Which two statements are correct when FortiGate enters conserve mode? (Choose two.)
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?
An organization requires remote users to send external application data running on their PCs and access FTP resources through an SSUTLS connection.
Which FortiGate configuration can achieve this goal?
Refer to the exhibit, which shows a partial configuration from the remote authentication server.

Why does the FortiGate administrator need this configuration?
Refer to the exhibit showing a FortiGuard connection debug output.
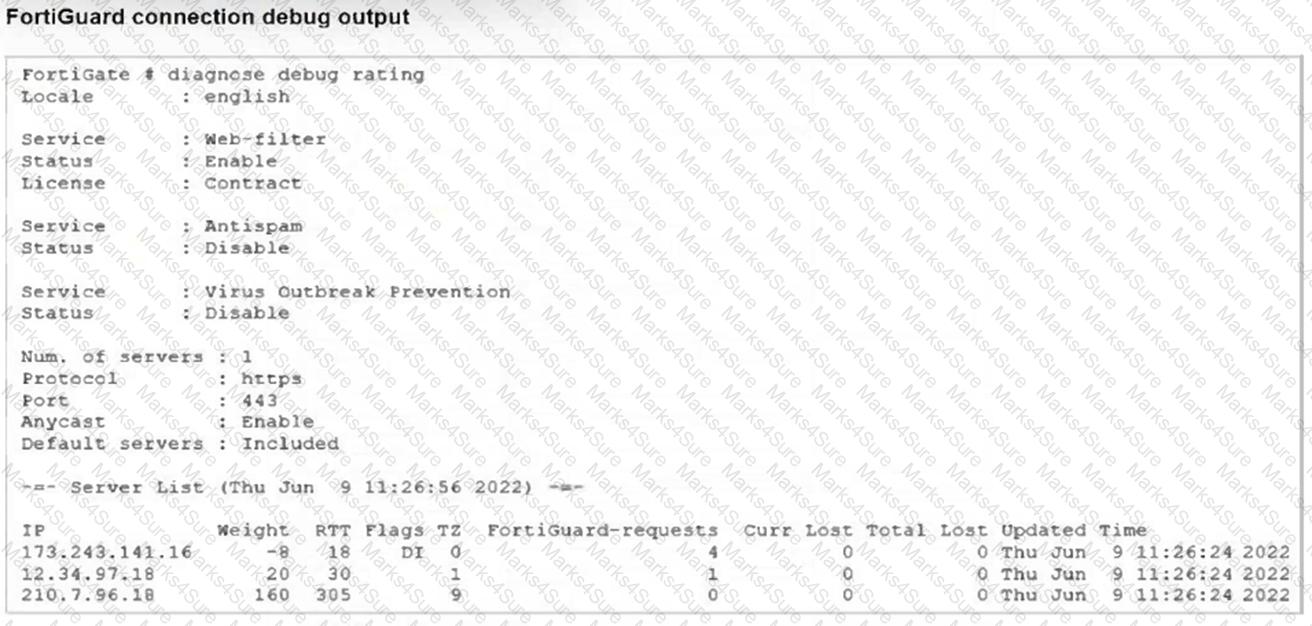
Based on the output, which two facts does the administrator know about the FortiGuard connection? (Choose two.)
Which method allows management access to the FortiGate CLI without network connectivity?
Which two pieces of information are synchronized between FortiGate HA members? (Choose two.)
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements are true about the requirements of connected physical interfaces on FortiGate? (Choose two.)
Refer to the exhibit.
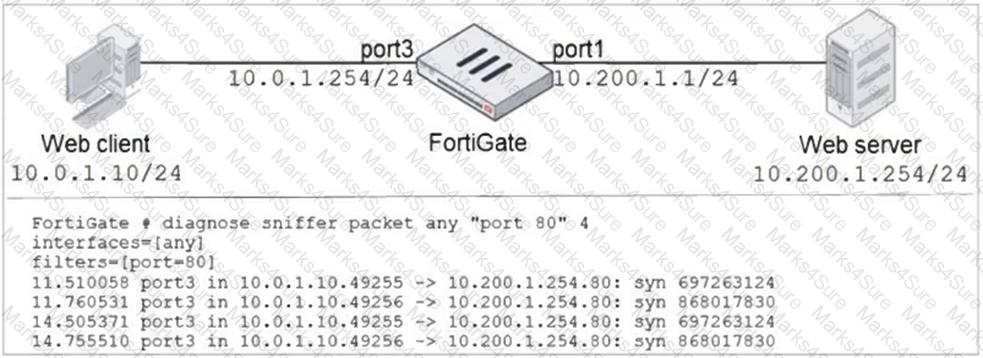
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
An administrator configured a FortiGate to act as a collector for agentless polling mode.
What must the administrator add to the FortiGate device to retrieve AD user group information?
An employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
Refer to the exhibit.
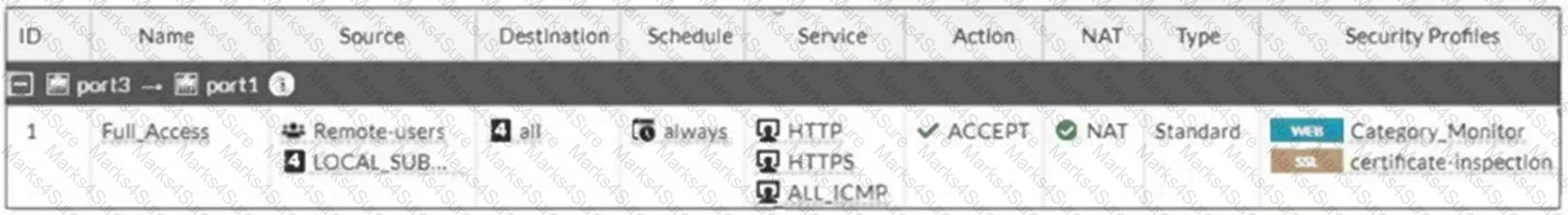
FortiGate is configured for firewall authentication. When attempting to access an external website, the user is not presented with a login prompt.
What is the most likely reason for this situation?
An administrator has configured a strict RPF check on FortiGate.
How does strict RPF check work?
An administrator has configured the following settings:
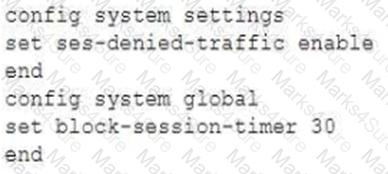
What are the two results of this configuration? (Choose two.)
Refer to the exhibits.
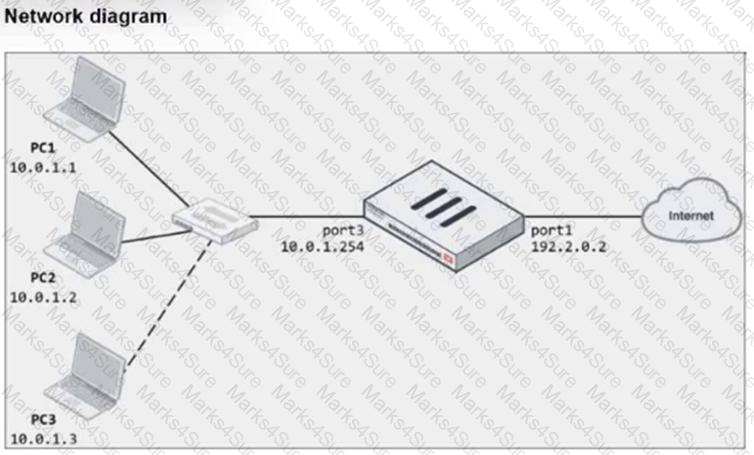
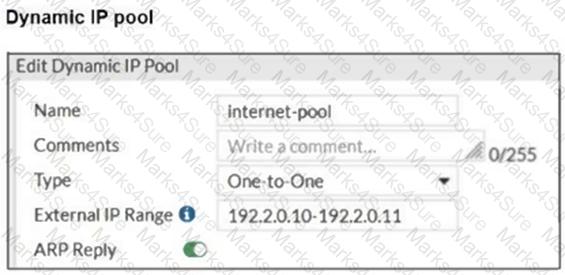
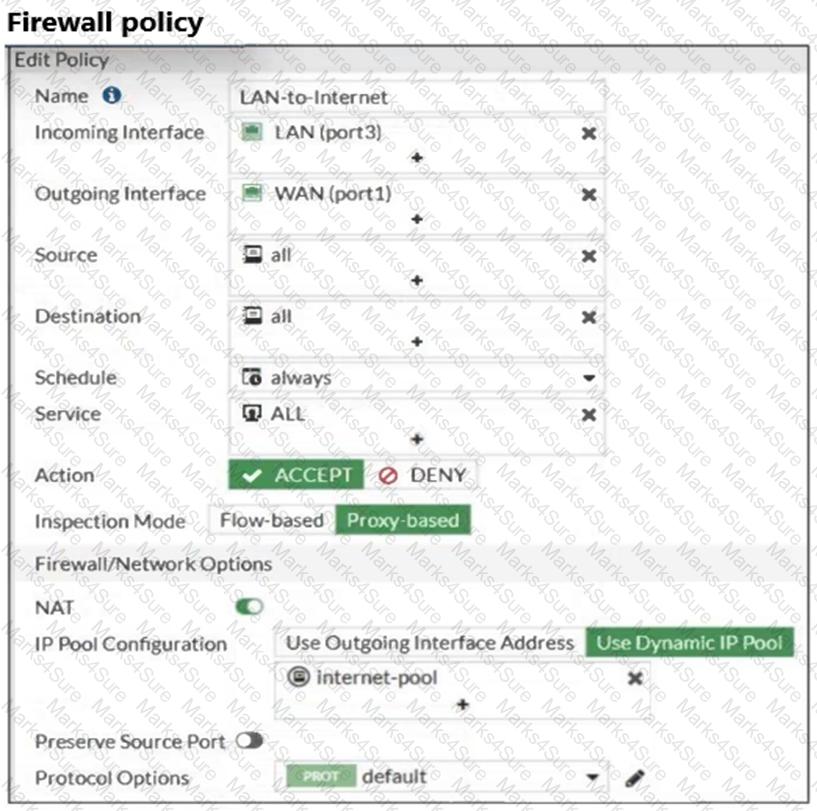
The exhibits show a diagram of a FortiGate device connected to the network, as well as the firewall policy and IP pool configuration on the FortiGate device.
Two PCs, PC1 and PC2, are connected behind FortiGate and can access the internet successfully. However, when the administrator adds a third PC to the network (PC3), the PC cannot connect to the internet.
Based on the information shown in the exhibit, which two configuration options can the administrator use to fix the connectivity issue for PC3? (Choose two.)
An administrator wants to configure dead peer detection (DPD) on IPsec VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when there is outbound traffic but no response from the peer.
Which DPD mode on FortiGate meets this requirement?
What is the primary FortiGate election process when the HA override setting is disabled?
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?
Which two features of IPsec IKEv1 authentication are supported by FortiGate? (Choose two.)
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the
and does not block the file allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
Which three strategies are valid SD-WAN rule strategies for member selection? (Choose three.)