Assume that an AOS-CX switch is already implementing DHCP snooping and ARP inspection successfully on several VLANs.
What should you do to help minimize disruption time if the switch reboots?
What role can Internet Key Exchange (IKE)/IKEv2 play in an HPE Aruba Networking client-to-site VPN?
Refer to the Exhibit:
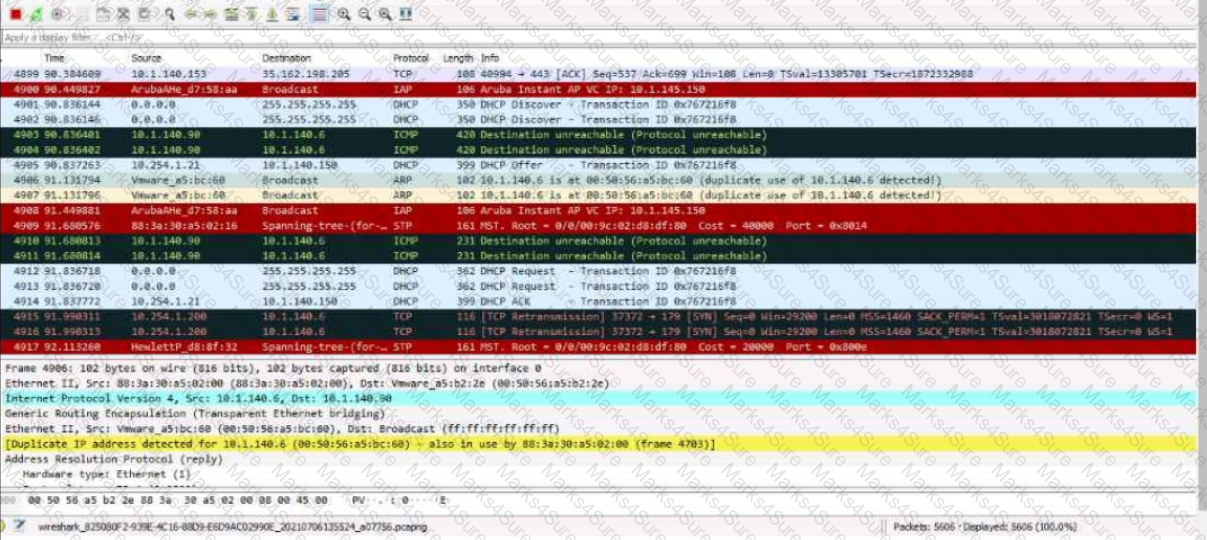
These packets have been captured from VLAN 10. which supports clients that receive their IP addresses with DHCP.
What can you interpret from the packets that you see here?
These packets have been captured from VLAN 10, which supports clients that receive their IP addresses with DHCP. What can you interpret from the packets that you see here?
Which use case is fulfilled by applying a time range to a firewall rule on an AOS device?
A company is using HPE Aruba Networking Central SD-WAN Orchestrator to establish a hub-spoke VPN between branch gateways (BGWs) at 1164 site and VPNCs at multiple data centers. What is part of the configuration that admins need to complete?
You manage AOS-10 APs with HPE Aruba Networking Central. A role is configured on these APs with the following rules:
Allow UDP on port 67 to any destination
Allow any to network 10.1.6.0/23
Deny any to network 10.1.0.0/16 + log
Deny any to network 10.0.0.0/8
Allow any to any destination
You add this new rule immediately before rule 2:
Deny SSH to network 10.1.4.0/23 + denylist
What happens when a client assigned to this role sends SSH traffic to 10.1.11.42?
A company is implementing a client-to-site VPN based on tunnel-mode IPsec.
Which devices are responsible for the IPsec encapsulation?
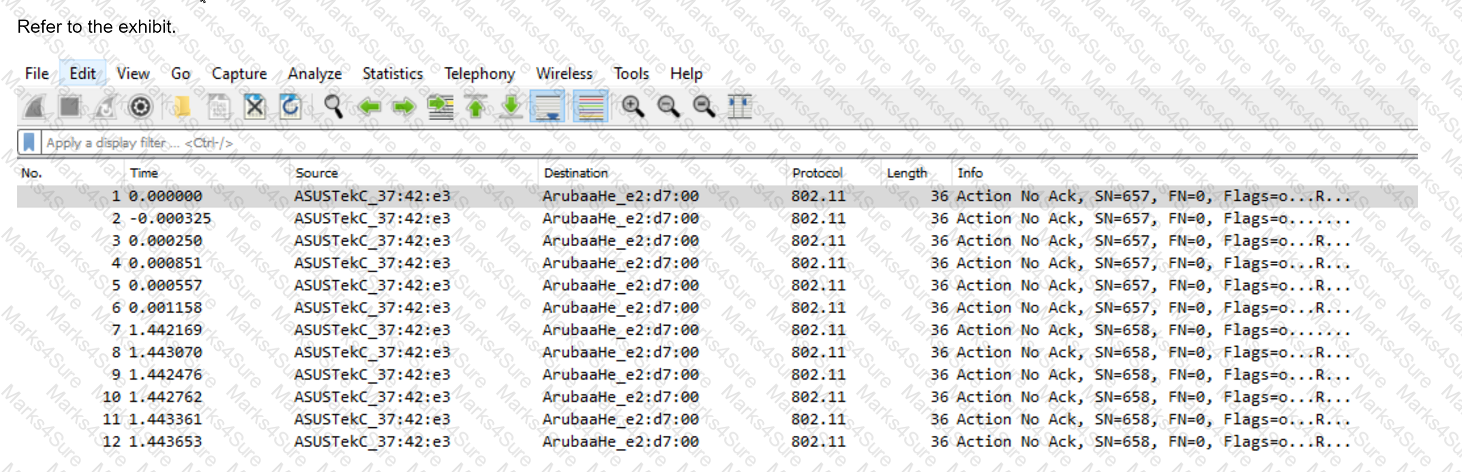
You have downloaded a packet capture that you generated on HPE Aruba Networking Central. When you open the capture in Wireshark, you see the output shown in the
exhibit.
What should you do in Wireshark so that you can better interpret the packets?
A company has a variety of HPE Aruba Networking solutions, including an HPE Aruba Networking infrastructure and HPE Aruba Networking ClearPass Policy
Manager (CPPM). The company passes traffic from the corporate LAN destined to the data center through a third-party SRX firewall. The company would like to
further protect itself from internal threats.
What is one solution that you can recommend?
A company has several use cases for using its AOS-CX switches' HPE Aruba Networking Network Analytics Engine (NAE).
What is one guideline to keep in mind as you plan?
A company has been running Gateway IDS/IPS on its gateways in IDS mode for several weeks. The company wants to transition to IPS mode.
What is one step you should recommend?
A company has HPE Aruba Networking APs running AOS-10 that connect to AOS-CX switches. The APs will:
Authenticate as 802.1X supplicants to HPE Aruba Networking ClearPass Policy Manager (CPPM)
Be assigned to the "APs" role on the switches
Have their traffic forwarded locally
What information do you need to help you determine the VLAN settings for the "APs" role?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as a TACACS+ server to authenticate managers on its AOS-CX switches. You want
to assign managers to groups on the AOS-CX switch by name.
How do you configure this setting in a CPPM TACACS+ enforcement profile?
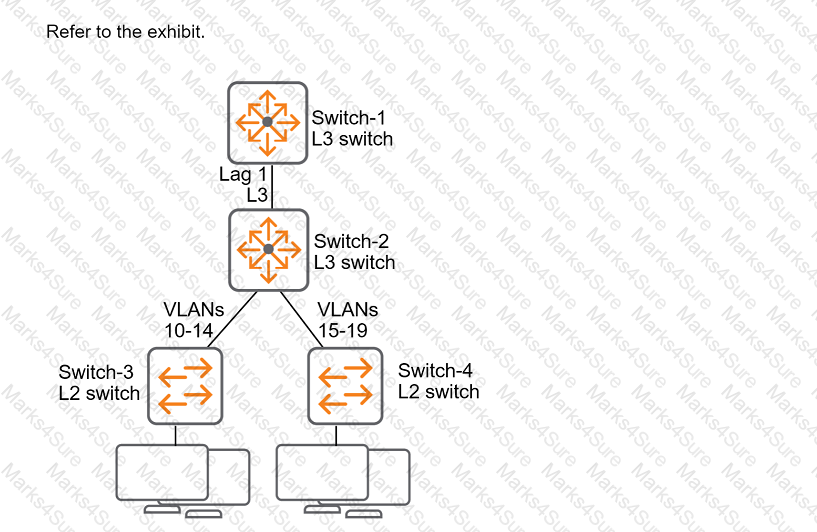
All of the switches in the exhibit are AOS-CX switches.
What is the preferred configuration on Switch-2 for preventing rogue OSPF routers in this network?
A company lacks visibility into the many different types of user and loT devices deployed in its internal network, making it hard for the security team to address
those devices.
Which HPE Aruba Networking solution should you recommend to resolve this issue?
Refer to Exhibit:
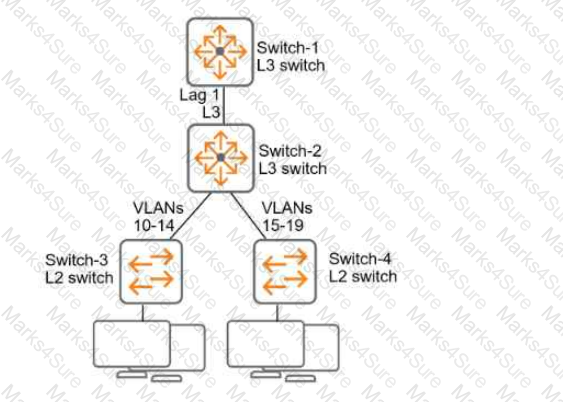
All of the switches in the exhibit are AOS-CX switches.
What is the preferred configuration on Switch-2 for preventing rogue OSPF routers in this network?
An AOS-CX switch has this admin user account configured on it:
netadmin in the operators group.
You have configured these commands on an AOS-CX switch:
tacacs-server host cp.example.com key plaintext &12xl,powmay7855
aaa authentication login ssh group tacacs local
aaa authentication allow-fail-through
A user accesses the switch with SSH and logs in as netadmin with the correct password. When the switch sends a TACACS+ request to the ClearPass server at cp.example.com, the server does not send a response. Authentication times out.
What happens?
A company has HPE Aruba Networking APs and AOS-CX switches, as well as HPE Aruba Networking ClearPass. The company wants CPPM to have HTTP User-
Agent strings to use in profiling devices.
What can you do to support these requirements?
A company wants to apply a standard configuration to all AOS-CX switch ports and have the ports dynamically adjust their configuration based on the identity of
the user or device that connects. They want to centralize configuration of the identity-based settings as much as possible.
What should you recommend?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) and HPE Aruba Networking ClearPass Device Insight (CPDI) and has integrated the
two. CPDI admins have created a tag. CPPM admins have created rules that use that tag in the wired 802.1X and wireless 802.1X services' enforcement policies.
The company requires CPPM to apply the tag-based rules to a client directly after it learns that the client has that tag.
What is one of the settings that you should verify on CPPM?
A company has HPE Aruba Networking APs (AOS-10), which authenticate clients to HPE Aruba Networking ClearPass Policy Manager (CPPM). CPPM is set up
to receive a variety of information about clients' profile and posture. New information can mean that CPPM should change a client's enforcement profile.
What should you set up on the APs to help the solution function correctly?
You are establishing a cluster of HPE Aruba Networking ClearPass servers. (Assume that they are running version 6.9.).
For which type of certificate is it recommended to install a CA-signed certificate on the Subscriber before it joins the cluster?
You have set up a mirroring session between an AOS-CX switch and a management station, running Wireshark. You want to capture just the traffic sent in the
mirroring session, not the management station's other traffic.
What should you do?
Admins have recently turned on Wireless IDS/IPS infrastructure detection at the high level on HPE Aruba Networking APs. When you check WIDS events, you
see several RTS rate and CTS rate anomalies, which were triggered by neighboring APs.
What can you interpret from this event?
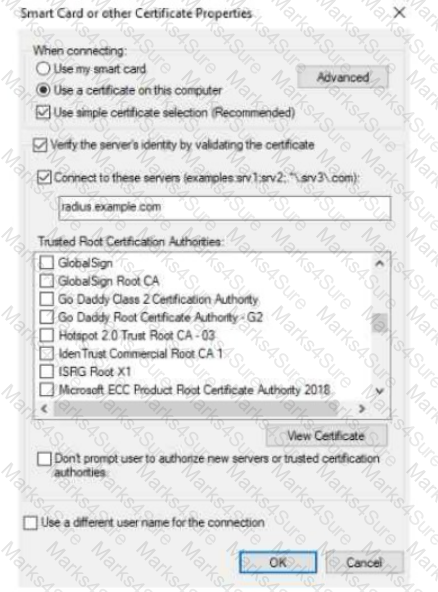
The exhibit shows the 802.1X-related settings for Windows domain clients. What should admins change to make the settings follow best security practices?
A company has a third-party security appliance deployed in its data center. The company wants to pass all traffic for certain clients through that device before forwarding that traffic toward its ultimate destination.
Which AOS-CX switch technology fulfills this use case?
A company needs you to integrate HPE Aruba Networking ClearPass Policy Manager (CPPM) with HPE Aruba Networking ClearPass Device Insight (CPDI). What is one task you should do to prepare?
You have created a Web-based Health Check Service that references a posture policy. You want the service to trigger a RADIUS change of authorization (CoA) when a client receives a Healthy or Quarantine posture. Where do you configure those rules?
A company has AOS-CX switches. The company wants to make it simpler and faster for admins to detect denial of service (DoS) attacks, such as ping or ARP
floods, launched against the switches.
What can you do to support this use case?
A company has AOS-CX switches, which authenticate clients to HPE Aruba Networking ClearPass Policy Manager (CPPM). CPPM is set up to receive a variety of information about clients' profile and posture. New information can mean that CPPM should change a client's enforcement profile. What should you set up on the switches to help the solution function correctly?
Refer to the exhibit.
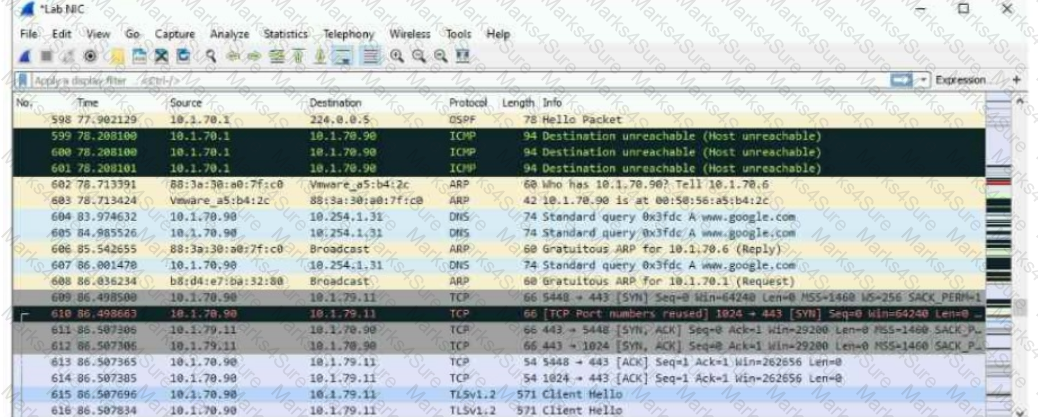
The exhibit shows a saved packet capture, which you have opened in Wireshark. You want to focus on the complete conversation between 10.1.70.90 and 10.1.79.11 that uses source port 5448.
What is a simple way to do this in Wireshark?
HPE Aruba Networking Central displays a Gateway Threat Count alert in the alert list. How can you gather more information about what caused the alert to trigger?
A company needs you to integrate HPE Aruba Networking ClearPass Policy Manager (CPPM) with HPE Aruba Networking ClearPass Device Insight (CPDI).
What is one task you should do to prepare?
You have configured an AOS-CX switch to implement 802.1X on edge ports. Assume ports operate in the default auth-mode. VolP phones are assigned to the
"voice" role and need to send traffic that is tagged for VLAN 12.
Where should you configure VLAN 12?