
Which two statements describe the characteristics of an Edge Cluster in NSX? (Choose two.)
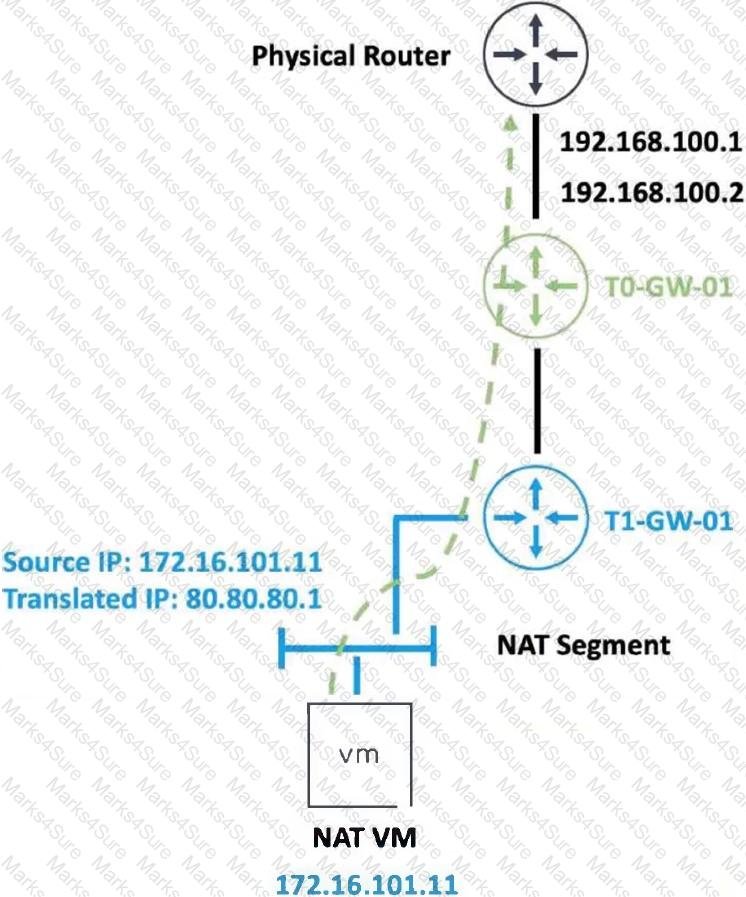
Refer to the exhibit.
An administrator would like to change the private IP address of the NAT VM 172.16.101.11 to a public address of 80.80.80.1 as the packets leave the NAT-Segment network.
Which type of NAT solution should be implemented to achieve this?
Which two of the following features are supported for the Standard NSX Application Platform Deployment? (Choose two.)
Which three of the following describe the Border Gateway Routing Protocol (BGP) configuration on a Tier-0 Gateway? (Choose three.)
When deploying an NSX Edge Transport Node, what two valid IP address assignment options should be specified for the TEP IP addresses? (Choose two.)
Which two choices are use cases for Distributed Intrusion Detection? (Choose two.)
Which steps are required to activate Malware Prevention on the NSX Application Platform?
Refer to the exhibits.
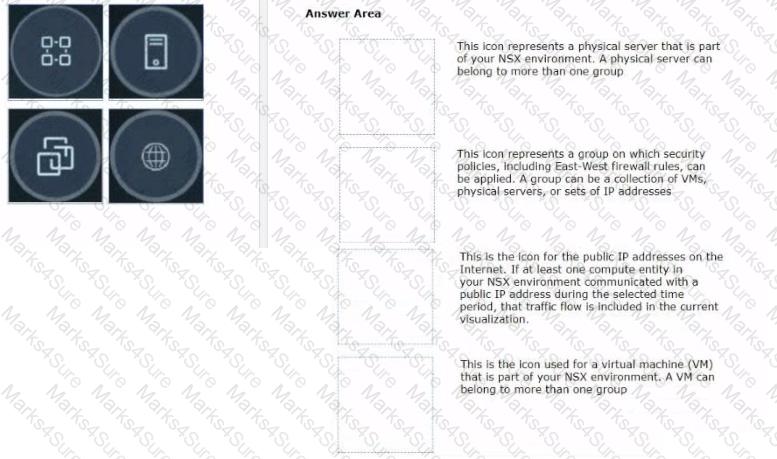
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.
Which two statements are correct about East-West Malware Prevention? (Choose two.)
An NSX administrator is reviewing syslog and notices that Distributed Firewall Rules hit counts are not being logged.
What could cause this issue?
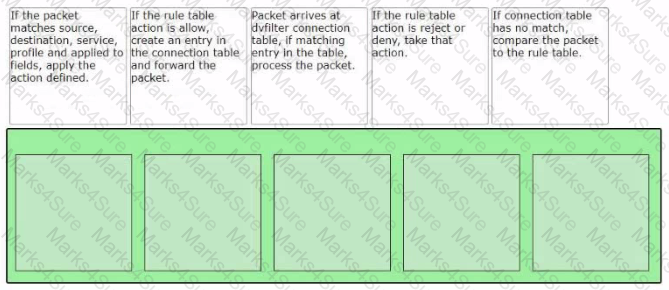
Sort the rule processing steps of the Distributed Firewall. Order responses from left to right.
Which VMware NSX Portfolio product can be described as a distributed analysis solution that provides visibility and dynamic security policy enforcement for NSX environments?