An administrator is attempting to deploy an NC2 cluster.
The cluster configuration is as follows:
* Name-Cluster-1
* Nodes of type i4i.metal
* Replication Factor 2
* Existing VPC resources
*VPC-10.0.0.0/16
*Subnets:
*Bare metal hosts: 10.0.1.0/24
*User VMs:10.0.2.0/24
*Public: 10.0.3.0/24
During the deployment process, the administrator notices the following alert:

What should the administrator do to ensure the cluster deployment does not fail?
An administrator needs to allow wide open access to one particular NC2 AWS cluster from an on-premises subnet of 10.19.160.0/24.
What is the proper Custom Security Group formatting to satisfy this task?
A)
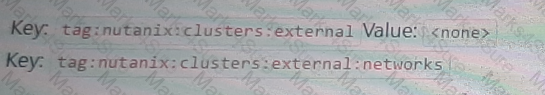
B)
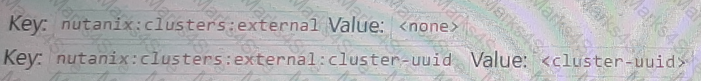
C)
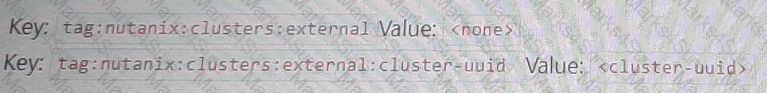
D)
An administrator is creating and destroying multiple clusters daily for a test/dev environment. The administrator wants ensure that every NC2 on AWS cluster deployed will allow full access from the on-premises CVM subnet.
What is most-efficient way to achive this?
What is an available log module when configuring a syslog server in the Prism Central Admin Center?
An administrator needs the permissions to create and manage multiple organizations and clusters in NC2, as well as manage user access for the entire company.
What role should be assigned to meet the minimum requirements of this task?
preparing the landing zone networking resources for a Nutanix cluster on AWS.The administrator has created a VPC with two private subnets:one for cluster management and one for user VMs.
What additional subnet must the administrator create?
An administrator is deploying an NC2 cluster into an existing AWS VPC.
The cluster deployment fails, with the following error message:

Why has the deployment failed?
An administrator has deployed an NC2 cluster on AWS to an existing environment for VDI.
Afterwards, the corporate security teamsdirectthe administrator to reuse an existing AWS subnet, 10.79.4.0/24 that has two EC2 instances: EC2-1 (10.79.4.200) and EC2-2 (10.79.4.201). The security team indicates that this directive is to avoid overlap with the AHV IPAM.
Which two configuration actions should the administrator take to ensure there are no configuration issues? (Choose two.)
Administrator has recently deployed an NC2 cluster on AWS in the North Virginia region in availability zone us-east-id. The consuming IPS from a 10.78.2.0/24 range.
The AWS VPC has two available CIDR ranges:
10.78.0.0/16
10.19.101.0/24
The following subnet have been configured in the NC2 AWS VPC:

Which two subnet will show up in the Network configuration of the Prism Element Settings page? (Choose two.)
Which two statements are the most accurate regarding Cluster Protect? (Choose two.)
When selecting the NC2 subscription plan from the Nutanix Billing portal, which options are available.
An administrator has been tasked with deploying an NC2 cluster on AWS with the requirement to protect workloads. Which two options are valid to protect the workloads on this cluster? (Choose two.)
An administrator has been tasked with deploying a new production NC2 cluster on AWS and is studying the deployment..
AWS supports EC2 bare-metal instances in regions with at least how many partitions?
A company needs to create virtual interfaces directly to public AWS S3 services. The company also wants to bypass any internet service providers in the network path.
Which method will best satisfy this requirement?
When configuring an alert email in Prism Central deployed within anNC2 environment, what is required in order for the emails to be sent properly?
An administrator has been tasked with performing a test migrating from an NC2 environment to a Nutanix on-premisesenvironment.
Where should the administrator perform this task?
An administrator has recently deployed an NC2 on AWS cluster in the North Virginia region in availability zone us-east-1z. The clusters UUID is 0005F487-4962-91EA-4C98-C4284D123835.
The cluster is consuming IPs from a 10.78.2.0/24 range.
The AWS VPC has these available CIDR ranges:
• 70.73.0.0/16
• 10.79.107.0/24
• 10.0.0.0/22
The following subnets have been configured in the NC2 AWS VPC:

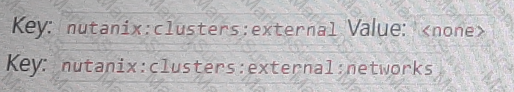
The following tags have been applied to a Custom Network Security Group:
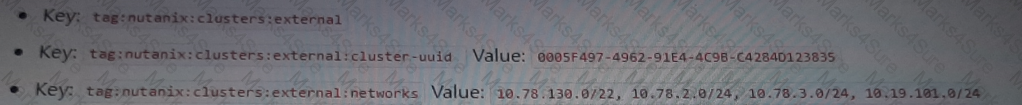
The Custom Network Security Group is allowing all inbound traffic from the 10.0.0.0/22 network. Which two subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment"? (Choose two.)
An organization plans to use the Cluster Protect feature to protect the cluster data.
Which license will satisfy this requirement?