Refer to the graphic, 00e0-fc99-9999 is a specific host MAC address learned by a switch through ARP, and the host changes the IP address three times.
Following a failure of services in the network, an administrator discovered that the configuration in one of the enterprise routers had been changed. What actions can be taken by the administrator to prevent further changes?
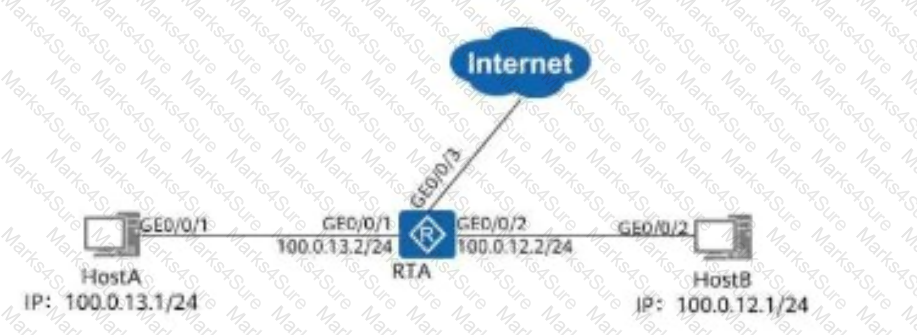
On the network shown in the figure, the router receives a data packet with the destination IP address 11.0.12.1 from Host A.

After the packet is forwarded by the router, which of the following are the destination MAC address and destination IP address of the data packet?
The Priority field in a VLAN tag can be used to identify the priority of a data frame. What is the value range of the field?
Which of the following authentication modes does/do not require a user name and a password?
Refer to the following configuration of an interface on a switch. For which VLAN does the interface remove VLAN tags before forwarding data frames?
go
CopyEdit
interface GigabitEthernet0/0/1
port link-type trunk
port trunk pvid vlan 10
port trunk allow-pass vlan 10 20 30 40
In a broadcast address, all host bits are set to 1, and a broadcast address can be used as a host address.
Which SNMP version focuses on two main aspects, namely security and administration? The security aspect is addressed by offering both strong authentication and data encryption for privacy. The administration aspect is focused on two parts, namely notification originators and proxy forwarders.
On the VRP platform, which of the following parameters can be used together with the "ping" command to specify the source address of an echo request message?
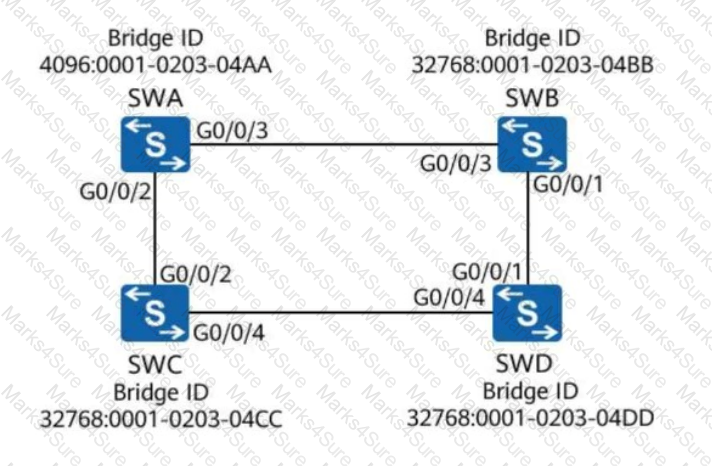
As shown in the figure, all switches run STP. Assume that the path cost of all ports is 200. What is the root path cost contained in the configuration BPDU received by G0/0/4 on SWD?
Which of the following statements about static routes on Huawei devices is false?
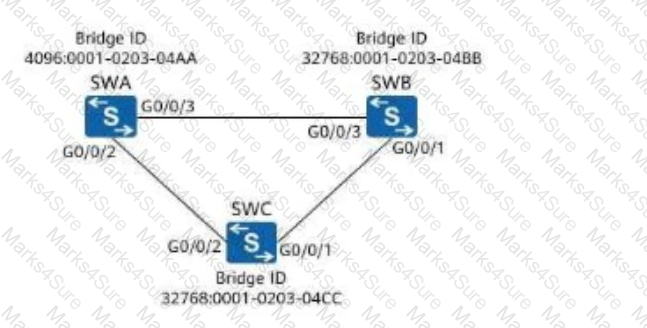
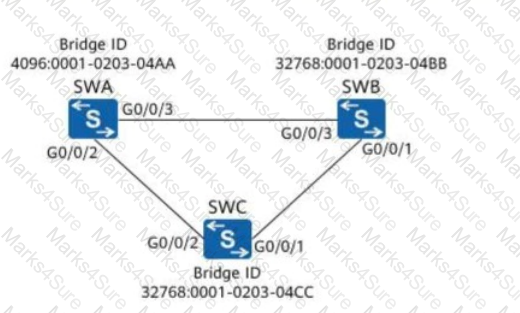
On the network shown in the following figure, assuming that SWA, SWB, and SWC retain factory defaults, which of the following ports will be selected as a designated port?
Which of the following are advantages of stacking and CSS (Cluster Switch System) technologies?
For STP, the Message Age in the configuration BPDUs sent by the root bridge is 0.
If Proto of a route displayed in the routing table is OSPF, the preference of the route must be 10.
When an AP and an AC are located on different Layer 3 networks, which of the following methods is recommended for the AP when discovering the AC?
Which of the following configurations can prevent Host A and Host B from communicating with each other?
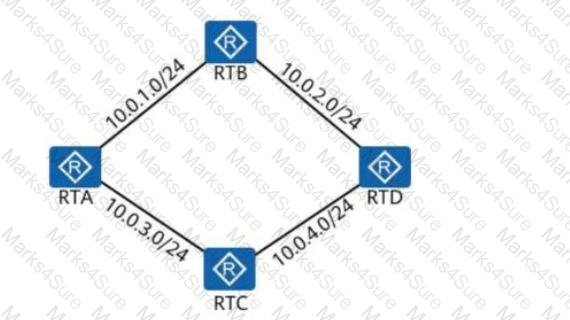
In the following figure, all links are Ethernet links, and all interfaces on the routers are running OSPF. Given this, how many DRs will be elected on this network?
As shown in the figure, which of the following ports will be in a blocking state?
On an STP-enabled switch, a port in the forwarding state can receive BPDU packets.
Refer to the following configuration of an interface on a switch. For which VLAN does the interface transmit tagged data frames?
interface GigabitEthernet0/0/1
port hybrid tagged vlan 2 to 3 100
port hybrid untagged vlan 4 6
To provide the information about the IP addresses that a user packet traverses along the path to the destination, which of the following does Tracert record in each expired ICMP TTL packet?
The CAPWAP protocol defines the communication standard between ACs and APs. Which of the following statements about CAPWAP is true?
In RSTP, an edge port becomes a common STP port after receiving a configuration BPDU.
A Layer 2 ACL can match information such as the source MAC address, destination MAC address, source IP address, and destination IP address.
Which of the following information is displayed when an entered command is incomplete on the Versatile Routing Platform (VRP)?
If the network administrator assigns the IPv4 address 192.168.1.1/28 to a host on the network, how many hosts can be added to the network where the host resides?
Refer to the following figure of the ACL configured on a router. Which of the following statements is true?
nginx
CopyEdit
acl number 2000
rule 5 permit source 192.168.1.1 0
rule 10 deny source 192.168.1.1 0
The following configuration commands implement route backup on RTA for a route to the same destination 10.1.1.0.
[RTA] ip route-static 10.1.1.0 24 12.1.1.1 permanent
[RTA] ip route-static 10.1.1.0 24 13.1.1.1
When the host accesses the web service of the server, the value of the "Protocol" field at the network layer is 6.
Refer to the captured three packets shown in the figure. Which of the following statements is false?
With SNMP, an NMS can only display the device running status but cannot deliver configurations.
What is the protocol of the Router Advertisement (RA) packet, which is used in IPv6 stateless address auto-configuration?
An administrator wishes to manage the router in the remote branch office, which method can be used?
The tree topology is a hierarchical star topology, facilitating network expansion. A consequence of this topology is that faults on a node at a higher layer are more severe.
The router ID of the OSPF-enabled router must be the same as the IP address of an interface on the router.
When a host uses the stateless address autoconfiguration solution to obtain an IPv6 address, the host cannot obtain the DNS server address.
Which of the following protocols can be used to prevent Layer 2 loops on a campus network?
(By default, in the SNMP protocol, which port number is used by the proxy process to send alarm messages to the NMS?)
(When a network engineer enters a command, the following information is displayed:
Error: Unrecognized command found at 'A' position. Which of the following statements is true about such information?)
What is the length range of an Ethernet_II frame that contains an Ethernet header?
< Huawei > system-view
[Huawei]command-privilege level 3 view user save
Refer to the command output. What is the result of the shown command?
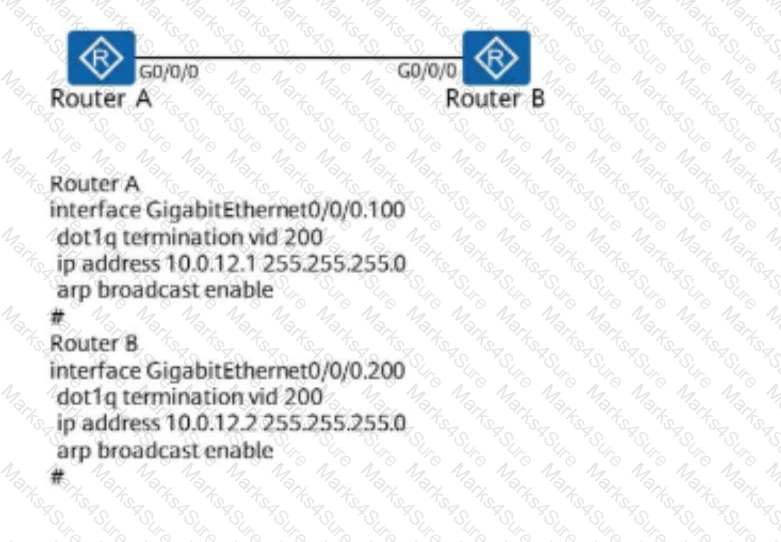
The following figure shows the configuration of a sub-interface on a router. For which VLAN does the sub-interface receive tagged data frames?
Which of the following packets is used by network devices running SNMPv1 to proactively send alarm information?
Which of the following methods is not supported by the Versatile Routing Platform (VRP) to configure a router?
UDP does not guarantee data transmission reliability and does not provide packet sorting and traffic control functions. It is suitable for the traffic that has low requirements for data transmission reliability, but high requirements for the transmission speed and delay.
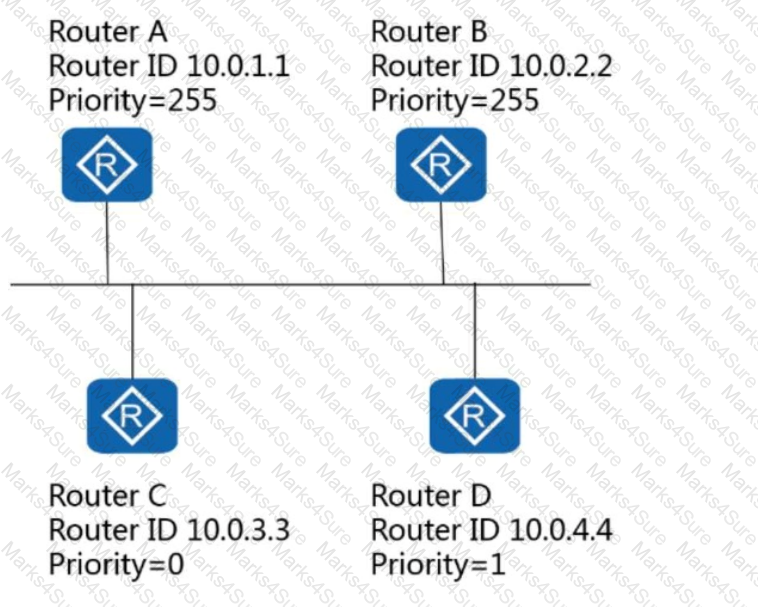
Assuming that OSPF has been enabled on all routers in the following figure, which router is the BDR on this network?
Which of the following statements about the network shown in the figure is true?
As specified by the RSTP protocol, when a root port fails, which type of port will function as a new root port and enter the forwarding state without any delay?
Which of the following WLAN security policies support open link authentication?
The router ID of the OSPF process takes effect immediately after being changed.
In the case of Huawei routers, what is the "-i" parameter in a Ping command issued on a VRP operating system used to set?
Refer to the network diagram.
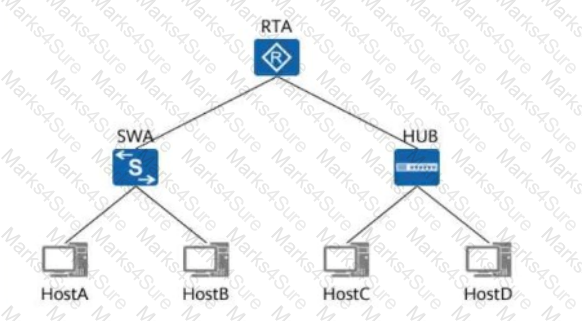
Which of the following statements describes the network shown?
Which of the following states indicates that the OSPF neighbor relationship has been established?
When the "delete vrpcfg.zip" command is run on the Huawei VRP user interface, the file can be permanently deleted only after it is cleared from the recycle bin.
On an STP-enabled switch, a port in the Learning state can transition to the Forwarding state only after the Forward Delay timer expires.
On Huawei VRP platform, which of the following can be used to invoke the history command saved by the command line interface?
An ACL rule is as follows. Which of the following IP addresses can be matched by the permit rule?
Rule: rule 5 permit ip source 10.0.2.0 0.0.254.255
Which of the following commands sets the data forwarding mode on an AC to direct forwarding?
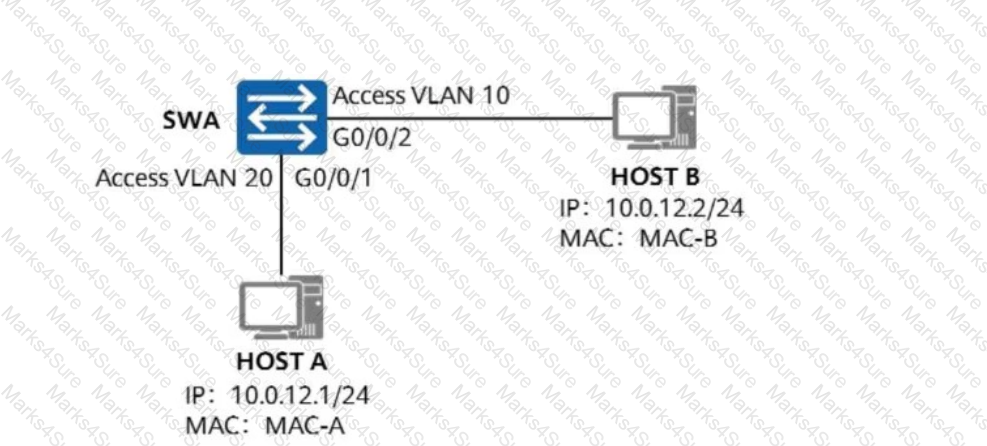
As shown in the figure, if host A has the ARP cache of host B, host A can ping host B.
A company applies for a class C IP address for subnetting. It has six branches and the largest branch should have 26 hosts. What would be an appropriate subnet mask for the largest branch?
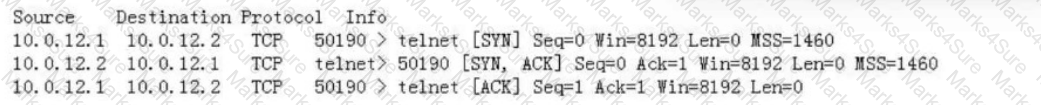
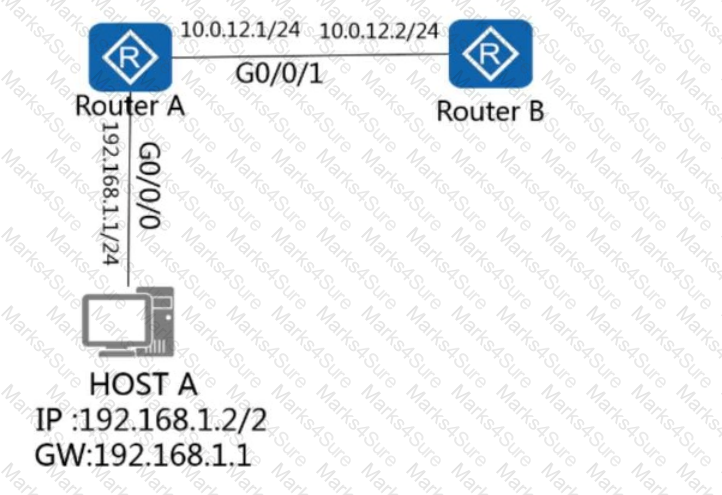
On the network shown in the figure, host A logs in to router A through Telnet and obtains the configuration file of router B through FTP on the remote CLI. How many TCP connections exist on router A?
A router that runs OSPF can enter the Full state only after Link-State Database (LSDB) synchronization is completed.
Which statement is true regarding the following command?
ip route-static 10.0.12.0 255.255.255.0 192.168.1.1
The users who log on the router through Telnet are not permitted to configure an IP address. What is the possible reason?
Which SNMP version focuses on two main aspects, namely security and administration. The security aspect is addressed by offering both strong authentication and data encryption for privacy. The administration aspect is focused on two parts, namely notification originators and proxy forwarders.
Refer to the display startup command output shown in the figure. Which of the following statements are true?