Click the Exhibit button.
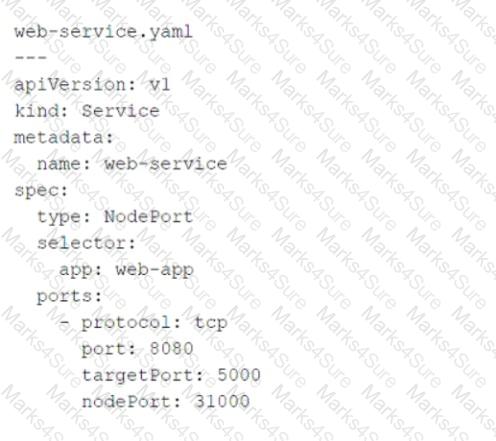
Referring to the exhibit, which port number would external users use to access the WEB application?
80
8080
31000
5000
The YAML file provided in the exhibit defines a KubernetesServiceobject of typeNodePort. Let’s break down the key components of the configuration and analyze how external users access the WEB application:
Key Fields in the YAML File:
type: NodePort:
This specifies that the service is exposed on a static port on each node in the cluster. External users can access the service using the node's IP address and the assignednodePort.
port: 8080:
This is the port on which the service is exposed internally within the Kubernetes cluster. Other services or pods within the cluster can communicate with this service using port8080.
targetPort: 5000:
This is the port on which the actual application (WEB application) is running inside the pod. The service forwards traffic fromport: 8080totargetPort: 5000.
nodePort: 31000:
This is the port on the node (host machine) where the service is exposed externally. External users will use this port to access the WEB application.
How External Users Access the WEB Application:
External users access the WEB application using the node's IP address and thenodePortvalue (31000).
The Kubernetes service listens on this port and forwards incoming traffic to the appropriate pods running the WEB application.
Why Not Other Options?
A. 80:Port80is commonly used for HTTP traffic, but it is not specified in the YAML file. The service does not expose port80externally.
B. 8080:Port8080is the internal port used within the Kubernetes cluster. It is not the port exposed to external users.
D. 5000:Port5000is the target port where the application runs inside the pod. It is not directly accessible to external users.
Why 31000?
NodePort Service Type:TheNodePortservice type exposes the application on a high-numbered port (default range: 30000–32767) on each node in the cluster.
External Accessibility:External users must use thenodePortvalue (31000) along with the node's IP address to access the WEB application.
JNCIA Cloud References:
The JNCIA-Cloud certification covers Kubernetes networking concepts, including service types likeClusterIP,NodePort, andLoadBalancer. Understanding howNodePortservices work is essential for exposing applications to external users in Kubernetes environments.
For example, Juniper Contrail integrates with Kubernetes to provide advanced networking features, such as load balancing and network segmentation, for services like the one described in the exhibit.
Which two tools are used to deploy a Kubernetes environment for testing and development purposes? (Choose two.)
OpenStack
kind
oc
minikube
Kubernetes is a popular container orchestration platform used for deploying and managing containerized applications. Several tools are available for setting up Kubernetes environments for testing and development purposes. Let’s analyze each option:
A. OpenStack
Incorrect: OpenStack is an open-source cloud computing platform used for managing infrastructure resources (e.g., compute, storage, networking). It is not specifically designed for deploying Kubernetes environments.
B. kind
Correct: kind (Kubernetes IN Docker) is a tool for running local Kubernetes clusters using Docker containers as nodes. It is lightweight and ideal for testing and development purposes.
C. oc
Incorrect: oc is the command-line interface (CLI) for OpenShift, a Kubernetes-based container platform. While OpenShift can be used to deploy Kubernetes environments, oc itself is not a tool for setting up standalone Kubernetes clusters.
D. minikube
Correct: minikube is a tool for running a single-node Kubernetes cluster locally on your machine. It is widely used for testing and development due to its simplicity and ease of setup.
Why These Tools?
kind: Ideal for simulating multi-node Kubernetes clusters in a lightweight environment.
minikube: Perfect for beginners and developers who need a simple, single-node Kubernetes cluster for experimentation.
JNCIA Cloud References:
The JNCIA-Cloud certification covers Kubernetes as part of its container orchestration curriculum. Tools like kind and minikube are essential for learning and experimenting with Kubernetes in local environments.
For example, Juniper Contrail integrates with Kubernetes to provide advanced networking and security features for containerized workloads. Proficiency with Kubernetes tools ensures effective operation and troubleshooting.
Which statement about software-defined networking is true?
It must manage networks through the use of containers and repositories.
It manages networks by separating the data forwarding plane from the control plane.
It applies security policies individually to each separate node.
It manages networks by merging the data forwarding plane with the control plane.
Software-Defined Networking (SDN) is a revolutionary approach to network management that separates the control plane from the data (forwarding) plane. Let’s analyze each option:
A. It must manage networks through the use of containers and repositories.
Incorrect:While containers and repositories are important in cloud-native environments, they are not a requirement for SDN. SDN focuses on programmability and centralized control, not containerization.
B. It manages networks by separating the data forwarding plane from the control plane.
Correct:SDN separates the control plane (decision-making) from the data forwarding plane (packet forwarding). This separation enables centralized control, programmability, and dynamic network management.
C. It applies security policies individually to each separate node.
Incorrect:SDN applies security policies centrally through the SDN controller, not individually to each node. Centralized policy enforcement is one of the key advantages of SDN.
D. It manages networks by merging the data forwarding plane with the control plane.
Incorrect:Merging the forwarding and control planes contradicts the fundamental principle of SDN. The separation of these planes is what enables SDN’s flexibility and programmability.
Why This Answer?
Separation of Planes:By decoupling the control plane from the forwarding plane, SDN enables centralized control over network devices. This architecture simplifies network management, improves scalability, and supports automation.
JNCIA Cloud References:
The JNCIA-Cloud certification covers SDN as a core concept in cloud networking. Understanding the separation of the control and forwarding planes is essential for designing and managing modern cloud environments.
For example, Juniper Contrail serves as an SDN controller, centralizing control over network devices and enabling advanced features like network automation and segmentation.
You must provide tunneling in the overlay that supports multipath capabilities.
Which two protocols provide this function? (Choose two.)
MPLSoGRE
VXLAN
VPN
MPLSoUDP
In cloud networking, overlay networks are used to create virtualized networks that abstract the underlying physical infrastructure. To supportmultipath capabilities, certain protocols provide efficient tunneling mechanisms. Let’s analyze each option:
A. MPLSoGRE
Incorrect:MPLS over GRE (MPLSoGRE) is a tunneling protocol that encapsulates MPLS packets within GRE tunnels. While it supports MPLS traffic, it does not inherently provide multipath capabilities.
B. VXLAN
Correct:VXLAN (Virtual Extensible LAN) is an overlay protocol that encapsulates Layer 2 Ethernet frames within UDP packets. It supports multipath capabilities by leveraging the Equal-Cost Multi-Path (ECMP) routing in the underlay network. VXLAN is widely used in cloud environments for extending Layer 2 networks across data centers.
C. VPN
Incorrect:Virtual Private Networks (VPNs) are used to securely connect remote networks or users over public networks. They do not inherently provide multipath capabilities or overlay tunneling for virtual networks.
D. MPLSoUDP
Correct:MPLS over UDP (MPLSoUDP) is a tunneling protocol that encapsulates MPLS packets within UDP packets. Like VXLAN, it supports multipath capabilities by utilizing ECMP in the underlay network. MPLSoUDP is often used in service provider environments for scalable and flexible network architectures.
Why These Protocols?
VXLAN:Provides Layer 2 extension and supports multipath forwarding, making it ideal for large-scale cloud deployments.
MPLSoUDP:Combines the benefits of MPLS with UDP encapsulation, enabling efficient multipath routing in overlay networks.
JNCIA Cloud References:
The JNCIA-Cloud certification covers overlay networking protocols like VXLAN and MPLSoUDP as part of its curriculum on cloud architectures. Understanding these protocols is essential for designing scalable and resilient virtual networks.
For example, Juniper Contrail uses VXLAN to extend virtual networks across distributed environments, ensuring seamless communication and high availability.
Which virtualization method requires less duplication of hardware resources?
OS-level virtualization
hardware-assisted virtualization
full virtualization
paravirtualization
Virtualization methods differ in how they utilize hardware resources. Let’s analyze each option:
A. OS-level virtualization
Correct: OS-level virtualization (e.g., containers) uses the host operating system’s kernel to run isolated user-space instances (containers). Since containers share the host OSkernel, there is less duplication of hardware resources compared to other virtualization methods.
B. hardware-assisted virtualization
Incorrect: Hardware-assisted virtualization (e.g., Intel VT-x, AMD-V) enables full virtual machines (VMs) to run on physical hardware. Each VM includes its own operating system, leading to duplication of resources like memory and CPU.
C. full virtualization
Incorrect: Full virtualization involves running a complete guest operating system on top of a hypervisor. Each VM requires its own OS, resulting in significant resource duplication.
D. paravirtualization
Incorrect: Paravirtualization modifies the guest operating system to communicate directly with the hypervisor. While it reduces some overhead compared to full virtualization, it still requires separate operating systems for each VM, leading to resource duplication.
Why OS-Level Virtualization?
Resource Efficiency: Containers share the host OS kernel, eliminating the need for multiple operating systems and reducing resource duplication.
Lightweight: Containers are faster to start and consume fewer resources compared to VMs.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding virtualization technologies, including OS-level virtualization. Containers are a key component of modern cloud-native architectures due to their efficiency and scalability.
For example, Juniper Contrail integrates with container orchestration platforms like Kubernetes to manage OS-level virtualization workloads efficiently.
Theopenstack user listcommand uses which OpenStack service?
Cinder
Keystone
Nova
Neutron
OpenStack provides various services to manage cloud infrastructure resources, including user management. Let’s analyze each option:
A. Cinder
Incorrect: Cinderis the OpenStack block storage service that provides persistent storage volumes for virtual machines. It is unrelated to managing users.
B. Keystone
Correct: Keystoneis the OpenStack identity service responsible for authentication, authorization, and user management. Theopenstack user listcommand interacts with Keystone to retrieve a list of users in the OpenStack environment.
C. Nova
Incorrect: Novais the OpenStack compute service that manages virtual machine instances. It does not handle user management.
D. Neutron
Incorrect: Neutronis the OpenStack networking service that manages virtual networks, routers, and IP addresses. It is unrelated to user management.
Why Keystone?
Identity Management:Keystone serves as the central identity provider for OpenStack, managing users, roles, and projects.
API Integration:Commands likeopenstack user listrely on Keystone's APIs to query and display user information.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenStack services, including Keystone, as part of its cloud infrastructure curriculum. Understanding Keystone’s role in user management is essential for operating OpenStack environments.
For example, Juniper Contrail integrates with OpenStack Keystone to enforce authentication and authorization for network resources.
Which cloud service model provides access to networking, storage, servers, and virtualization in a cloud environment?
Platform as a Service (PaaS)
Software as a Service (SaaS)
Infrastructure as a Service (IaaS)
Database as a Service (DaaS)
Cloud service models define how services are delivered and managed in a cloud environment. The three primary models are:
Infrastructure as a Service (IaaS): Provides virtualized computing resources such as servers, storage, networking, and virtualization over the internet. Customers manage their own operating systems, applications, and data, while the cloud provider manages the underlying infrastructure.
Platform as a Service (PaaS): Provides a platform for developers to build, deploy, and manage applications without worrying about the underlying infrastructure. Examples include Google App Engine and Microsoft Azure App Services.
Software as a Service (SaaS): Delivers fully functional applications over the internet, eliminating the need for users to install or maintain software locally. Examples include Salesforce CRM, Google Workspace, and Microsoft Office 365.
Database as a Service (DaaS): A specialized subset of PaaS that provides managed database services.
In this question, the focus is on access to networking, storage, servers, and virtualization , which are the core components of IaaS . IaaS allows customers to rent infrastructure on-demand and build their own environments without investing in physical hardware.
Why IaaS?
Flexibility: Customers have full control over the operating systems, applications, and configurations.
Scalability: Resources can be scaled up or down based on demand.
Cost Efficiency: Pay-as-you-go pricing eliminates upfront hardware costs.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding the different cloud service models and their use cases. IaaS is particularly relevant for organizations that want to leverage cloud infrastructure while maintaining control over their applications and data.
For example, Juniper Contrail integrates with IaaS platforms like OpenStack to provide advanced networking and security features for virtualized environments.
Which Kubernetes component guarantees the availability of ReplicaSet pods on one or more nodes?
kube-proxy
kube-scheduler
kube controller
kubelet
Kubernetes components work together to ensure the availability and proper functioning of resources like ReplicaSets. Let’s analyze each option:
A. kube-proxy
Incorrect:Thekube-proxymanages network communication for services and pods by implementing load balancing and routing rules. It does not guarantee the availability of ReplicaSet pods.
B. kube-scheduler
Incorrect:Thekube-scheduleris responsible for assigning pods to nodes based on resource availability and other constraints. While it plays a role in pod placement, it does not ensure the availability of ReplicaSet pods.
C. kube controller
Correct:Thekube controller(specifically the ReplicaSet controller) ensures that the desired number of pods specified in a ReplicaSet are running at all times. If a pod crashes or is deleted, the controller creates a new one to maintain the desired state.
D. kubelet
Incorrect:Thekubeletensures that containers are running as expected on a node but does not manage the overall availability of ReplicaSet pods across the cluster.
Why Kube Controller?
ReplicaSet Management:The ReplicaSet controller within the kube controller manager ensures that the specified number of pod replicas are always available.
Self-Healing:If a pod fails or is deleted, the controller automatically creates a new pod to maintain the desired state.
JNCIA Cloud References:
The JNCIA-Cloud certification covers Kubernetes control plane components, including the kube controller. Understanding the role of the kube controller is essential for managing the availability and scalability of Kubernetes resources.
For example, Juniper Contrail integrates with Kubernetes to provide advanced networking and security features, relying on the kube controller to maintain the desired state of ReplicaSets.
Which two statements are correct about Kubernetes resources? (Choose two.)
A ClusterIP type service can only be accessed within a Kubernetes cluster.
A daemonSet ensures that a replica of a pod is running on all nodes.
A deploymentConfig is a Kubernetes resource.
NodePort service exposes the service externally by using a cloud provider load balancer.
Kubernetes resources are the building blocks of Kubernetes clusters, enabling the deployment and management of applications. Let’s analyze each statement:
A. A ClusterIP type service can only be accessed within a Kubernetes cluster.
Correct:
AClusterIPservice is the default type of Kubernetes service. It exposes the service internally within the cluster, assigning it a virtual IP address that is accessible only to other pods or services within the same cluster. External access is not possible with this service type.
B. A daemonSet ensures that a replica of a pod is running on all nodes.
Correct:
AdaemonSetensures that a copy of a specific pod is running on every node in the cluster (or a subset of nodes if specified). This is commonly used for system-level tasks like logging agents or monitoring tools that need to run on all nodes.
C. A deploymentConfig is a Kubernetes resource.
Incorrect:
deploymentConfigis a concept specific to OpenShift, not standard Kubernetes. In Kubernetes, the equivalent resource is called aDeployment, which manages the desired state of pods and ReplicaSets.
D. NodePort service exposes the service externally by using a cloud provider load balancer.
Incorrect:
ANodePortservice exposes the service on a static port on each node in the cluster, allowing external access via the node's IP address and the assigned port. However, it does not use a cloud provider load balancer. TheLoadBalancerservice type is the one that leverages cloud provider load balancers for external access.
Why These Statements?
ClusterIP:Ensures internal-only communication, making it suitable for backend services that do not need external exposure.
DaemonSet:Guarantees that a specific pod runs on all nodes, ensuring consistent functionality across the cluster.
JNCIA Cloud References:
The JNCIA-Cloud certification covers Kubernetes resources and their functionalities, including services, DaemonSets, and Deployments. Understanding these concepts is essential for managing Kubernetes clusters effectively.
For example, Juniper Contrail integrates with Kubernetes to provide advanced networking features for services and DaemonSets, ensuring seamless operation of distributed applications.
Which two consoles are provided by the OpenShift Web UI? (Choose two.)
administrator console
developer console
operational console
management console
OpenShift provides a web-based user interface (Web UI) that offers two distinct consoles tailored to different user roles. Let’s analyze each option:
A. administrator console
Correct:
Theadministrator consoleis designed for cluster administrators. It provides tools for managing cluster resources, configuring infrastructure, monitoring performance, and enforcing security policies.
B. developer console
Correct:
Thedeveloper consoleis designed for application developers. It focuses on building, deploying, and managing applications, including creating projects, defining pipelines, and monitoring application health.
C. operational console
Incorrect:
There is no "operational console" in OpenShift. This term does not correspond to any official OpenShift Web UI component.
D. management console
Incorrect:
While "management console" might sound generic, OpenShift specifically refers to the administrator console for management tasks. This term is not officially used in the OpenShift Web UI.
Why These Consoles?
Administrator Console:Provides a centralized interface for managing the cluster's infrastructure and ensuring smooth operation.
Developer Console:Empowers developers to focus on application development without needing to interact with low-level infrastructure details.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding OpenShift's Web UI and its role in cluster management and application development. Recognizing the differences between the administrator and developer consoles is essential for effective collaboration in OpenShift environments.
For example, Juniper Contrail integrates with OpenShift to provide advanced networking features, leveraging both consoles for seamless operation.
What are the two characteristics of the Network Functions Virtualization (NFV) framework? (Choose two.)
It implements virtualized tunnel endpoints
It decouples the network software from the hardware.
It implements virtualized network functions
It decouples the network control plane from the forwarding plane.
Network Functions Virtualization (NFV) is a framework designed to virtualize network services traditionally run on proprietary hardware. NFV aims to reduce costs, improve scalability, and increase flexibility by decoupling network functions from dedicated hardware appliances. Let’s analyze each statement:
A. It implements virtualized tunnel endpoints.
Incorrect:While NFV can support virtualized tunnel endpoints (e.g., VXLAN gateways), this is not a defining characteristic of the NFV framework. Tunneling protocols are typically associated with SDN or overlay networks rather than NFV itself.
B. It decouples the network software from the hardware.
Correct:One of the primary goals of NFV is to separate network functions (e.g., firewalls, load balancers, routers) from proprietary hardware. Instead, these functions are implemented as software running on standard servers or virtual machines.
C. It implements virtualized network functions.
Correct:NFV replaces traditional hardware-based network appliances with virtualized network functions (VNFs). Examples include virtual firewalls, virtual routers, and virtual load balancers. These VNFs run on commodity hardware and are managed through orchestration platforms.
D. It decouples the network control plane from the forwarding plane.
Incorrect:Decoupling the control plane from the forwarding plane is a characteristic of Software-Defined Networking (SDN), not NFV. While NFV and SDN are complementary technologies, they serve different purposes. NFV focuses on virtualizing network functions, while SDN focuses on programmable network control.
JNCIA Cloud References:
The JNCIA-Cloud certification covers NFV as part of its discussion on cloud architectures and virtualization. NFV is particularly relevant in modern cloud environments because it enables flexible and scalable deployment of network services without reliance on specialized hardware.
For example, Juniper Contrail integrates with NFV frameworks to deploy and manage VNFs, enabling service providers to deliver network services efficiently and cost-effectively.
You just uploaded a qcow2 image of a vSRX virtual machine in OpenStack.
In this scenario, which service stores the virtual machine (VM) image?
Glance
Ironic
Neutron
Nova
OpenStack provides various services to manage cloud infrastructure resources, including virtual machine (VM) images. Let’s analyze each option:
A. Glance
Correct: Glanceis the OpenStack service responsible for managing and storing VM images. It provides a repository for uploading, discovering, and retrieving images in various formats, such as qcow2, raw, or ISO.
B. Ironic
Incorrect: Ironicis the OpenStack bare-metal provisioning service. It is used to manage physical servers, not VM images.
C. Neutron
Incorrect: Neutronis the OpenStack networking service that manages virtual networks, routers, and IP addresses. It does not store VM images.
D. Nova
Incorrect: Novais the OpenStack compute service that manages the lifecycle of virtual machines. While Nova interacts with Glance to retrieve VM images for deployment, it does not store the images itself.
Why Glance?
Image Repository:Glance acts as the central repository for VM images, enabling users to upload, share, and deploy images across the OpenStack environment.
Integration with Nova:When deploying a VM, Nova retrieves the required image from Glance to create the instance.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenStack services, including Glance, as part of its cloud infrastructure curriculum. Understanding Glance’s role in image management is essential for deploying and managing virtual machines in OpenStack.
For example, Juniper Contrail integrates with OpenStack Glance to provide advanced networking features for VM images stored in the repository.
Which component of Kubernetes runs on each node maintaining network rules?
container runtime
kube-proxy
kubelet
kube controller
Kubernetes components work together to ensure seamless communication and network functionality within the cluster. Let’s analyze each option:
A. container runtime
Incorrect:The container runtime (e.g.,containerd,cri-o) is responsible for running containers on worker nodes. It does not maintain network rules.
B. kube-proxy
Correct: kube-proxyis a Kubernetes component that runs on each node and maintains network rules to enable communication between services and pods. It ensures proper load balancing and routing of traffic.
C. kubelet
Incorrect:Thekubeletis responsible for managing the state of pods and containers on a node. It does not handle network rules.
D. kube controller
Incorrect:Thekube controllermanages the desired state of the cluster, such as maintaining the correct number of replicas. It does not directly manage network rules.
Why kube-proxy?
Network Rules:kube-proxy implements iptables or IPVS rules to route traffic between services and pods, ensuring seamless communication.
Load Balancing:It provides basic load balancing for services, distributing traffic across available pods.
JNCIA Cloud References:
The JNCIA-Cloud certification covers Kubernetes networking, including the role of kube-proxy. Understanding how kube-proxy works is essential for managing network communication in Kubernetes clusters.
For example, Juniper Contrail integrates with Kubernetes to enhance networking capabilities, leveraging kube-proxy for service-level traffic management.
What is the name of the Docker container runtime?
docker_cli
containerd
dockerd
cri-o
Docker is a popular containerization platform that relies on a container runtime to manage the lifecycle of containers. The container runtime is responsible for tasks such as creating, starting, stopping, and managing containers. Let’s analyze each option:
A. docker_cli
Incorrect: The Docker CLI (Command Line Interface) is a tool used to interact with the Docker daemon (dockerd). It is not a container runtime but rather a user interface for managing Docker containers.
B. containerd
Correct: containerd is the default container runtime used by Docker. It is a lightweight, industry-standard runtime that handles low-level container management tasks, such as image transfer, container execution, and lifecycle management. Docker delegates these tasks to containerd through the Docker daemon.
C. dockerd
Incorrect: dockerd is the Docker daemon, which manages Docker objects such as images, containers, networks, and volumes. While dockerd interacts with the container runtime, it is not the runtime itself.
D. cri-o
Incorrect: cri-o is an alternative container runtime designed specifically for Kubernetes. It implements the Kubernetes Container Runtime Interface (CRI) and is not used by Docker.
Why containerd?
Industry Standard: containerd is a widely adopted container runtime that adheres to the Open Container Initiative (OCI) standards.
Integration with Docker: Docker uses containerd as its default runtime, making it the correct answer in this context.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding containerization technologies and their components. Docker and its runtime (containerd) are foundational tools in modern cloud environments, enabling lightweight, portable, and scalable application deployment.
For example, Juniper Contrail integrates with container orchestration platforms like Kubernetes, which often use containerd as the underlying runtime. Understanding container runtimes is essential for managing containerized workloads in cloud environments.
Which OpenShift resource represents a Kubernetes namespace?
Project
ResourceQuota
Build
Operator
OpenShift is a Kubernetes-based container platform that introduces additional abstractions and terminologies. Let’s analyze each option:
A. Project
Correct:
In OpenShift, aProjectrepresents a Kubernetes namespace with additional capabilities. It provides a logical grouping of resources and enables multi-tenancy by isolating resources between projects.
B. ResourceQuota
Incorrect:
AResourceQuotais a Kubernetes object that limits the amount of resources (e.g., CPU, memory) that can be consumed within a namespace. While it is used within a project, it is not the same as a namespace.
C. Build
Incorrect:
ABuildis an OpenShift-specific resource used to transform source code into container images. It is unrelated to namespaces or projects.
D. Operator
Incorrect:
AnOperatoris a Kubernetes extension that automates the management of complex applications. It operates within a namespace but does not represent a namespace itself.
Why Project?
Namespace Abstraction:OpenShift Projects extend Kubernetes namespaces by adding features like user roles, quotas, and lifecycle management.
Multi-Tenancy:Projects enable organizations to isolate workloads and resources for different teams or applications.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenShift and its integration with Kubernetes. Understanding the relationship between Projects and namespaces is essential for managing OpenShift environments.
For example, Juniper Contrail integrates with OpenShift to provide advanced networking and security features for Projects, ensuring secure and efficient resource isolation.
You want to create a template that defines the CPU, RAM, and disk space properties that a VM will use when instantiated.
In this scenario, which OpenStack object should you create?
role
Image
project
flavor
In OpenStack, aflavordefines the compute, memory, and storage properties of a virtual machine (VM) instance. Let’s analyze each option:
A. role
Incorrect:Aroledefines permissions and access levels for users within a project. It is unrelated to defining VM properties.
B. Image
Incorrect:Animageis a template used to create VM instances. While images define the operating system and initial configuration, they do not specify CPU, RAM, or disk space properties.
C. project
Incorrect:Aproject(or tenant) represents an isolated environment for managing resources. It does not define the properties of individual VMs.
D. flavor
Correct:Aflavorspecifies the CPU, RAM, and disk space properties that a VM will use when instantiated. For example, a flavor might define a VM with 2 vCPUs, 4 GB of RAM, and 20 GB of disk space.
Why Flavor?
Resource Specification:Flavors allow administrators to define standardized resource templates for VMs, ensuring consistency and simplifying resource allocation.
Flexibility:Users can select the appropriate flavor based on their workload requirements, making it easy to deploy VMs with predefined configurations.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenStack concepts, including flavors, as part of its cloud infrastructure curriculum. Understanding how flavors define VM properties is essential for managing compute resources effectively.
For example, Juniper Contrail integrates with OpenStack Nova to provide advanced networking features for VMs deployed using specific flavors.

TESTED 24 Apr 2025

