Your learn is asked to Investigate which of the Netskope DLP policies are creating the most incidents. In this scenario, which two statements are true? (Choose two.)
Recently your company implemented Zoom for collaboration purposes and you are attempting to inspect the traffic with Netskope. Your initial attempt reveals that you are not seeing traffic from the Zoom client that is used by all users. You must ensure that this traffic is visible to Netskope.
In this scenario, which two steps must be completed to satisfy this requirement? (Choose two.)
Review the exhibit.
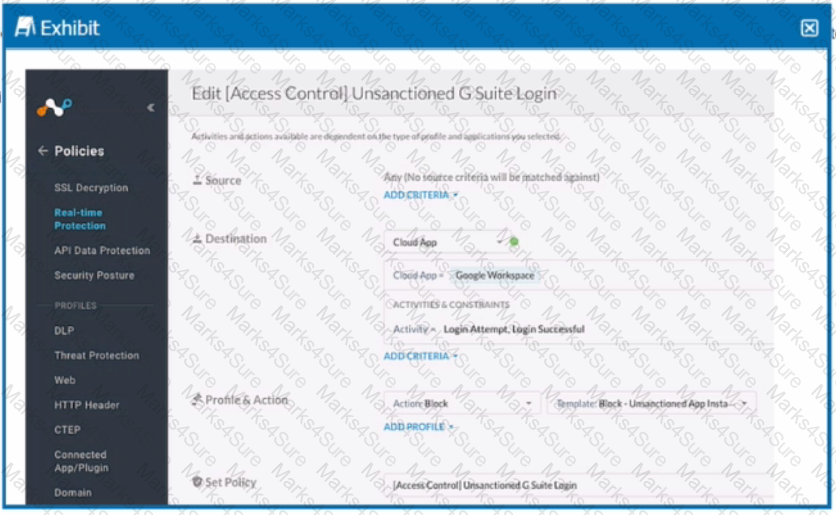
Your company uses Google as the corporate collaboration suite; however, corporate policy restricts the use of personal Google services. The exhibit provides a partially completed policy to ensure that users cannot log into their personal account.
What should be added to achieve the desired outcome in this scenario?
You use Netskope to provide a default Malware Scan profile for use with your malware policies. Also, you want to create a custom malware detection profile.
In this scenario, what are two additional requirements to complete this task? (Choose two.)
Your organization has a homegrown cloud application. You are required to monitor the activities that users perform on this cloud application such as logins, views, and downloaded files. Unfortunately, it seems Netskope is unable to detect these activities by default.
How would you accomplish this goal?
Your company has many users that are remote and travel often. You want to provide the greatest visibility into their activities, even while traveling. Using Netskope. which deployment method would be used in this scenario?
Review the exhibit.
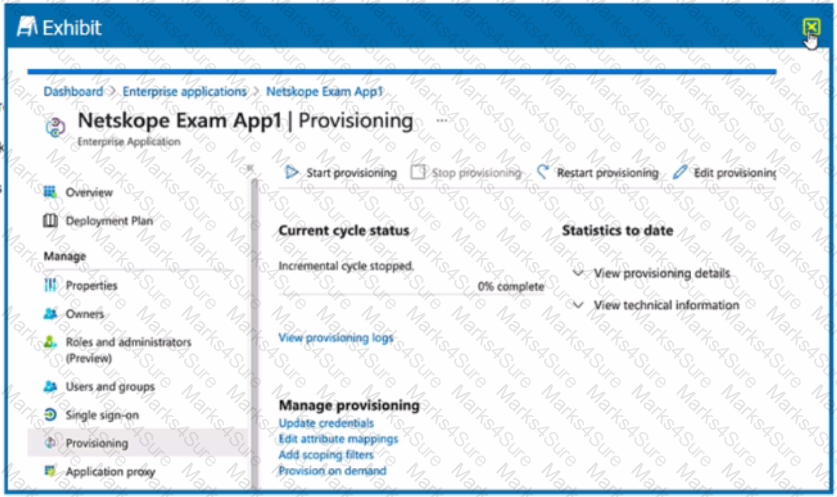
What is the purpose of the configuration page shown Ii the exhibit?
While most Web and SaaS traffic is decrypted for inspection, you are asked to prevent a certain host on the network from SSL decryption for privacy purposes.
You want to provide malware protection for all cloud storage applications.
In this scenario, which action would accomplish this task?
Your IT organization is migrating its user directory services from Microsoft Active Directory to a cloud-based Identity Provider (IdP) solution, Azure AD. You are asked to adapt the Netskope user provisioning process to work with this new cloud-based IdP.
You discover the ongoing use of the native Dropbox client in your organization. Although Dropbox is not a corporate-approved application, you do not want to prevent the use of Dropbox. You do, however, want to ensure visibility into its usage.
You want to prevent a document stored in Google Drive from being shared externally with a public link.
You have created a specific Skope IT application events query and want to have the query automatically run and display the results every time you log into your tenant.
Which two statements are correct in this scenario? (Choose two.)
Netskope is being used as a secure Web gateway. Your organization's URL list changes frequently. In this scenario, what makes It possible for a mass update of the URL list in the Netskope platform?
Your organization has three main locations with 30.000 hosts in each location. You are planning to deploy Netskope using iPsec tunnels for security.
What are two considerations to make a successful connection in this scenario? (Choose two.)
You are using the Netskope DLP solution. You notice flies containing test data for credit cards are not triggering DLP events when uploaded to Dropbox. There are corresponding page events. Which two scenarios would cause this behavior? (Choose two.)
You are comparing the behavior of Netskope's Real-time Protection policies to API Data Protection policies. In this Instance, which statement is correct?
You are creating an API token to allow a DevSecOps engineer to create and update a URL list using REST API v2. In this scenario, which privilege(s) do you need to create in the API token?
Review the exhibit.
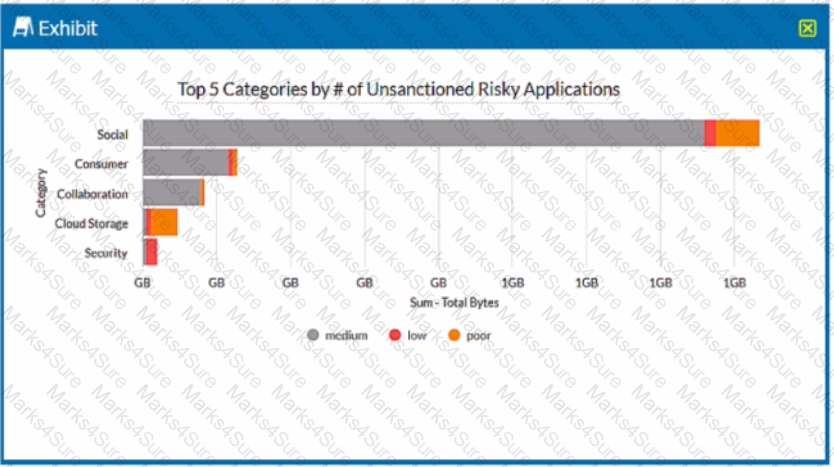
A security analyst needs to create a report to view the top five categories of unsanctioned applications accessed in the last 90 days. Referring to the exhibit, what are two data collections in Advanced Analytics that would be used to create this report? (Choose two.)
You are configuring GRE tunnels from a Palo Alto Networks firewall to a Netskope tenant with the Netskope for Web license enabled. Your tunnel is up as seen from the Netskope dashboard. You are unable to ping hosts behind the Netskope gateway.
Which two statements are true about this scenario? (Choose two.)
Review the exhibit.
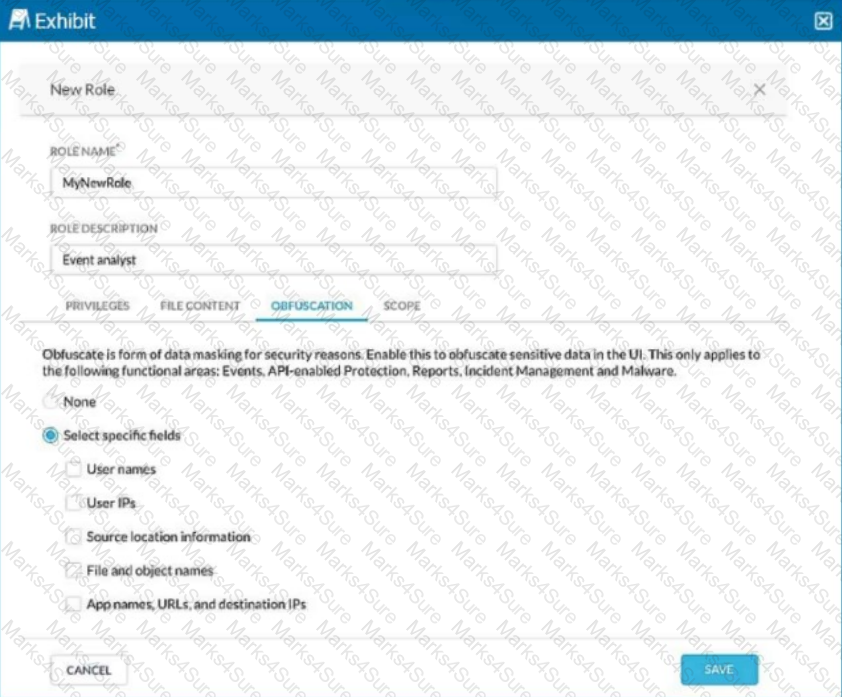
You are asked to create a new role that allows analysts to view Events and Reports while providing user privacy. You need to avoid directly exposing identities and user location information.
Which three fields must you obfuscate in this scenario? (Choose three.)
Your customer has some managed Windows-based endpoints where they cannot add any clients or agents. For their users to have secure access to their SaaS application, you suggest that the customer use Netskope's Explicit Proxy.
Which two configurations are supported for this use case? (Choose two.)
With Netskope DLP, which feature would be used to detect keywords such as "Confidential" or "Access key"?