A remote monitoring system is unable to protect an organisation from which of the following risks?
Which of the following approaches to cyber security takes a bottom-up approach to assessing vulnerabilities meticulously item by item?
Fluffy Pillows Ltd has recently expanded its operations and has hired more staff. These staff will work remotely and because of this Fluffy Pillows Ltd is in need of buying and upgrading their IT systems. The CEO of Fluffy Pillows is examining the security of currently held data in preparation for the expansion and has recently completed a document which looks into what data is stored where and what the consequences would be if this data were to be stolen or corrupted. In his research he has found multiple data entries for the same information, which he believes could lead to inaccuracies in data reporting. He is also concerned that the data isn't being stored securely and is unsure whether he should retain some of the confidential personal details on employees who have left the business. He has decided that along with the introduction of new systems it is important that all members of staff at Fluffy Pillows are aware of the responsibilities of storing data correctly and the risks of cyber attacks.
What is the main legal concern regarding the data?
It is important for all Procurement and Supply Chain professionals to use Big Data in order to create efficiencies. Is this statement TRUE?
Bruno is the newly appointed Head of Operations of a manufacturing organisation based in Coventry that makes children's toys. The company was established in 1958 and has many years of records of toys sold. Some of the early records are paper-based, but data from the 1990s onwards is computer-based. Bruno believes that as the company acquired the data legally, it should be stored in the office and can be used for marketing purposes. Is this true?
Jamila is the Head of Procurement at Big Smiles Ltd. A few years ago, e-procurement systems were introduced, which has led to huge efficiency and transparency gains for the organisation. The tools that Jamila's team use include a PO system and supplier KPI monitoring system, which are accessed through a web portal. Which of the following statements are true?
Henry is the Head of IT at Purple Rain Ltd and is presenting a case to the Senior Leadership Team to ask for more investment in the company's IT strategy. Henry believes the company has an issue with data resilience and is asking for more money to be invested in this. He has completed a Business Impact Assessment (BIA) to better understand what data the company holds. Jon is the Head of Procurement and has listened intently to Henry's presentation. He has decided to go back to his department and complete a thorough risk assessment, as he is aware his team holds a lot of data on suppliers and contracts. The CEO of Purple Rain, Roger Nelson, has asked Henry about next steps in order to protect the company from further risks associated with the IT strategy. Data is currently stored on servers located at Purple Rain's Headquarters. The server room is locked at all times of the day and is only accessible to staff members who have a key. The building itself is extremely secure with CCTV systems located both inside the server room and outside it. However, the server room is prone to overheating.
What would Henry's BIA show?
The Data Protection Act covers any data that is input or held on a computer and does not cover paper filing systems. Is this TRUE?
The use of data to predict future demand and adjust prices accordingly is known as what?
The speed at which data can be transferred and accessed over the internet is known as … ?
Henry is the Head of IT at Purple Rain Ltd and is presenting a case to the Senior Leadership Team to ask for more investment in the company's IT strategy. Henry believes the company has an issue with data resilience and is asking for more money to be invested in this. He has completed a Business Impact Assessment (BIA) to better understand what data the company holds. Jon is the Head of Procurement and has listened intently to Henry's presentation. He has decided to go back to his department and complete a thorough risk assessment, as he is aware his team holds a lot of data on suppliers and contracts. The CEO of Purple Rain, Roger Nelson, has asked Henry about next steps in order to protect the company from further risks associated with the IT strategy. Data is currently stored on servers located at Purple Rain's Headquarters. The server room is locked at all times of the day and is only accessible to staff members who have a key. The building itself is extremely secure with CCTV systems located both inside the server room and outside it. However, the server room is prone to overheating.
What is Henry's primary concern?
IT hacking can take many forms, and it is important for Procurement professionals to be aware of different ways their data can be compromised or stolen through cyber attacks. Which of the following is not a type of cyber attack?
Henry is the Head of IT at Purple Rain Ltd and is presenting a case to the Senior Leadership Team to ask for more investment in the company's IT strategy. Henry believes the company has an issue with data resilience and is asking for more money to be invested in this. He has completed a Business Impact Assessment (BIA) to better understand what data the company holds. Jon is the Head of Procurement and has listened intently to Henry's presentation. He has decided to go back to his department and complete a thorough risk assessment, as he is aware his team holds a lot of data on suppliers and contracts. The CEO of Purple Rain, Roger Nelson, has asked Henry about next steps in order to protect the company from further risks associated with the IT strategy. Data is currently stored on servers located at Purple Rain's Headquarters. The server room is locked at all times of the day and is only accessible to staff members who have a key. The building itself is extremely secure with CCTV systems located both inside the server room and outside it. However, the server room is prone to overheating.
What should Henry's next steps be?
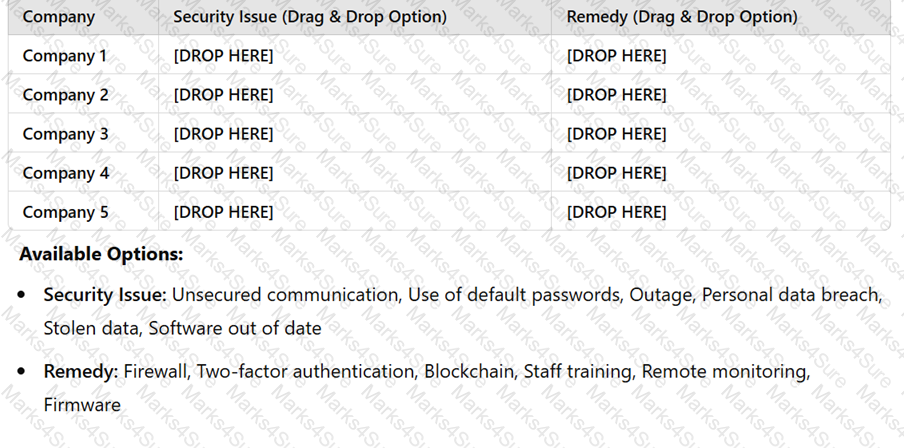
Below are details of five companies that have security issues related to their IT network or data storage. Each company is proposing a remedy to resolve the issue.
Instructions:
Drag and drop the correct Security Issue and Remedy into the table for each company. Some options may not be used.
In order to increase security at the Local Council building, the Local Council has decided to implement biometrics. What employee information would be required for this to be implemented?