After BGP initiates a TCP connection, the ConnectRetry timer is disabled if the TCP connection is successfully established. If the TCP connection fails to be established, the device tries to reestablish the TCP connection when the ConnectRetry timer expires.
According to BGP route selection rules, the route with the higher Local_Pref is preferred.
On an OSPF network, an algorithm is used to prevent loops within an area, but loops may occur between areas. Therefore, OSPF defines a loop prevention mechanism for inter-area routes. Which of the following statements are true about the loop prevention mechanism?
IGMP has three versions. Different versions support different features. Which of the following features is supported by all versions?
Four routers run ISIS and have established adjacencies. The area IDs and router levels are marked in the following figure. If route leaking is configured on R3, which of the following is the cost of the route from R4 to 10.0.2.2/32?
Huawei modular devices have multiple hardware modules that provide different functions. Match the following hardware modules with their functions.

On an IS-IS network, each router can generate LSPs. Which of the following events trigger the generation of a new LSP?
Route attributes are specific descriptions of routes. BGP route attributes can be classified into four types. Which of the following are well-known discretionary attributes?
A network entity title consists of an area address and a system ID. It is a special NSAP (the SEL has a fixed value of 00) and is mainly used for route calculation.
A BGP device receives a route carrying an unknown attribute from a peer but does not know whether other devices need the attribute. In this case, the BGP device retains this attribute when advertising the route to other peers. Which of the following attributes is of this type?
IGMP group entries play an important role in multicast forwarding. An administrator runs a command to view information about a multicast entry. The information is as follows:
sql
Copy
Interface group report information
Vlanif100(10.1.6.2):
Total 1 IGMP Group reported
Group Address Last Reporter Uptime Expires
225.1.1.2 10.1.6.10 00:02:04 00:01:17
Given this, which of the following statements are true?
In IPv6, to communicate with a destination host, a host must obtain the link-layer address of the destination host through ARP.
The BFD Echo function checks the connectivity of the forwarding link by looping back packets. Which of the following statements are true about this function?
A Huawei firewall by default creates security zones named untrust, dmz, _________ and local. (Use Lowercase letters.)
In addition to a route reflector, the confederation is another method that reduces the number of IBGP connections in an AS.
Which of the following statements are true about the confederation technology? (Choose all that apply)
In BGP, the origin attribute of the routes imported using the import-route command is incomplete.
A switch runs MSTP. The configuration is shown in the figure. What is the role of this switch in MSTI 1?
On an STP network, only the designated port processes inferior BPDUs. On an RSTP network, a port with any role processes inferior BPDUs.
R1, R2, R3, and R4 run IS-IS, and the DIS priorities of their interfaces are shown in the following figure. Ifall these devices are started simultaneously, will be elected as the DIS. (Enter the device name, for example, R1.)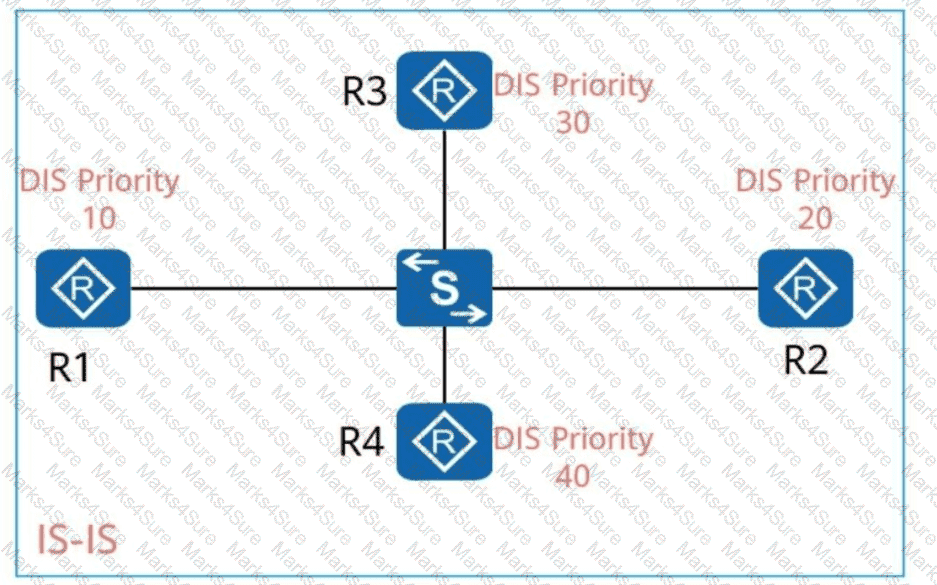
A campus network uses OSPF for network communication. The display ospf peer command is run on a router, and the command output is as follows:
vbnet
Copy
Edit
OSPF Process 1 with Router ID 10.0.2.2
Area 0.0.0.0 interface 10.0.235.2 (GigabitEthernet0/0/1)'s neighbors
Router ID: 10.0.5.5 Address: 10.0.235.5
State: Full Mode: Nbr is Master Priority: 1
DR: 10.0.235.5 BDR: 10.0.235.3 MTU: 0
Dead timer due in 40 sec
Area 0.0.0.0 interface 10.0.24.2 (Serial1/0/1)'s neighbors
Router ID: 10.0.4.4 Address: 10.0.24.4
State: Full Mode: Nbr is Master Priority: 1
DR: None BDR: None MTU: 0
Dead timer due in 35 sec
Which of the following statements are true about the device?
An enterprise uses OSPF to implement network communication. To ensure data validity and security, all authentication modes supported by OSPF are enabled on routers. In this case, interface authentication is preferentially used by the routers.
OSPF supports area authentication and interface authentication. If both authentication modes are configured, Interface authentication takes preference over area authentication.
Which of the following statements regarding the firewall zone security level is false?
In BGP, the AS_Path attribute records the numbers of all ASs that a route passes through from the local end to the destination in the vector order.
Which of the following statements is false about the attribute change during route transmission?
The Neighbor Discovery Protocol (NDP) is an important basic protocol in the IPv6 protocol suite and plays an important role. Which of the following functions and features does it support?
On a network, each router has a local core routing table and protocol routing tables. A routing entry in the local core routing table has multiple key fields. Which of the following are included?
On an STP network, parameters used for role election, such as the root bridge ID, root path cost, and bridge ID, are all fields in BPDUs.
On an OSPF network, if a router functions as an ABR, the router must also be a BR.
Which of the following is the default dead time of an interface on an OSPF P2P or broadcast network?
GRE is a Layer 2 VPN encapsulation technology that encapsulates packets of certain data link layer protocols so that the encapsulated packets can be transmitted over an IP network.
In IPv6, interface IDs can be manually configured, automatically generated by the system, or generated based on the IEEE EUI-64 standard.
IGMPv2 uses the timeout mechanism for group members leaving a group. Group members can only leave a group silently. Before the timeout period expires, multicast traffic is still forwarded by the multicast router, and this is a defect.
Which of the following attributes must be carried when BGP sends route update messages?
Compress the 2001:0DBB:B8:0000:C030:0000:0000:09A0:CDEF address.___________(if the answer contains letters, capitalize them.)
PBR is a mechanism for selecting routes based on user-defined policies. There are two types of PBR: interface-based PBR and local PBR. Which of the following statements is false about these two types of PBR?
VRF, also called VPN instance, is a network virtualization technology that helps VPN technology to isolate users. In normal cases, multiple VPN instances can be created on a physical device, and each VPN instance has independent entries. Which of the following resources can be independently owned by a VPN instance?
To enable PC1 to access PC2 using the IP address of the firewall's GE0/0/2, you need to configure NAPT for source address translation. In the following figure, fill in the blank to complete the command.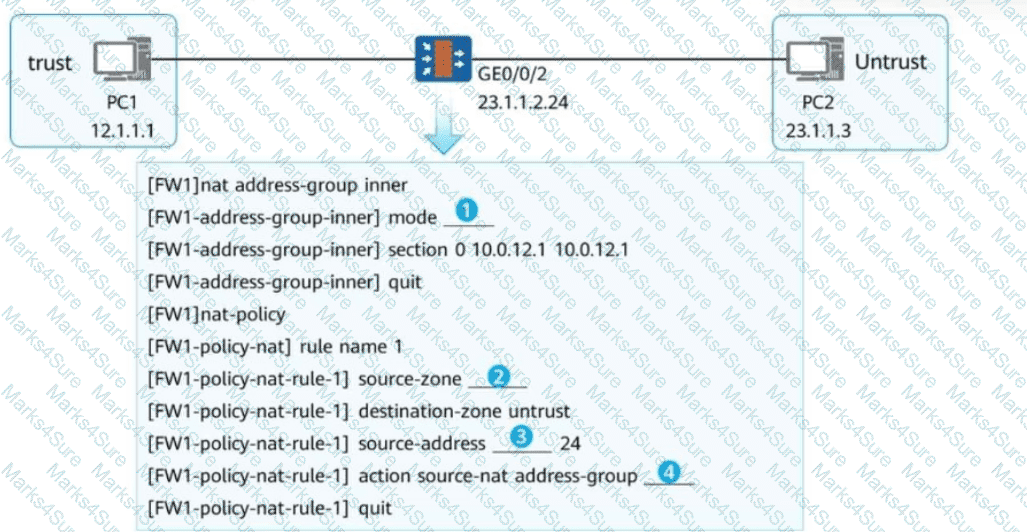
IP multicast effectively conserves network bandwidth and reduces network load. Therefore, it is widely used in network services, such as IPTV, real-time data transmission, and multimedia conferencing.
BGP routes have multiple path attributes. When a router advertises a BGP route to its peers, the route carries multiple path attributes. These attributes describe the characteristics of the BGP route and affect route selection in some scenarios. The attribute is Huawei-specific. It is valid only on the local device and is not transmitted to BGP peers. (Enter the attribute name in lowercase as it appears in the command output about the BGP routing table.)
An enterprise network runs OSPF to implement network communication. Which of the following types of LSAs may be generated by an ABR?
When receiving a packet that does not match any session table entry, the firewall discards the packet to prevent external attacks and ensure internal information security.
A route-policy consists of one or more nodes. What is the maximum number of nodes in a route-policy?
BFD can associate with multiple protocols to quickly detect faults.
Which of the following functions are supported?(Select all that apply)
A Layer 2 switch supports multiple types of Ethernet interfaces. Similar to a trunk interface, a hybrid interface allows data frames from multiple VLANs to pass through. In addition, you can determine whether data frames from a VLAN sent out from a hybrid interface are tagged or untagged.
A monitoring plane usually comprises the monitoring units of main control boards and interface boards. This plane can monitor the system environment independently. Which of the following environment monitoring functions can be provided by the monitoring plane?
ACLs are a common tool for matching routes. ACLs are classified into multiple types based on ACL rule functions. An ACL can be identified by a number, and the number range for each type of ACLs is different. Which of the following type of ACLs are numbered from 4000 to 4999?
In IP multicast, RPF routes can be elected only from among unicast routes and multicast static routes.
A route-policy can have multiple nodes, and each node can have multiple if-match and apply clauses. Which of the following statements are false?
After HSB is configured, the HSB channel fails to be established and cannot back up information on the active device to the standby device. What are the possible causes for this HSB function failure?
Which of the following PIM protocol packets have unicast destination addresses.
Which of the following statements regarding the summary automatic command and BGP route summarization is false?
Which of the following statements regarding OSPF route summarization commands are true?
L2TP does not provide security encryption. Therefore, other security measures, such as IPsec, are required to ensure the security of the entire tunnel for data transmission.
On a network, some switches are enabled with RSTP and some switches are enabled with STP. What will happen?
Which of the following is the default interval at which the DIS on a broadcast IS_IS network sends CSNPs.
Which of the following TLVs is used by ISIS to describe the IP address of an interface?
BFD control packets are encapsulated in UDP packets for transmission. What is the destination port number of multi-hop BFD control packets?
By default, a router interface sends PIM Hello messages at an interval of __________ seconds.
After a BGP peer relationship is established between two ends, changing the router ID of one end resets the BGP peer relationship.
Similar to the OSPF DR, the IS-IS DIS needs to be elected on a broadcast network. However, the OSPF DR is preemptive by default, whereas the IS-IS DIS is not preemptive by default.
VRRP defines three states. Only the device in which state can forward packets destined for a virtual IP address?
(Write in full and capitalize the first letter.)
Which of the following statements about the forwarding plane of a switch is false?
A switch running a later IGMP version can identify Report messages of an earlier IGMP version, but the switch running an earlier IGMP version cannot identify Report messages of a later IGMP version. To ensure that IGMP runs properly, you are advised to set the IGMP version on the switch to be the same as or later than the IGMP version of member hosts.
During routine O&M, an engineer finds that theHold Timeparameters of two devices are inconsistent. In this case, which of the following situations occurs?
A wide area network (WAN) is a remote network that connects local area networks (LANs) or metropolitan area networks (MANs) in different areas for communication purposes. It is typically used to interconnect campus networks or data center networks.
On an OSPF network, OSPF routers exchange LSAs to synchronize their LSDBs. If an OSPF router receives an LSA that does not exist in its LSDB, it updates its LSDB and floods the LSA.
Both MQC and PBR can be applied on device interfaces to filter received and sent packets or control packet forwarding paths.
Which of the following statements regarding the display bgp routing-table command output is true?
Compared with STP, RSTP defines the different port states. Which of the following statements regarding discarding and learning states are true?
In the OSPF protocol, intra-area route calculation involves only Router LSA, Network LSA, and Summary LSA.
As shown in the following figure, a new AP is deployed In dual link MSB networking (load balancing mode). Which AC will the connect to?
In special scenarios, when advertising routes to an IBGP peer, a BGP device needs to set the next hop to its IP address to prevent blackhole routes. Which of the following commands can be run in this case?