A company using PaaS to host and develop their software application is experiencing a DOS attack. What challenge will a DFIR analyst experience when investigating this attack?
What is the recommended storage type when creating an initial snapshot of a VM in Azure for forensic analysis?
An attacker successfully downloaded sensitive data from a misconfigured GCP bucket. Appropriate logging was not enabled. Where can an analyst find the rough time and quantity of the data downloaded?
At what point of the OAuth delegation process does the Resource Owner approve the scope of access to be allowed?
Sensitive company data is found leaked on the internet, and the security team didn't
get any alert and is unsure of how the breach occurred.
Which logs would be a preferable starting point for an investigation?
Communication between the VPN client and Azure VNet1via VPN Tunnel #1 is using which of the following connections?

An investigator is evaluating a client's Microsoft 365 deployment using the web portals and has identified that the Purview compliance portal states that the Unified Audit Logs are not enabled. Based on the additional Information gathered below, what is most likely the cause of this configuration message?
Subscription creation date: December 4, 2021 Number of administrators: 2 Number of non-administrative user accounts: 74 Last tenant administration change: December 4,2021
What is the lowest level of GCP organization that consists of a logical grouping of services?
An investigator his successfully installed the ExchangeOnlineManagement module on their investigation system and is attempting to search a client's Microsoft 365 Unified Audit Log using PowerShell. PowerShell returns a "command not found" error each time they try to execute the Search-UnifiedAuditLog cmdlet. How should the investigator troubleshoot this issue?
An Azure blob is accessed using the link below. What is the name of the blob container?

After registering the application in Azure AD, what is the next step to take in order to use Microsoft Graph API?
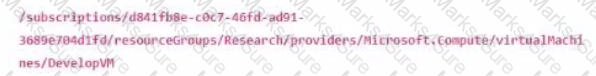
The Azure URI for the Develop VM is shown below. What will change in the notation when referencing the VM's OS disk?