Refer to the exhibit.
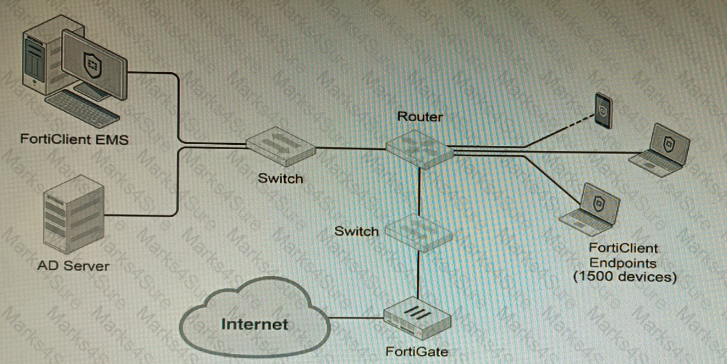
A customer wants FortiClient EMS configured to deploy to 1500 endpoints. The deployment will be integrated with FortiOS and there is an Active Directory server.
Given the configuration shown in the exhibit, which two statements about the installation are correct? (Choose two.)
Refer to the exhibits.
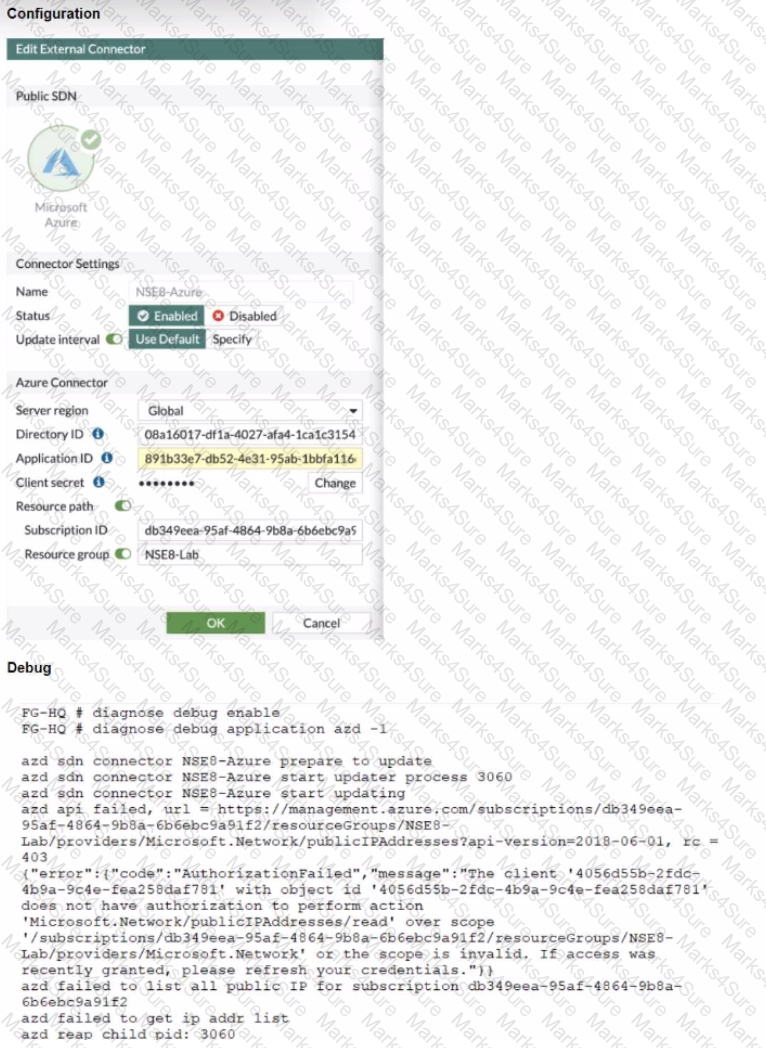
The exhibits show the configuration and debug output from a FortiGate Public SDN Connector.
What is a possible reason for this dynamic address object to be empty?
A Hub FortiGate is connecting multiple branch FortiGate devices separating the traffic centrally in unique VRFs. Routing information is exchanged using BGP between the Hub and the Branch FortiGate devices.
You want to efficiently enable route leaking of specific routes between the VRFs.
Which two steps are required to achieve this requirement? (Choose two.)
Refer to The exhibit, which shows a topology diagram.
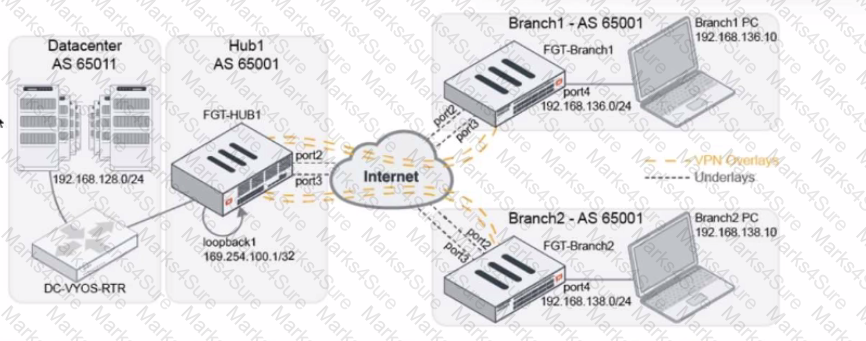
A customer wants to use SD-WAN for traffic generated from the data center towards Branches. SD-WAN on HUB should follow the underlay condition on each Branch and the solution should be scalable for hundreds of Branches.
Which SD WAN-Rules strategy should be used?
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the OCSP server.
Part of the FortiGate configuration is shown below:
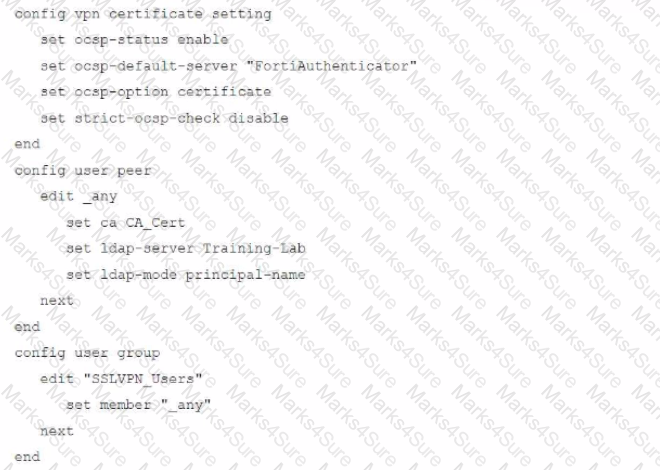
Based on this configuration, which authentication scenario will FortiGate deny?
A remote IT Team is in the process of deploying a FortiGate in their lab. The closed environment has been configured to support zero-touch provisioning from the FortiManager, on the same network, via DHCP options. After waiting 15 minutes, they are reporting that the FortiGate received an IP address, but the zero-touch process failed.
The exhibit below shows what the IT Team provided while troubleshooting this issue:

Which statement explains why the FortiGate did not install its configuration from the FortiManager?
You are responsible for recommending an adapter type for NICs on a FortiGate VM that will run on an ESXi Hypervisor. Your recommendation must consider performance as the main concern, cost is not a factor. Which adapter type for the NICs will you recommend?
Refer to the exhibits, which show a network topology and VPN configuration.
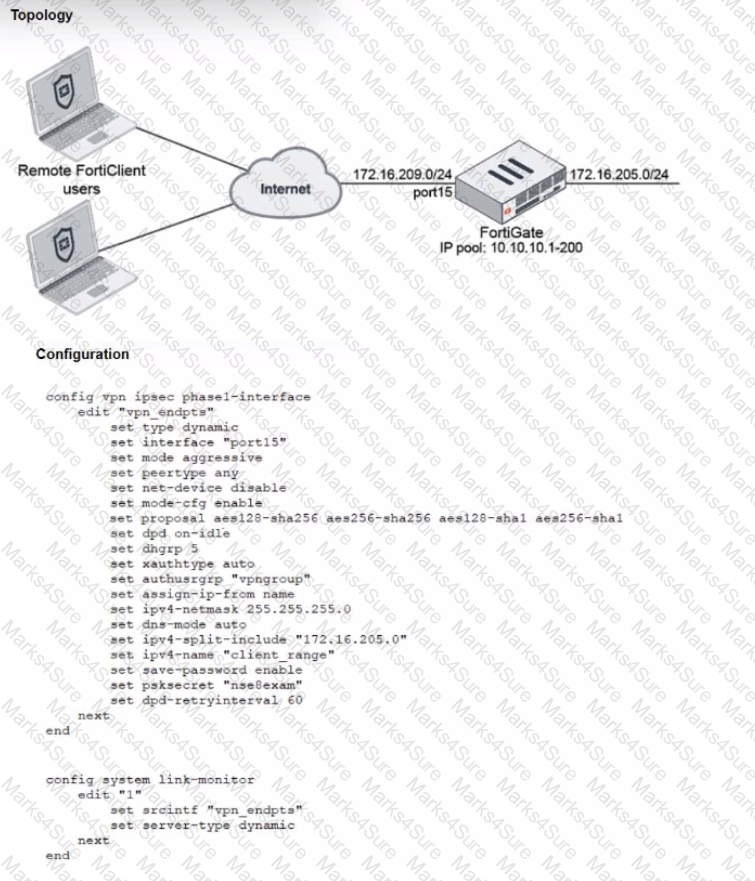
A network administrator has been tasked with modifying the existing dial-up IPsec VPN infrastructure to detect the path quality to the remote endpoints.
After applying the configuration shown in the configuration exhibit, the VPN clients can still connect and access the protected 172.16.205.0/24 network, but no SLA information shows up for the client tunnels when issuing the diagnose sys link-monitor tunnel all command on the FortiGate CLI.
What is wrong with the configuration?
Refer to the exhibits.
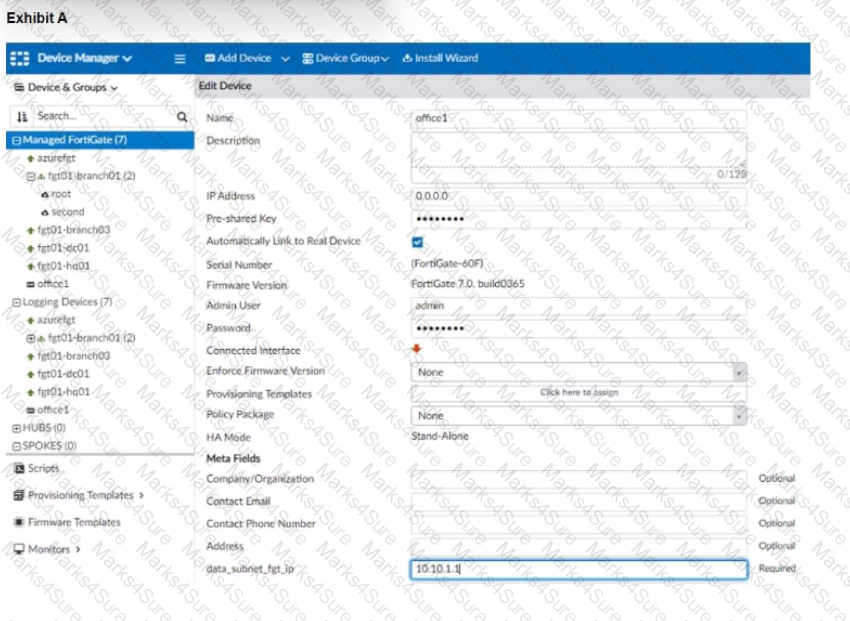
The exhibit shows a FortiGate model device that will be used for zero touch provisioning and a CLI Template.
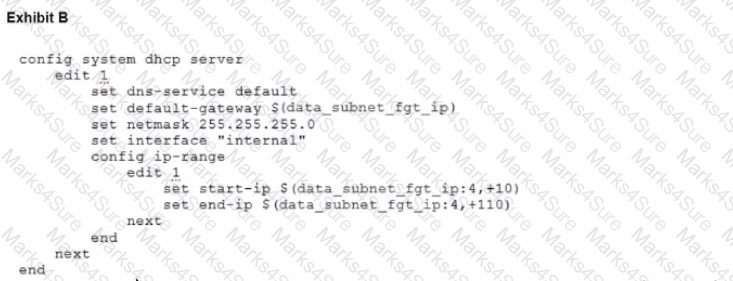
To facilitate a more efficient roll out of FortiGate devices, you are tasked with using meta fields with the CLI Template to configure the DHCP server on the "office1" FortiGate.
Given this scenario, what would be the output of the config ip-range section on the CLI Template?
A FortiGate must be configured to accept VoIP traffic which will include session initiation protocol (SIP) traffic. Which statement about the VoIP configuration options is correct?
Refer to the exhibits.
Exhibit A
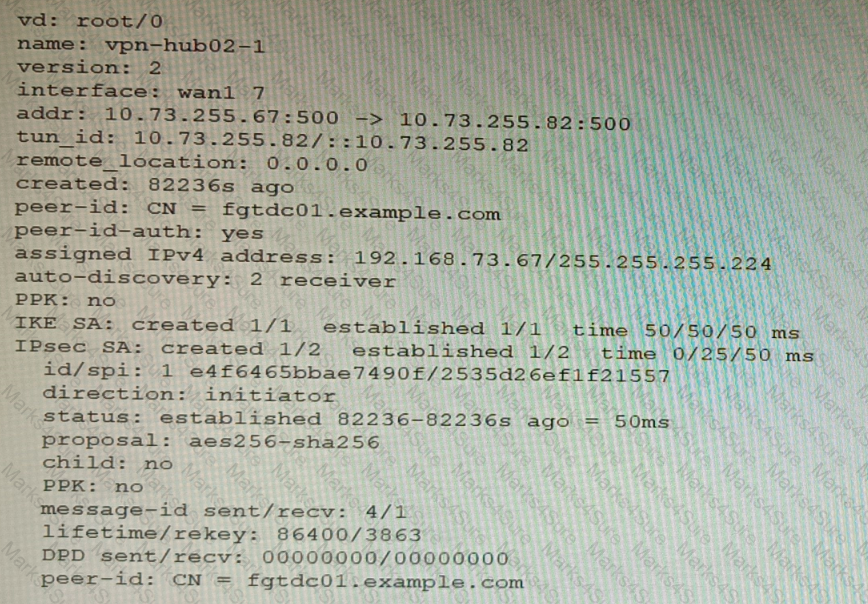
Exhibit B
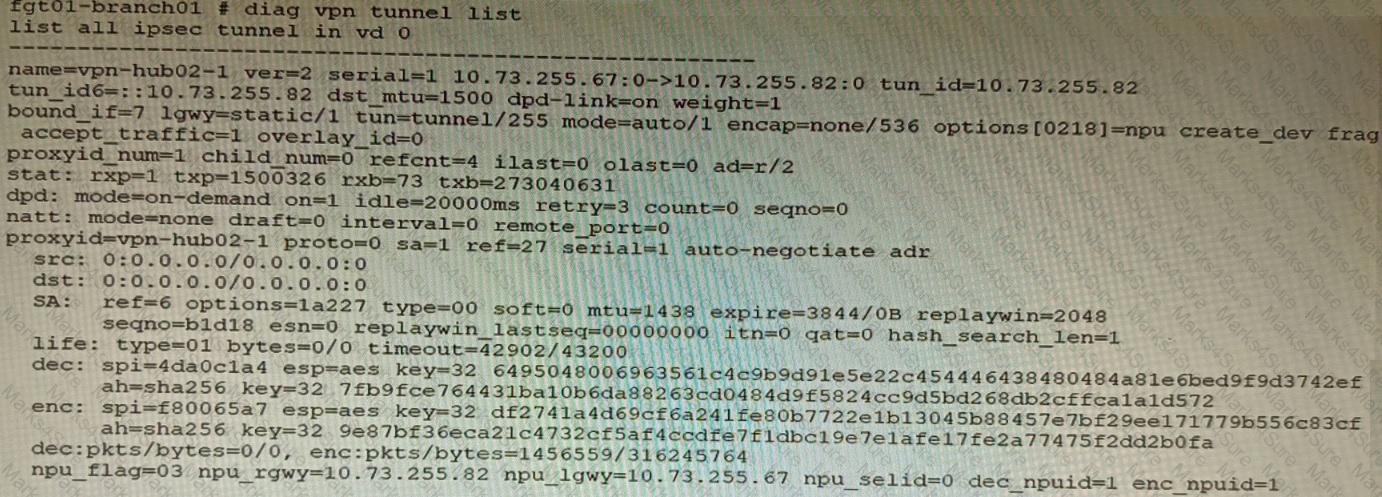
Exhibit C
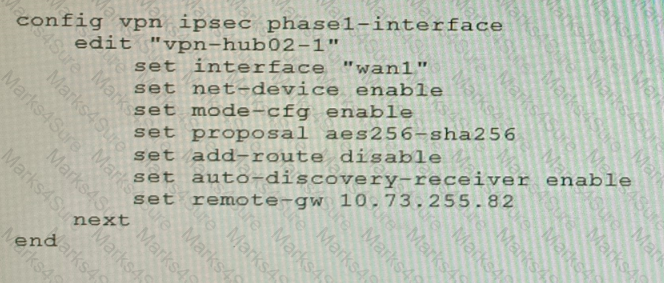
A customer is trying to set up a VPN with a FortiGate, but they do not have a backup of the configuration. Output during a troubleshooting session is shown in the exhibits A and B and a baseline VPN configuration is shown in Exhibit C Referring to the exhibits, which configuration will restore VPN connectivity?
A)
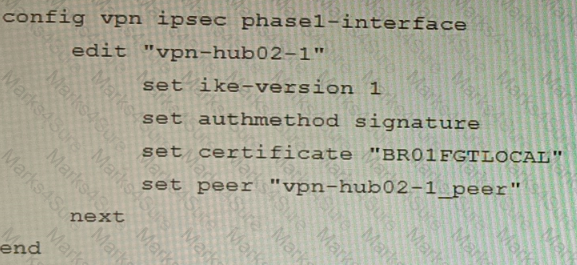
B)
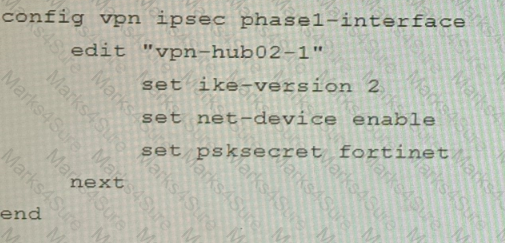
C)
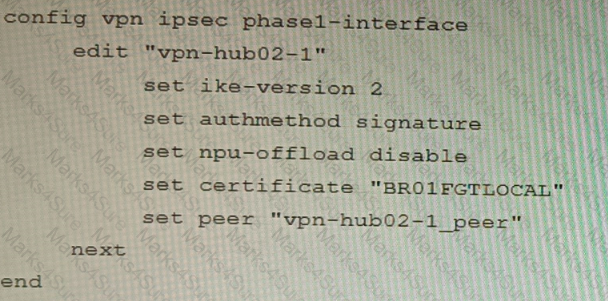
D)
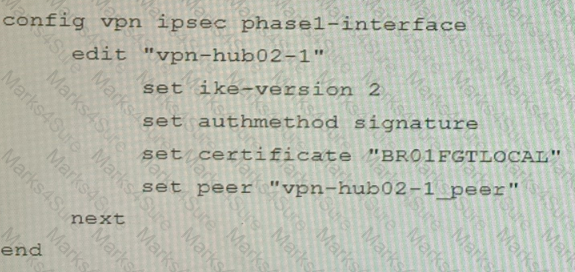
Refer to the exhibits.
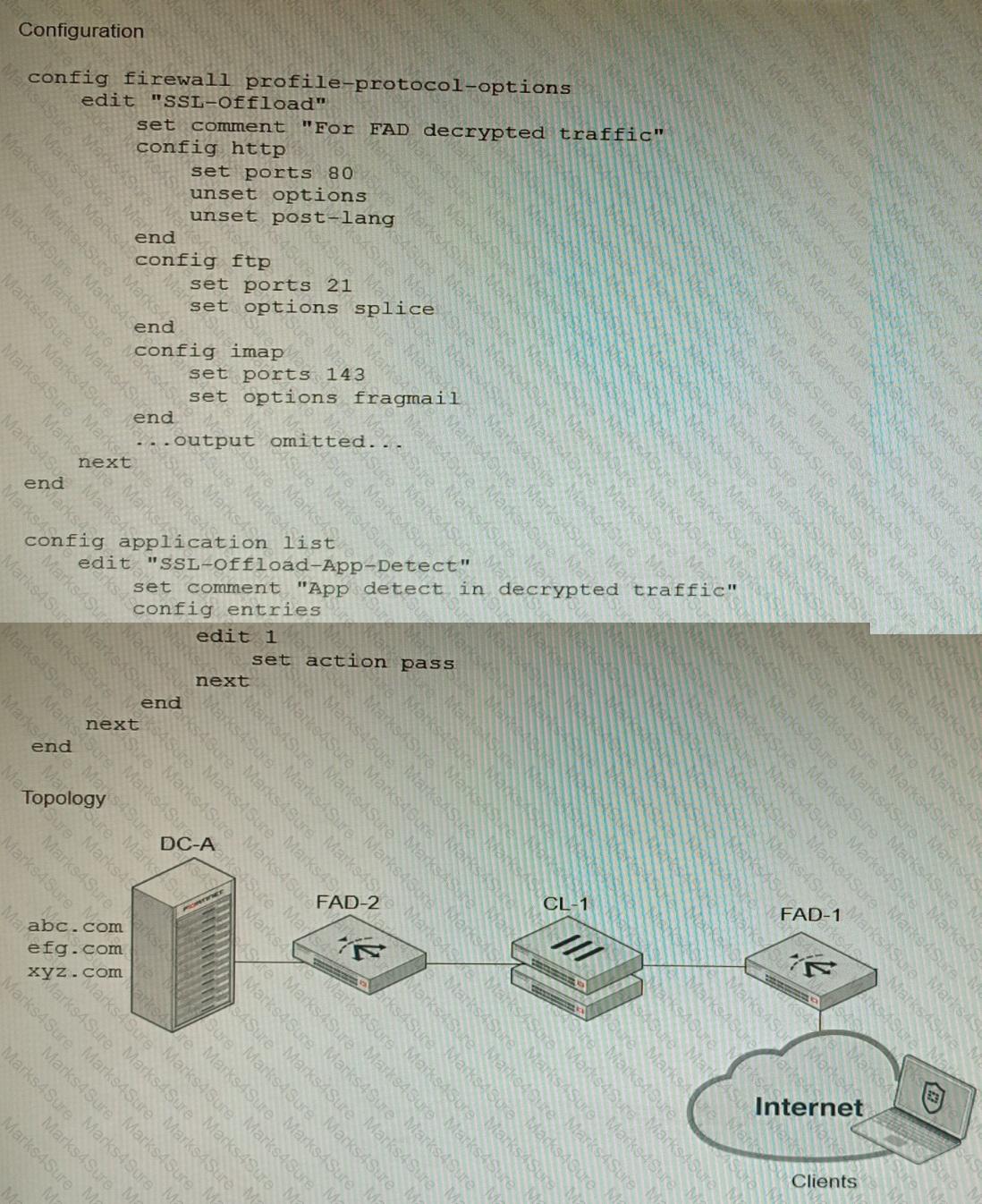
A FortiGate cluster (CL-1) protects a data center hosting multiple web applications. A pair of FortiADC devices are already configured for SSL decryption (FAD-1), and re-encryption (FAD-2). CL-1 must accept unencrypted traffic from FAD-1, perform application detection on the plain-text traffic, and forward the inspected traffic to FAD-2.
The SSL-Offload-App-Detect application list and SSL-Offload protocol options profile are applied to the firewall policy handling the web application traffic on CL-1.
Given this scenario, which two configuration tasks must the administrator perform on CL-1? (Choose two.)
A)
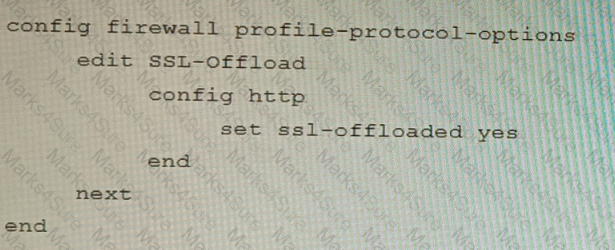
B)

C)
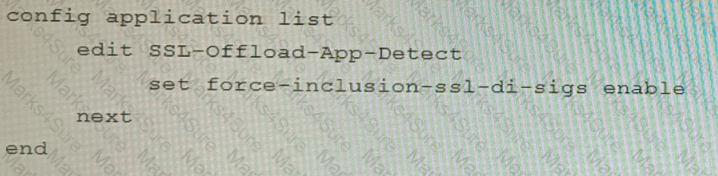
D)
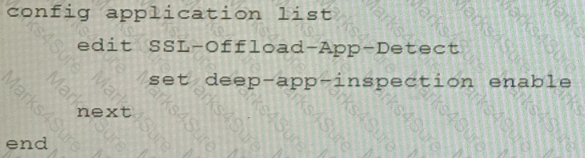
Which two types of interface have built-in active bypass in FortiDDoS devices? (Choose two.)
Refer to the exhibits.
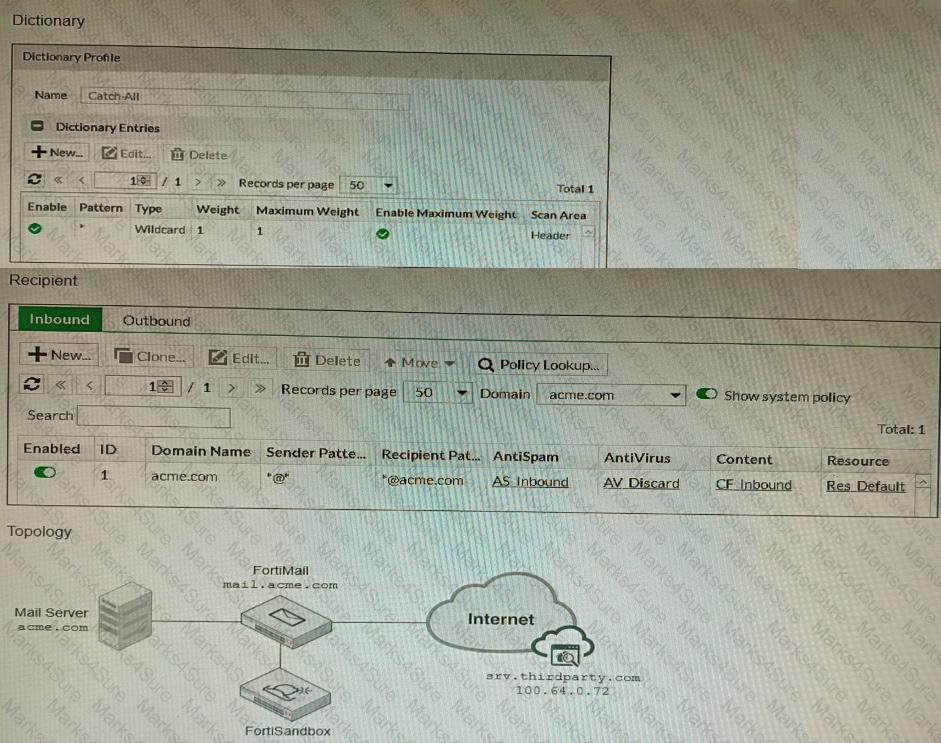
The exhibits show a FortiMail network topology, Inbound configuration settings, and a Dictionary Profile.
You are required to integrate a third-party's host service (srv.thirdparty.com) into the e-mail processing path.
All inbound e-mails must be processed by FortiMail antispam and antivirus with FortiSandbox integration. If the email is clean, FortiMail must forward it to the third-party service, which will send the email back to FortiMail for final delivery, FortiMail must not scan the e-mail again.
Which three configuration tasks must be performed to meet these requirements? (Choose three.)
Refer to the exhibit.
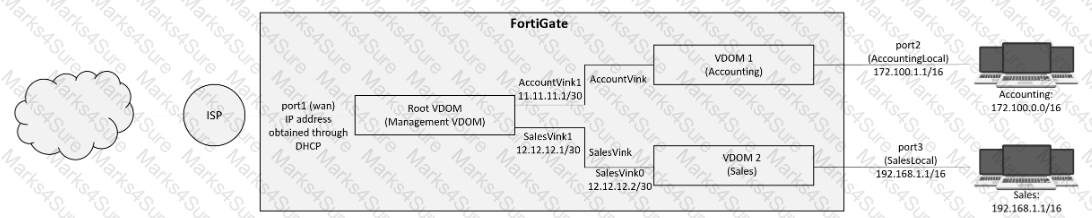
A customer has deployed a FortiGate 300E with virtual domains (VDOMs) enabled in the multi-VDOM mode. There are three VDOMs: Root is for management and internet access, while VDOM 1 and VDOM 2 are used for segregating internal traffic. AccountVInk and SalesVInk are standard VDOM links in Ethernet mode.
Given the exhibit, which two statements below about VDOM behavior are correct? (Choose two.)
You deployed a fully loaded FG-7121F in the data center and enabled sslvpn-load-balance. Based on the behavior of this feature which statement is correct?
You are running a diagnose command continuously as traffic flows through a platform with NP6 and you obtain the following output:
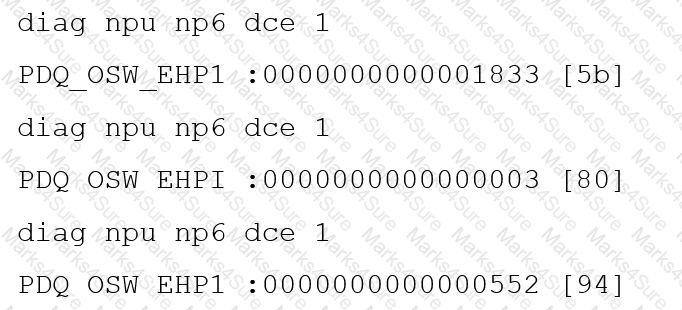
Given the information shown in the output, which two statements are true? (Choose two.)
Refer to the exhibit.
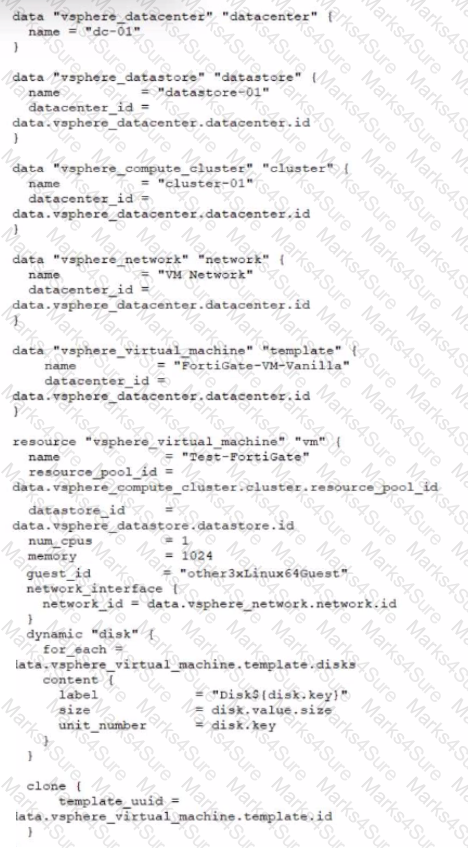
A customer wants to automate the creation and configuration of FortiGate VM instances in a VMware vCenter environment using Terraform. They have the creation part working with the code shown in the exhibit.
Which code snippet will allow Terraform to automatically connect to a newly deployed FortiGate if its IP was dynamically assigned by VMware NSX-T?
You must configure an environment with dual-homed servers connected to a pair of FortiSwitch units using an MCLAG.
Multicast traffic is expected in this environment, and you should ensure unnecessary traffic is pruned from links that do not have a multicast listener.
In which two ways must you configure the igmps-f lood-traffic and igmps-flood-report settings? (Choose two.)
Refer to the exhibit that shows VPN debugging output.
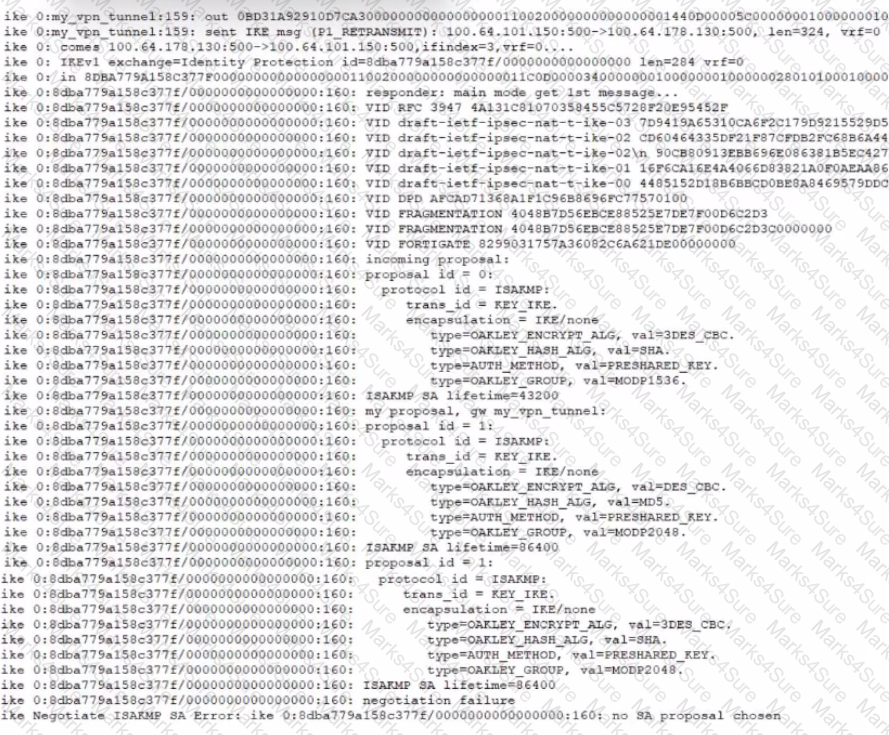
The VPN tunnel between headquarters and the branch office is not being established.
What is causing the problem?
Refer to the exhibit, which shows a VPN topology.
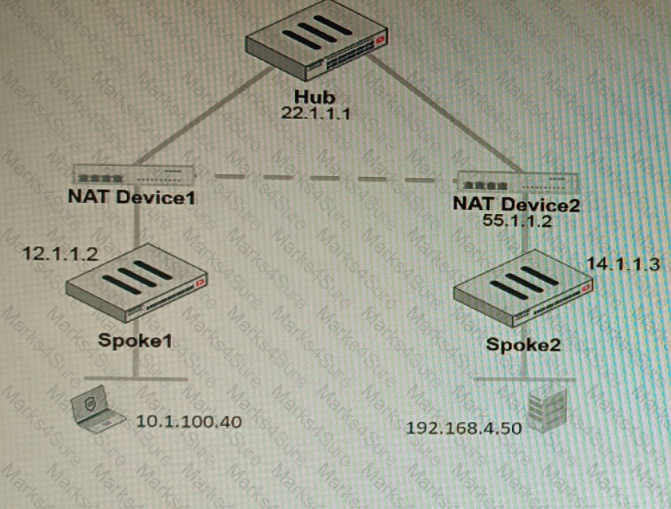
The device IP 10.1.100.40 downloads a file from the FTP server IP 192.168.4.50
Referring to the exhibit, what will be the traffic flow behavior if ADVPN is configured in this environment?
Refer to the exhibit.
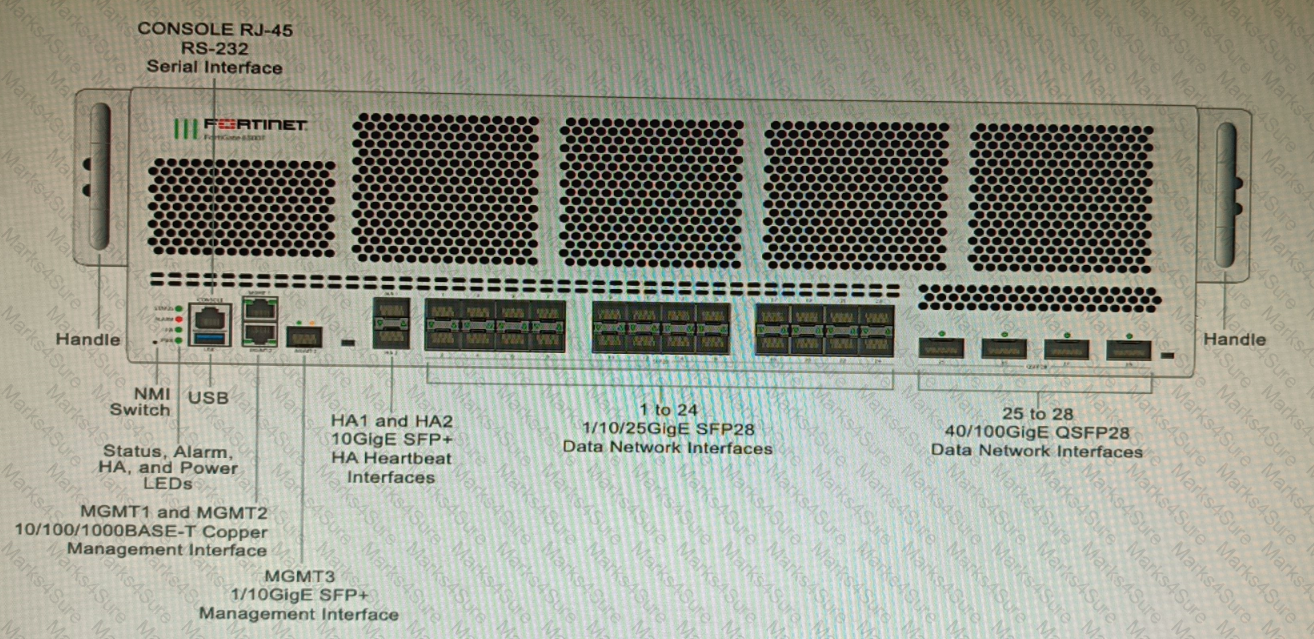
You are deploying a FortiGate 6000F. The device should be directly connected to a switch. In the future, a new hardware module providing higher speed will be installed in the switch, and the connection to the FortiGate must be moved to this higher-speed port.
You must ensure that the initial FortiGate interface connected to the switch does not affect any other port when the new module is installed and the new port speed is defined.
How should the initial connection be made?
Refer to the exhibit.
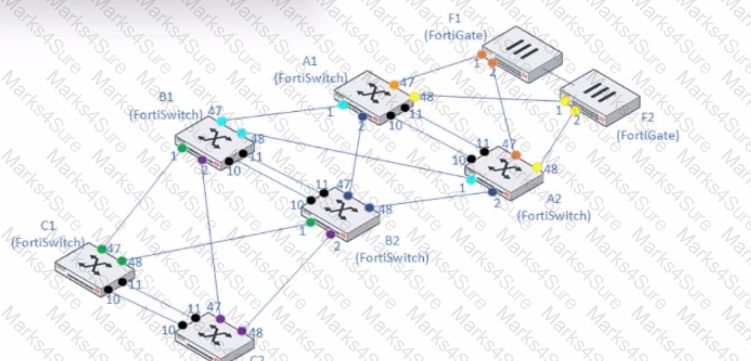
A customer needs to create a multi-tier MCLAG set up with the topology as shown in the exhibit.
A1/A2
B1/B2
C1/C2
Which command snippet should be applied to it, to allow active/active links in this topology?
A customer has FortiAP devices in three branch offices managed from a FortiGate in the HQ. Each FortiAP is connected to a dedicated management VLAN.
The customer wants the users connected to the FortiAP SSIDs to use the branch local internet connection, but each branch uses a different VLAN ID for the bridge. HQ users travel to different branches and connect to the same SSID.
Which configuration option will solve this requirement?
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
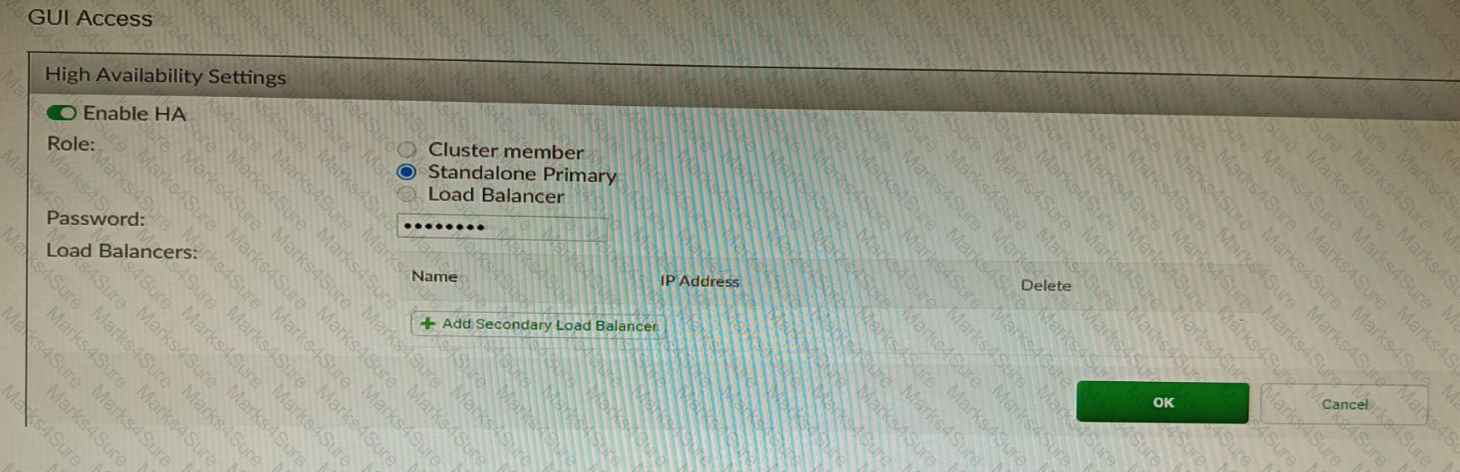
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
Refer to the exhibits.

During the implementation of a Fortinet Security Fabric configuration, CLI commands were issued in the order shown in the exhibit. On the next day, the local admin for FGTC issues the following command:
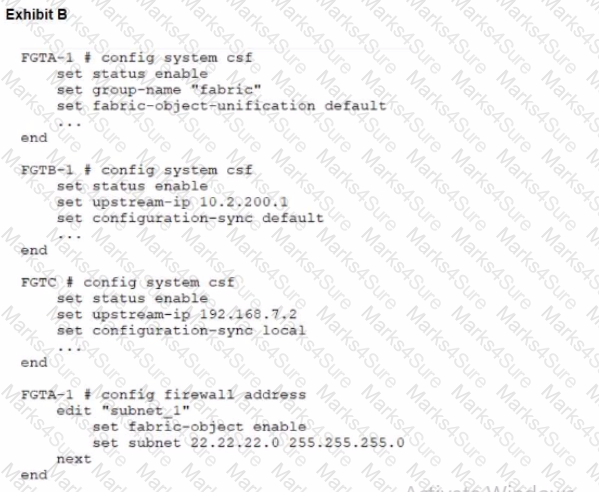
FGTC # config system csf
set configuration-sync default
end
In this scenario, which outcome is true regarding the "subnet_1" firewall address object on FGTC?
You are creating the CLI script to be used on a new SD-WAN deployment You will have branches with a different number of internet connections and want to be sure there is no need to change the Performance SLA configuration in case more connections are added to the branch.
The current configuration is:
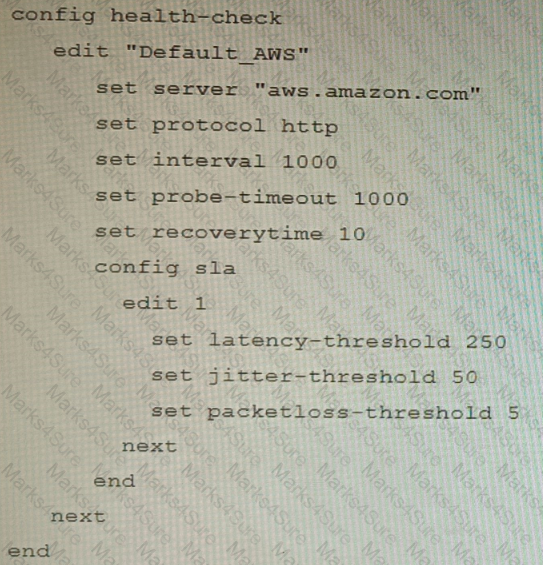
Which configuration do you use for the Performance SLA members?
Refer to the exhibit.
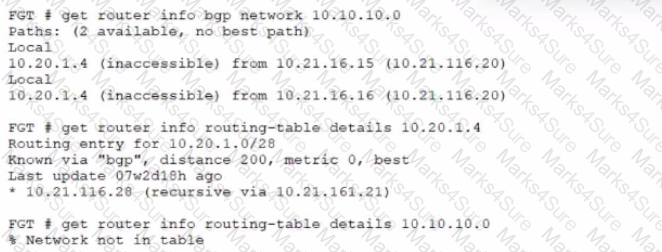
A customer reports that they are not able to reach subnet 10.10.10.0/24 from their FortiGate device.
Based on the exhibit, what should you do to correct the situation?