Refer to the exhibit.
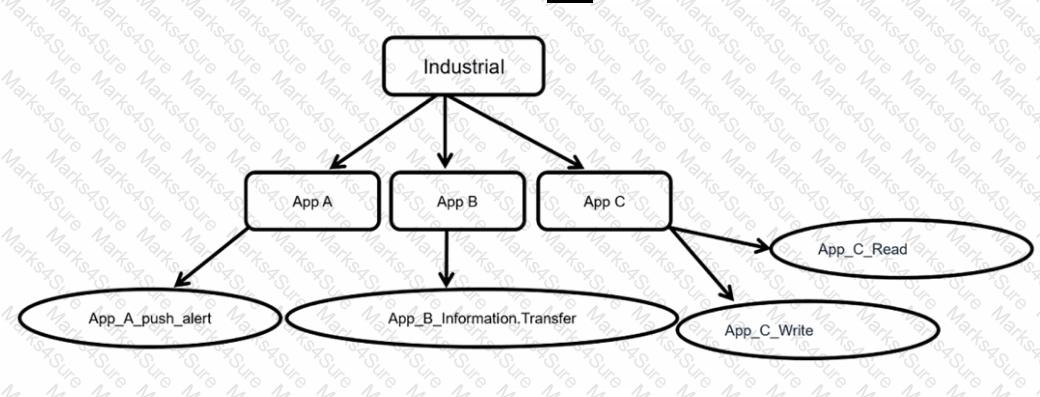
Which statement is true about application control inspection?
Refer to the exhibit and analyze the output.
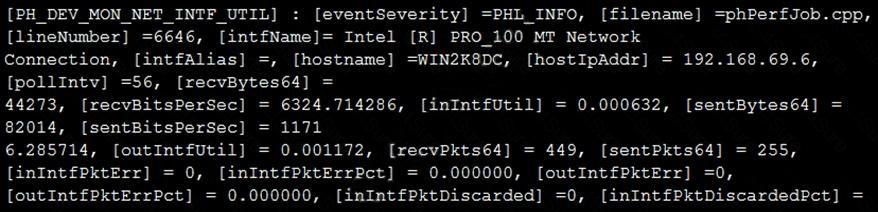
Which statement about the output is true?
Which three common breach points can you find in a typical OT environment? (Choose three.)
Refer to the exhibit, which shows a non-protected OT environment.
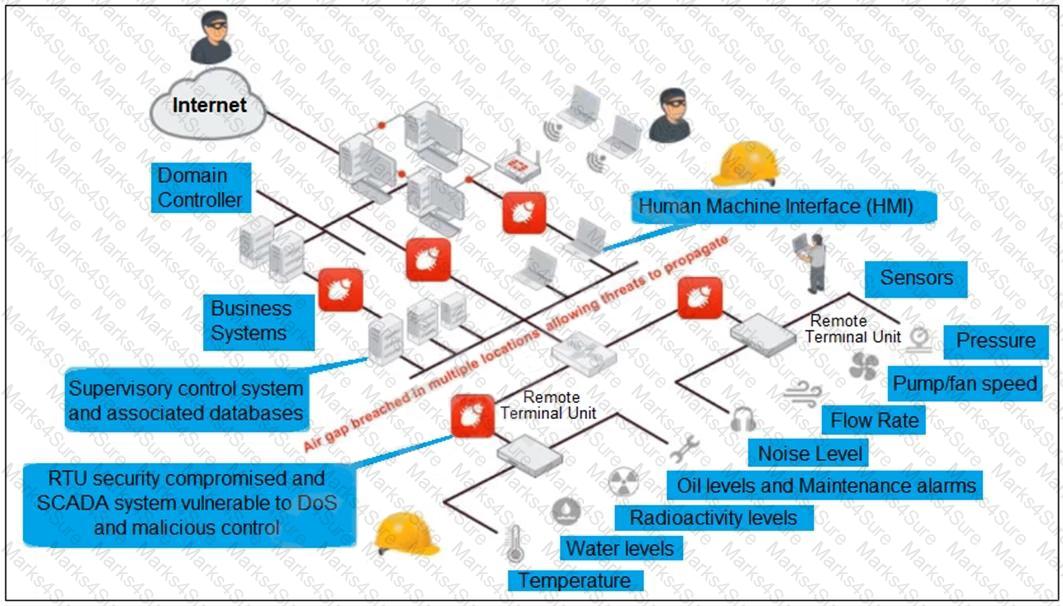
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
The OT network analyst runs different level of reports to quickly explore threats that exploit the network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting method helps to identify these type of exploits of image firmware files?
The OT network analyst run different level of reports to quickly explore failures that could put the network at risk. Such reports can be about device performance. Which FortiSIEM reporting method helps to identify device failures?
in an operation technology (OT) network FortiAnalyzer is used to receive and process logs from responsible FortiGate devices
Which statement about why FortiAnalyzer is receiving and processing multiple tog messages from a given programmable logic controller (PLC) or remote terminal unit (RTU) is true'?
Refer to the exhibit.
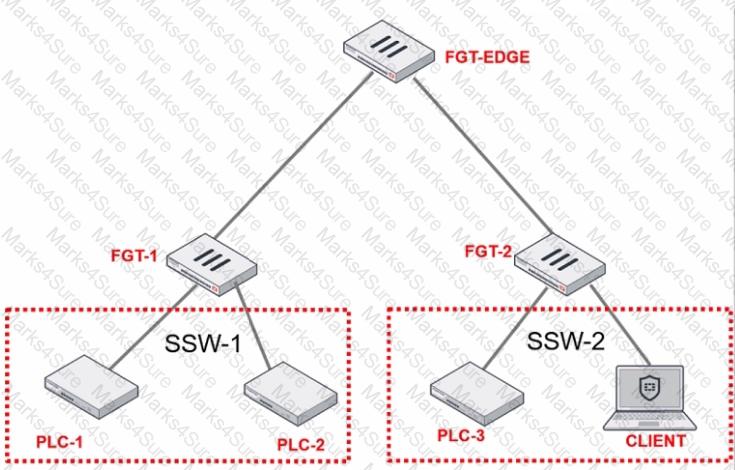
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT cannot send traffic to each other.
Which two statements about the traffic between PCL-1 and PLC-2 are true? (Choose two.)
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
Operational technology (OT) network analysts run different levels of reports to identify failures that could put the network at risk Some of these reports may be related to device performance
Which FortiSIEM reporting method helps identify device failures?
An OT administrator is defining an incident notification policy using FortiSIEM and would like to configure the system with a notification policy. If an incident occurs, the administrator would like to be able to intervene and block an IP address or disable a user in Active Directory from FortiSIEM.
Which step must the administrator take to achieve this task?
Refer to the exhibit.
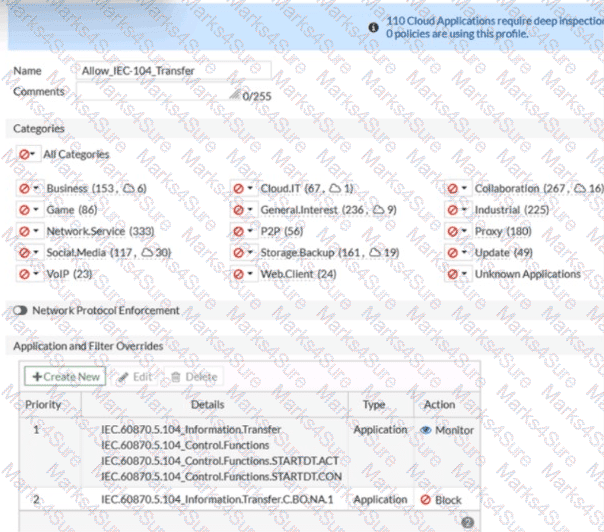
An OT network security audit concluded that the application sensor requires changes to ensure the correct security action is committed against the overrides filters.
Which change must the OT network administrator make?
To increase security protection in an OT network, how does application control on ForliGate detect industrial traffic?
When you create a user or host profile, which three criteria can you use? (Choose three.)
An OT architect has deployed a Layer 2 switch in the OT network at Level 1 the Purdue model-process control. The purpose of the Layer 2 switch is to segment traffic between PLC1 and PLC2 with two VLANs. All the traffic between PLC1 and PLC2 must first flow through the Layer 2 switch and then through the FortiGate device in the Level 2 supervisory control network.
What statement about the traffic between PLC1 and PLC2 is true?