A network engineer needs to deploy an access point at a remote office so that it will not communicate back to the wireless LAN controller. Which of the following deployment methods must the engineer use to accomplish this task?
A network engineer configures a new switch and connects it to an existing switch for expansion and redundancy. Users immediately lose connectivity to the network. The network engineer notes the following spanning tree information from both switches:
Switch 1
Port State Cost
1 Forward 2
2 Forward 2
Switch 2
Port State Cost
1 Forward 2
2 Forward 2
Which of the following best describes the issue?
A network administrator deploys several new desk phones and workstation cubicles. Each cubicle has one assigned switchport. The administrator runs the following commands:
nginx
CopyEdit
switchport mode access
switchport voice vlan 69
With which of the following VLANs will the workstation traffic be tagged?
Which of the following physical installation factors is the most important when a network switch is installed in a sealed enclosure?
A company implements a new network utilizing only IPv6 addressing and needs to connect to the internet. Which of the following must be enabled in order for the internal network to contact servers on the internet?
A technician is deploying new networking hardware for company branch offices. The bridge priority must be properly set. Which of the following should the technician configure?
Which of the following routing technologies uses an attribute list for path selection?
A technician is planning an equipement installation into a rack in a data center that practices hot aisle/cold aise ventilation. Which of the following directions should the equipement exhaust face when installed in the rack?
A newtwork administrator needs to create an SVI on a Layer 3-capable device to separate voice and data traffic. Which of the following best explains this use case?
An organization is struggling to get effective coverage using the wireless network. The organization wants to implement a solution that allows for continuous connectivity anywhere in the facility. Which of the following should the network administrator suggest to ensure the best coverage?
A network engineer discovers network traffic that is sending confidential information to an unauthorized and unknown destination. Which of the following best describes the cause of this network traffic?
Which of the following concepts describes the idea of housing different customers in the same public cloud data center?
A company is implementing a new internal network in which all devices use IPv6 addresses. Which of the following routing protocols will be best for this setup?
Which of the following is the most cost-effective way for a network administrator to establish a persistent, secure connection between two facilities?
A technician is planning an equipment installation into a rack in a data center that practices hot aisle/cold aisle ventilation. Which of the following directions should the equipment exhaust face when installed in the rack?
Which of the following are the best device-hardening techniques for network security? (Select two).
A user notifies a network administrator about losing access to a remote file server. The network administrator is able to ping the server and verifies the current firewall rules do not block access to the network fileshare. Which of the following tools wold help identify which ports are open on the remote file server?
A network administrator wants to restrict inbound traffic to allow only HTTPS to the company website, denying all other inbound traffic from the internet. Which of the following would best accomplish this goal?
Users cannot connect to an internal website with an IP address 10.249.3.76. A network administrator runs a command and receives the following output:
1 3ms 2ms 3ms 192.168.25.234
2 2ms 3ms 1ms 192.168.3.100
3 4ms 5ms 2ms 10.249.3.1
4 *
5 ’
6 *
7 •
Which of the following command-line tools is the network administrator using?
A systems administrator is looking for operating system information, running services, and network ports that are available on a server. Which of the following software tools should the administrator use to accomplish this task?
A network technician installs a new 19.7ft (6m), Cat 6, UTP cable for the connection between a server and a switch. Communication to the server is degraded, and the NIC statistics show dropped packets and CRC errors. Which of the following cables would the technician most likely use instead to reduce the errors?
Which of the following VPN configurations forces a remote user to access internet resources through the corporate network?
A company is purchasing a 40Gbps broadband connection service from an ISP. Which of the following should most likely be configured on the 10G switch to take advantage of the new service?
A major natural disaster strikes a company ' s headquarters, causing significant destruction and data loss. The company needs to quickly recover and resume operations. Which of the following will a network administrator need to do first?
A small business is choosing between static and dynamic routing for its network. Which of the following is the best reason to use dynamic routing in a growing network?
A technician needs to quickly set up a network with five wireless devices. Which of the following network types should the technician configure to accomplish this task?
A network administrator needs a solution to isolate and potentially identify any threat actors that are attempting to breach the network. Which of the following should the administrator implement to determine the type of attack used?
Which of the following OSI model layers can utilize a connectionless protocol for data transmission?
A network technician is installing a new switch that does not support STP at the access layer of a network. The technician wants a redundant connection to the distribution switch. Which of the following should the technician use?
Which of the following offers the ability to manage access at the cloud VM instance?
A network engineer added more APs to improve wireless coverage. However, users now report that the connectivity disconnects and reconnects repeatedly. Which of the following is causing the issue?
A network manager connects two switches together and uses two connecting links. Which of the following configurations will prevent Layer 2 loops?
A network administrator is responding to a request to configure a new IP phone. Which of the following should the network administrator do to allow data and voice traffic to be properly prioritized?
A user tries to visit a website, but instead of the intended site, the page displays vmw.cba.com. Which of the following should be done to reach the correct website?
A network administrator is trying to troubleshoot an issue with a newly installed switch that is not connecting to the network. The administrator logs on to the switch and observes collisions on the interface. Which of the following is most likely the issue?
A network administrator is configuring a network for a new site that will have 150 users. Within the next year, the site is expected to grow by ten users. Each user will have two IP addresses, one for a computer and one for a phone connected to the network. Which of the following classful IPv4 address ranges will be best-suited for the network?
A company is hosting a secure that requires all connections to the server to be encrypted. A junior administrator needs to harded the web server. The following ports on the web server. The following ports on the web server are open:

Which of the following ports should be disabled?
Which of the following attacks forces a switch to send all traffic out of all ports?
A client wants to increase overall security after a recent breach. Which of the following would be best to implement? (Select two.)
A new staff member is unable to connect to the network. An IT support staff member finds the following:
The IP configuration is correct.
The TCP/IP stack is working on the workstation.
The gateway is unreachable.
Which of the following would the IT support staff member most likely check next?
Which of the following allows a user to authenticate to multiple resources without requiring additional passwords?
Which of the following requires network devices to be managed using a different set of IP addresses?
A technician needs to identify a computer on the network that is reportedly downloading unauthorized content. Which of the following should the technician use?
Users are experiencing significant lag while connecting to a cloud-based application during peak hours. An examination of the network reveals that the bandwidth is being heavily utilized. Further analysis shows that only a few users are using the application at any given time. Which of the following is the most cost-effective solution for this issue?
Following a fire in a data center, the cabling was replaced. Soon after, an administrator notices network issues. Which of the following are the most likely causes of the network issues? (Select two).
Which of the following allows a network administrator to analyze attacks coming from the internet without affecting latency?
Which of the following appliances provides users with an extended footprint that allows connections from multiple devices within a designated WLAN?
After providing a username and password, a user must input a passcode from a phone application. Which of the following authentication technologies is used in this example?
A new SQL server is identified as allowing FTP access to all users. Which of the following would a systems administrator most likely do to ensure only the required services are allowed?
A research facility is expecting to see an exponential increase in global network traffic in the near future. The offices are equipped with 2.5Gbps fiber connections from the ISP, but the facility is currently only utilizing 1Gbps connections. Which of the following would need to be configured in order to use the ISP ' s connection speed?
Which of the following steps of the troubleshooting methodology would most likely include checking through each level of the OSI model after the problem has been identified?
A network administrator needs to connect a multimode fiber cable from the MDF to the server room. The administrator connects the cable to Switch 2, but there is no link light. The administrator tests the fiber and finds it does not have any issues. Swapping the connection to Switch 1 in a working port is successful, but the swapped connection does not work on Switch 2. Which of the following should the administrator verify next?
After running a Cat 8 cable using passthrough plugs, an electrician notices that connected cables are experiencing a lot of cross talk. Which of the following troubleshooting steps should the electrician take first?
A network administrator is planning to implement device monitoring to enhance network visibility. The security that the solution provides authentication and encryption. Which of the following meets these requirements?
A network engineer receives a vendor alert regarding a vulnerability in a router CPU. Which of the following should the engineer do to resolve the issue?
Which of the following must be implemented to securely connect a company ' s headquarters with a branch location?
After installing a new 6E wireless router in a small office, a technician notices that some wireless devices are not able to achieve the rated speeds.
Which of the following should the technician check to troubleshoot the issue? (Select two)
Which of the following connection methods allows a network engineer to automate configuration deployment for network devices across the environment?
A company has been added to an unapproved list because of spam. The network administrator confirmed that a workstation was infected by malware. Which of the following processes did the administrator use to identify the root cause?
A secure communication link needs to be configured between data centers via the internet. The data centers are located in different regions. Which of the following is the best protocol for the network administrator to use?
A network administrator needs to set up a multicast network for audio and video broadcasting. Which of the following networks would be the most appropriate for this application?
A network technician sets up a computer on the accounting department floor for a user from the marketing department. The user reports that they cannot access the marketing department’s shared drives but can access the internet. Which of the following is the most likely cause of this issue?
Which of the following devices functions mainly at the data link layer of the OSI model and is used to connect a fiber-optic cable to a network interface?
A data center interconnect using a VXLAN was recently implemented. A network engineer observes slow performance and fragmentation on the interconnect. Which of the following technologies will resolve the issue?
Which of the following is the most likely benefit of installing server equipment in a rack?
A client with a 2.4GHz wireless network has stated that the entire office is experiencing intermittent issues with laptops after the WAP was moved. Which of the following is the most likely reason for these issues?
A network administrator needs to assign IP addresses to a newly installed network. They choose 192.168.1.0/24 as their network address and need to create three subnets with 30 hosts on each subnet. Which of the following is a valid subnet mask that will meet the requirements?
A firewall receives traffic on port 80 and forwards it to an internal server on port 88. Which of the following technologies is being leveraged?
Which of the following can be implemented to add an additional layer of security between a corporate network and network management interfaces?
Several users in an organization report connectivity issues and lag during a video meeting. The network administrator performs a tcpdump and observes increased retransmissions for other non-video applications on the network. Which of the following symptoms describes the users ' reported issues?
Which of the following protocols is used to route traffic on the public internet?
A network technician is designing a LAN for a new facility. The company is expecting more than 300 devices to connect to the network. Which of the following masks will provide the most efficient subnet?
Which of the following, in addition to a password, can be asked of a user for MFA?
Which of the following is the most cost-effective way to safely expand outlet capacity in an IDF?
A network rack has four servers and four switches with dual power supplies. Only one intelligent PDU is installed in the rack. Which of the following is the reason to add a second PDU?
An administrator needs to configure an IoT device with a /21 subnet mask, but the device will only accept dotted decimal notation. Which of the following subnet masks should the administrator use?
After a networking intern plugged in a switch, a significant number of users in a building lost connectivity. Which of the following is the most likely root cause?
Which of the following cloud deployment models is most commonly associated with multitenancy and is generally offered by a service provider?
An organization recently connected a new computer to the LAN. The user is unable to ping the default gateway. The technician examines the configuration and sees a self-assigned IP address. Which of the following is the most likely cause?
A network technician is terminating a cable to a fiber patch panel in the MDF. Which of the following connector types is most likely in use?
A technician is troubleshooting a user ' s laptop that is unable to connect to a corporate server. The technician thinks the issue pertains to routing. Which of the following commands should the technician use to identify the issue?
Which of the following source control features allows an administrator to test a new configuration without changing the primary configuration?
A company is implementing a wireless solution in a high-density environment. Which of the following 802.11 standards is used when a company is concerned about device saturation and converage?
Which of the following most likely determines the size of a rack for installation? (Select two).
A user connects to a corporate VPN via a web browser and is able to use TLS to access the internal financial system to input a time card. Which of the following best describes how the VPN is being used?
Which of the following attacks utilizes a network packet that contains multiple network tags?
A network technician needs to configure IP addressing in a Class C network with eight subnets total:
Three subnets for 60 hosts
Three subnets for 15 hosts
Two subnets for seven hosts
Which of the following solutions should the technician use to accomplish this task?
Which of the following cloud service models most likely requires the greatest up-front expense by the customer when migrating a data center to the cloud?
Which of the following is a type of NAC that uses a set of policies to allow or deny access to the network based on the user ' s identity?
A network engineer is implementing a new connection between core switches. The engineer deploys the following configurations:
Core-SW01
vlan 100
name
interface Ethernet 1/1
channel-group 1 mode active
interface Ethernet 1/2
channel-group 1 mode active
interface port-channel 1
switchport mode trunk
switchport trunk allow vlan 100
Core-SW02
vlan 100
name
interface Ethernet 1/1
switchport mode trunk
switchport trunk allow vlan 100
interface Ethernet 1/2
switchport mode trunk
switchport trunk allow vlan 100
interface port-channel 1
switchport mode trunk
switchport trunk allow vlan 100
Which of the following is the state of the Core-SW01 port-channel interfaces?
A network technician is troubleshooting the connection to the company website. The traceroute command produces the following output:
Traceroute towww.mysite.com(8.8.8.8) over a maximum of 30 hops
10.1.1.1 < 1 ms 2. * < 1 ms < 1 ms
k k
k kTraceroute completeWhich of the following should the technician do to identify the path to the server?
A wireless technician wants to implement a technology that will allow user devices to automatically navigate to the best available frequency standard. Which of the following technologies should the technician use?
An IT department asks a newly hired employee to use a personal laptop until the company can provide one. Which of the following policies is most applicable to this situation?
Which of the following is the next step to take after successfully testing a root cause theory?
A systems administrator needs to connect two laptops to a printer via Wi-Fi. The office does not have access points and cannot purchase any. Which of the following wireless network types best fulfills this requirement?
Which of the following network access methods is used to securely access resources, such as a corporate cloud or network, as if they were directly connected?
A network engineer needs to virtualize network services, including a router at a remote branch location. Which of the following solutions meets the requirements?
Which of the following ports is used to transfer data between mail exchange servers?
A company wants to implement a disaster recovery site or non-critical applicance, which can tolerance a short period of downltime. Which of the followig type of sites should the company impelement to achive this goal?
Early in the morning, an administrator installs a new DHCP server. In the afternoon, some users report they are experiencing network outages. Which of the following is the most likely issue?
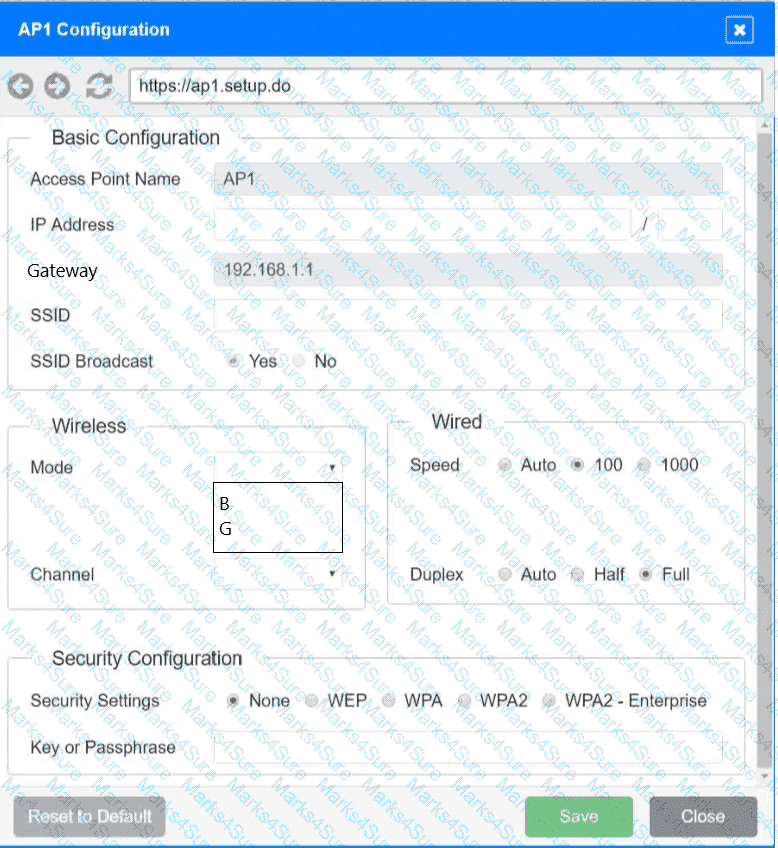
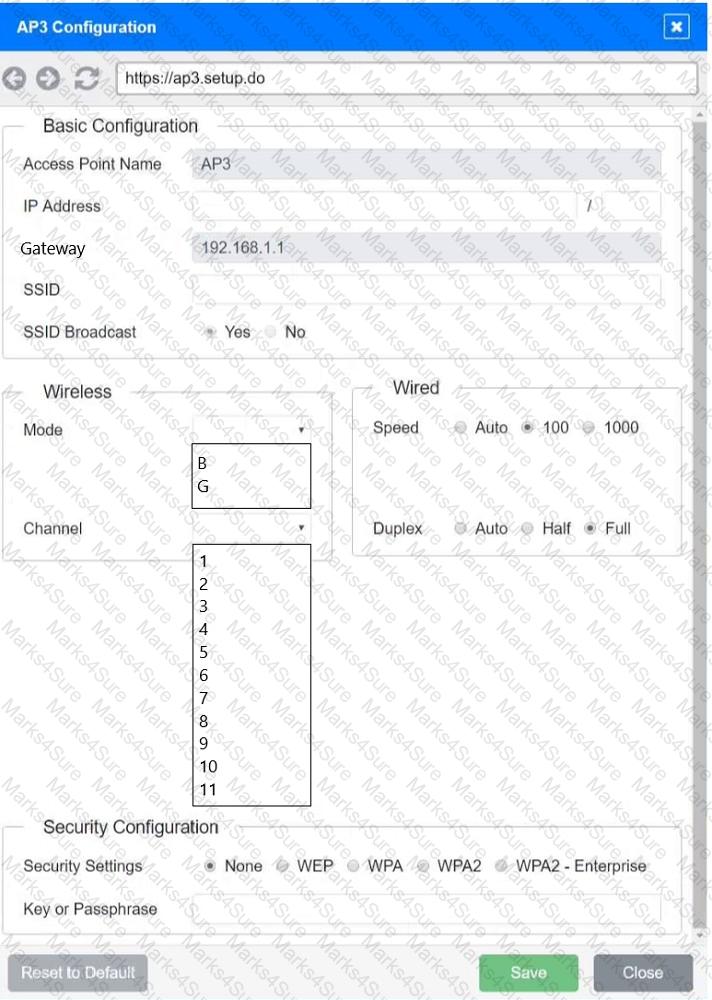
SIMULATION
You have been tasked with setting up a wireless network in an office. The network will consist of 3 Access Points and a single switch. The network must meet the following parameters:
The SSIDs need to be configured as CorpNet with a key of S3cr3t!
The wireless signals should not interfere with each other
The subnet the Access Points and switch are on should only support 30 devices maximum
The Access Points should be configured to only support TKIP clients at a maximum speed
INSTRUCTONS
Click on the wireless devices and review their information and adjust the settings of the access points to meet the given requirements.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Users are reporting latency on the network. The network engineer notes the following:
Confirms the only change was a new network switch
Confirms all users are experiencing latency
Thinks the issue is a network loop caused by the lower bridge ID of the new switch
Which of the following describes the next step in the troubleshooting methodology?
A network engineer queries a hostname using dig, and a valid IP address is returned. However, when the engineer queries that same IP address using dig, no hostname is returned. Which of the following DNS records is missing?
A network administrator determines that some switch ports have more errors present than expected. The administrator traces the cabling associated with these ports. Which of the following would most likely be causing the errors?
A Chief Information Officer wants a DR solution that runs only after a failure of the primary site and can be brought online quickly once recent backups are imported. Which of the following DR site solutions meets these requirements?
A network engineer is now in charge of all SNMP management in the organization. The engineer must use a SNMP version that does not utilize plaintext data. Which of the following is the minimum version of SNMP that supports this requirement?
An administrator is setting up an SNMP server for use in the enterprise network and needs to create device IDs within a MIB. Which of the following describes the function of a MIB?
Which of the following uses the longest prefix match to determine an exit interface?
A customer calls the help desk to report that resources are no longer reachable. The resources were available before network changes were made. The technician verifies the report, investigates, and discovers that a new logical layout is segmenting the network using tagging. Which of the following appliances most likely needs to be reviewed to restore the connections?
Which of the following is a company most likely enacting if an accountant for the company can only see the financial department ' s shared folders?
Which of the following connection methods allows a network engineer to automate the configuration deployment for network devices across the environment?
A company upgrades its network and PCs to gigabit speeds. After the upgrade, users are not getting the expected performance. Technicians discover that the speeds of the endpoint NICs are inconsistent. Which of the following should be checked first to troubleshoot the issue?
A network administrator is reviewing a production web server and observes the following output from the netstat command:
Which of the following actions should the network administrator take to harden the security of the web server?
A network administrator receives complaints of intermittent network connectivity issues. The administrator investigates and finds that the network design contains potential loop scenarios. Which of the following should the administrator do?
Which of the following best describes a group of devices that is used to lure unsuspecting attackers and to study the attackers ' activities?
A network administrator upgrades the wireless access points and wants to implement a configuration that gives users higher speed and less channel overlap based on device compatibility. Which of the following accomplishes this goal?
A customer calls the help desk to report issues connection to the internet. The customer can reach a local database server. A technician goes to the site and examines the configuration:
Which of the following is causing the user ' s issue?
An attack on an internal server is traced to an isolated guest network. Which of the following best describes the attack?
Which of the following steps of the troubleshooting methodology should a technician take to confirm a theory?
A network engineer needs to add a boundary network to isolate and separate the internal network from the public-facing internet. Which of the following security defense solutions would best accomplish this task?
A systems administrator is looking for operating system information, running services, and network ports that are available on a server. Which of the following software tools should the administrator use to accomplish this task?
A network engineer configures an application server so that it automatically adjusts resource allocation as demand changes. This server will host a new application and demand is not predictable. Which of the following concepts does this scenario demonstrate?
Which of the following is most commonly associated with many systems sharing one IP address in the public IP-addressing space?
A network administrator prepares a VLAN for a new office while planning for minimal IP address waste. The new office will have approximately 800 workstations. Which of the following network schemes meets the requirements?
A network administrator is configuring a network for a new site that will have 150 users. Within the next year, the site is expected to grow by ten users. Each user will have two IP addresses (one for a computer and one for a phone). Which of the following classful IPv4 address ranges will be best-suited for the network?
A network administrator is connecting two Layer 2 switches in a network. These switches must transfer data in multiple networks. Which of the following would fulfill this requirement?
Which of the following OSI model layers manages the exchange of HTTP information?
A network administrator is setting up a firewall to protect the organization’s network from external threats. Which of the following should the administrator consider first when configuring the firewall?
Which of the following types of attacks is most likely to occur after an attacker sets up an evil twin?
A network administrator is implementing security zones for each department. Which of the following should the administrator use to accomplish this task?
Which of the following connector types would most likely be used to connect to an external antenna?
Users report latency with a SaaS application. Which of the following should a technician adjust to fix the issue?
A network administrator is configuring a wireless network with an ESSID. Which of the following is a user benefit of ESSID compared to SSID?
A user calls the help desk after business hours to complain that files on a device are inaccessible and the wallpaper was changed. The network administrator thinks that this issue is an isolated incident, but the security analyst thinks the issue might be a ransomware attack. Which of the following troubleshooting steps should be taken first?