An organization experiences a compromise in a cloud-hosted solution that contains customer information. Which of the following strategies will help determine the sensitivity level of the breach?
Which of the following explains how regular patching helps mitigate risks when securing an enterprise environment?
Which of the following is a type of vulnerability that involves inserting scripts into web-based applications in order to take control of the client's web browser?
An enterprise has been experiencing attacks focused on exploiting vulnerabilities in older browser versions with well-known exploits. Which of the following security solutions should be configured to best provide the ability to monitor and block these known signature-based attacks?
Which of the following is the most effective way to protect an application server running software that is no longer supported from network threats?
A company with a high-availability website is looking to harden its controls at any cost. The company wants to ensure that the site is secure by finding any possible issues. Which of the following would most likely achieve this goal?
A network manager wants to protect the company's VPN by implementing multifactor authentication that uses:
. Something you know
. Something you have
. Something you are
Which of the following would accomplish the manager's goal?
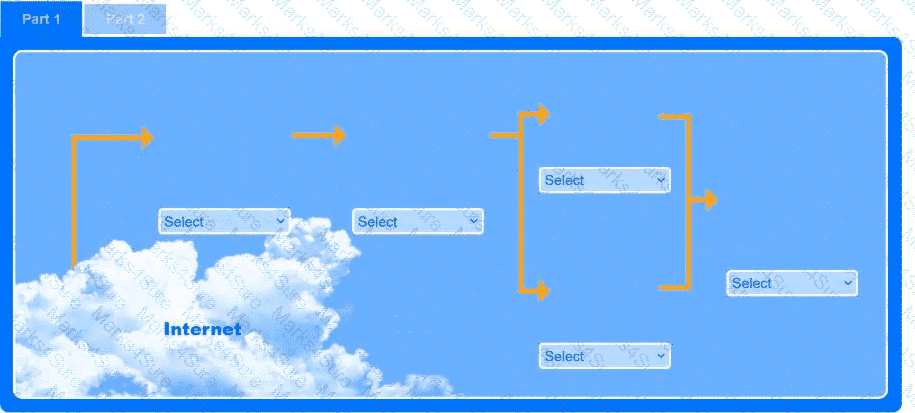
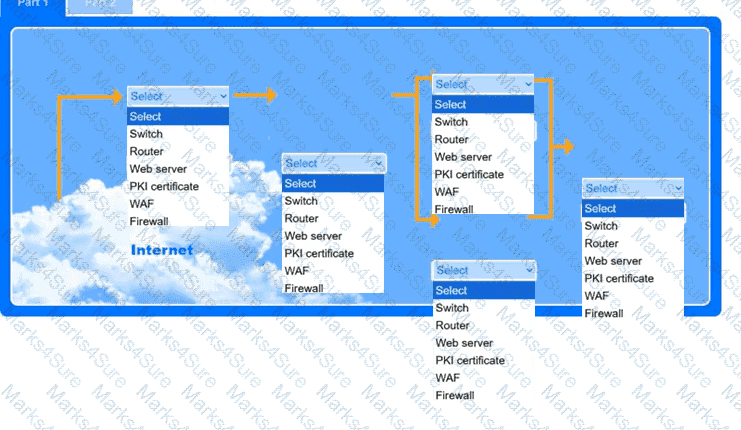
A recent black-box penetration test of http://example.com discovered that external
website vulnerabilities exist, such as directory traversals, cross-site scripting, cross-site forgery, and insecure protocols.
You are tasked with reducing the attack space and enabling secure protocols.
INSTRUCTIONS
Part 1
Use the drop-down menus to select the appropriate technologies for each location to implement a secure and resilient web architecture. Not all technologies will be used, and technologies may be used multiple times.
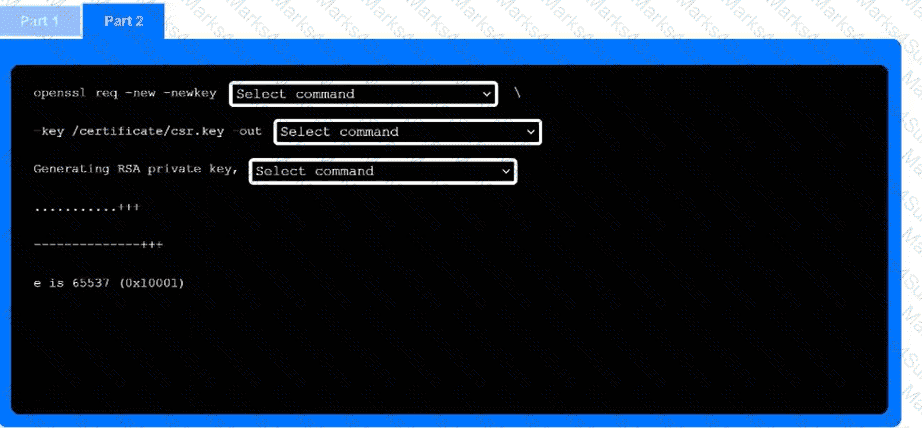
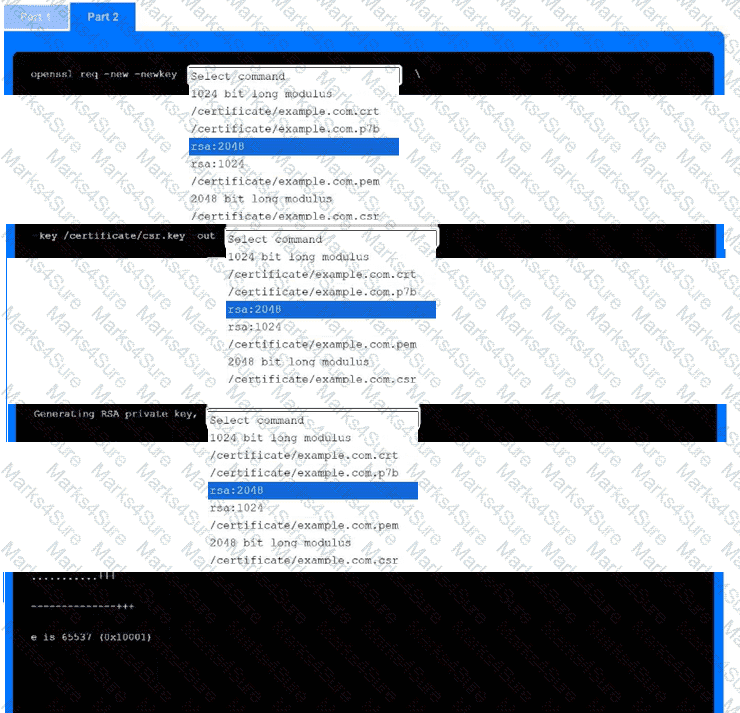
Part 2
Use the drop-down menus to select the appropriate command snippets from the drop-down menus. Each command section must be filled.
Which of the following agreement types defines the time frame in which a vendor needs to respond?
A company's end users are reporting that they are unable to reach external websites. After reviewing the performance data for the DNS severs, the analyst discovers that the CPU, disk, and memory usage are minimal, but the network interface is flooded with inbound traffic. Network logs show only a small number of DNS queries sent to this server. Which of the following best describes what the security analyst is seeing?
An organization is struggling with scaling issues on its VPN concentrator and internet circuit due to remote work. The organization is looking for a software solution that will allow it to reduce traffic on the VPN and internet circuit, while still providing encrypted tunnel access to the data center and monitoring of remote employee internet traffic. Which of the following will help achieve these objectives?
Which of the following is a type of vulnerability that may result from outdated algorithms or keys?
Which of the following describes the understanding between a company and a client about what will be provided and the accepted time needed to provide the company with the resources?
A company is in the process of cutting jobs to manage costs. The Chief Information Security Officer is concerned about the increased risk of an insider threat. Which of the following would most likely help the security awareness team address this potential threat?
Which of the following provides the best protection against unwanted or insecure communications to and from a device?
The Chief Information Officer (CIO) asked a vendor to provide documentation detailing the specific objectives within the compliance framework that the vendor's services meet. The vendor provided a report and a signed letter stating that the services meet 17 of the 21 objectives. Which of the following did the vendor provide to the CIO?
Which of the following allows an exploit to go undetected by the operating system?
A penetration tester visits a client’s website and downloads the site's content. Which of the following actions is the penetration tester performing?
Which of the following is used to quantitatively measure the criticality of a vulnerability?
Which of the following is the best way to remove personal data from a social media account that is no longer being used?
A company is using a legacy FTP server to transfer financial data to a third party. The legacy system does not support SFTP, so a compensating control is needed to protect the sensitive, financial data in transit. Which of the following would be the most appropriate for the company to use?
A company decided to reduce the cost of its annual cyber insurance policy by removing the coverage for ransomware attacks.
Which of the following analysis elements did the company most likely use in making this decision?
A company plans to secure its systems by:
Preventing users from sending sensitive data over corporate email
Restricting access to potentially harmful websites
Which of the following features should the company set up? (Select two).
An employee from the accounting department logs in to the website used for processing the company's payments. After logging in, a new desktop application automatically downloads on the employee's computer and causes the computer to restart. Which of the following attacks has occurred?
A program manager wants to ensure contract employees can only use the company’s computers Monday through Friday from 9 a.m. to 5 p.m. Which of the following would best enforce this access control?
One of a company's vendors sent an analyst a security bulletin that recommends a BIOS update. Which of the following vulnerability types is being addressed by the patch?
A systems administrate wants to implement a backup solution. the solution needs to allow recovery of the entire system, including the operating system, in case of a disaster. Which of the following backup types should the administrator consider?
Which of the following security controls is a company implementing by deploying HIPS? (Select two)
A business provides long-term cold storage services to banks that are required to follow regulator-imposed data retention guidelines. Banks that use these services require that data is disposed of in a specific manner at the conclusion of the regulatory threshold for data retention. Which of the following aspects of data management is the most important to the bank in the destruction of this data?
Which of the following security control types does an acceptable use policy best represent?
Which of the following is the best way to consistently determine on a daily basis whether security settings on servers have been modified?
A company prevented direct access from the database administrators’ workstations to the network segment that contains database servers. Which of the following should a database administrator use to access the database servers?
A security analyst learns that an attack vector, which was used as a part of a recent incident, was a well-known IoT device exploit. The analyst needs to review logs to identify the time of initial exploit. Which of the following logs should the analyst review first?
During a SQL update of a database, a temporary field that was created was replaced by an attacker in order to allow access to the system. Which of the following best describes this type of vulnerability?
A website user is locked out of an account after clicking an email link and visiting a different website Web server logs show the user's password was changed, even though the user did not change the password. Which of the following is the most likely cause?
Which of the following actions could a security engineer take to ensure workstations and servers are properly monitored for unauthorized changes and software?
A security analyst sees an increase of vulnerabilities on workstations after a deployment of a company group policy. Which of the following vulnerability types will the analyst most likely find on the workstations?
An organization has too many variations of a single operating system and needs to standardize the arrangement prior to pushing the system image to users. Which of the following should the organization implement first?
Which of the following should a company use to provide proof of external network security testing?
A systems administrator is concerned users are accessing emails through a duplicate site that is not run by the company. Which of the following is used in this scenario?
Which of the following is the most likely to be included as an element of communication in a security awareness program?
A security analyst is reviewing alerts in the SIEM related to potential malicious network traffic coming from an employee’s corporate laptop. The security analyst has determined that additional data about the executable running on the machine is necessary to continue the investigation. Which of the following logs should the analyst use as a data source?
Which of the following tools is best for logging and monitoring in a cloud environment?
A systems administrator wants to prevent users from being able to access data based on their responsibilities. The administrator also wants to apply the required access structure via a simplified format. Which of the following should the administrator apply to the site recovery resource group?
Which of the following should be used to ensure a device is inaccessible to a network-connected resource?
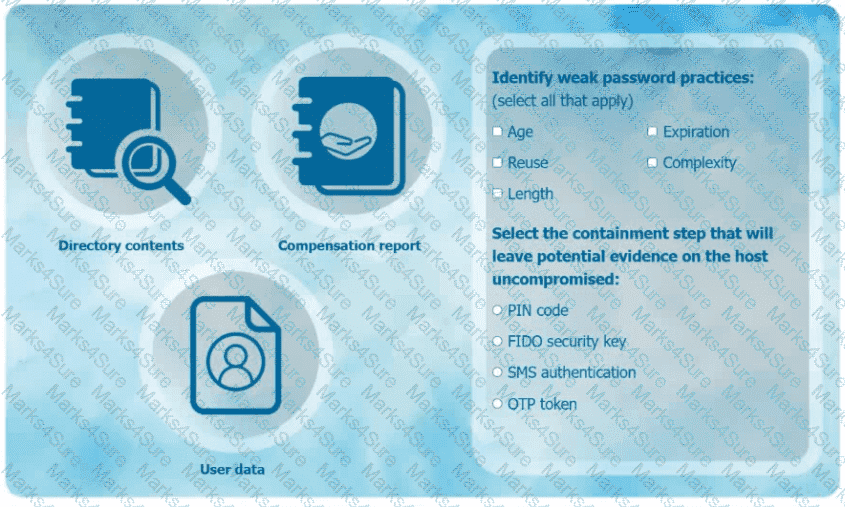
An organization has learned that its data is being exchanged on the dark web. The CIO
has requested that you investigate and implement the most secure solution to protect employee accounts.
INSTRUCTIONS
Review the data to identify weak security practices and provide the most appropriate
security solution to meet the CIO's requirements.
A penetration tester begins an engagement by performing port and service scans against the client environment according to the rules of engagement. Which of the following reconnaissance types is the tester performing?
A company implemented an MDM policy 10 mitigate risks after repealed instances of employees losing company-provided mobile phones. In several cases. The lost phones were used maliciously to perform social engineering attacks against other employees. Which of the following MDM features should be configured to best address this issue? (Select two).
Which of the following would be the best way to handle a critical business application that is running on a legacy server?
A company wants to reduce the time and expense associated with code deployment. Which of the following technologies should the company utilize?
Which of the following should an organization use to protect its environment from external attacks conducted by an unauthorized hacker?
A systems administrator is looking for a low-cost application-hosting solution that is cloud-based. Which of the following meets these requirements?
A nation-state attacker gains access to the email accounts of several journalists by compromising a website that the journalists frequently use. Which of the following types of attacks describes this example?
A security analyst developed a script to automate a trivial and repeatable task. Which of the following best describes the benefits of ensuring other team members understand how the script works?
Which of the following security principles most likely requires validation before allowing traffic between systems?
Which of the following would enable a data center to remain operational through a multiday power outage?
An IT team rolls out a new management application that uses a randomly generated MFA token sent to the administrator’s phone. Despite this new MFA precaution, there is a security breach of the same software. Which of the following describes this kind of attack?
Which of the following types of vulnerabilities involves attacking a system to access adjacent hosts?
A software development manager wants to ensure the authenticity of the code created by the company. Which of the following options is the most appropriate?
While conducting a business continuity tabletop exercise, the security team becomes concerned by potential impacts if a generator fails during failover. Which of the following is the team most likely to consider in regard to risk management activities?
An organization would like to calculate the time needed to resolve a hardware issue with a server. Which of the following risk management processes describes this example?
Which of the following is an algorithm performed to verify that data has not been modified?
A security analyst is reviewing logs and discovers the following:

Which of the following should be used lo best mitigate this type of attack?
A network security analyst monitors the network’s IDS, which has flagged unusual activity. The IDS has detected multiple login attempts to a database server within a short period. These attempts come from various IP addresses that are not normally recognized by the network’s usual traffic patterns. Each attempt uses the same username and password. Based on the following log output (corrected formatting for readability):
2025-04-10 14:22:01.4532 — Source IP: 192.168.15.101 — Status: Failed — User: JDoe — Action: Login Attempt
2025-04-10 14:22:02.1122 — Source IP: 192.168.15.102 — Status: Failed — User: JDoe — Action: Login Attempt
2025-04-10 14:22:02.7835 — Source IP: 192.168.15.103 — Status: Failed — User: JDoe — Action: Login Attempt
2025-04-10 14:22:03.5637 — Source IP: 192.168.15.104 — Status: Failed — User: JDoe — Action: Login Attempt
2025-04-10 14:22:04.9474 — Source IP: 192.168.15.105 — Status: Failed — User: JDoe — Action: Login Attempt
2025-04-10 14:22:05.5673 — Source IP: 192.168.15.106 — Status: Failed — User: JDoe — Action: Login Attempt
2025-04-10 14:22:06.1573 — Source IP: 192.168.15.107 — Status: Failed — User: JDoe — Action: Login Attempt
2025-04-10 14:22:07.7462 — Source IP: 192.168.15.108 — Status: Failed — User: JDoe — Action: Login Attempt
Which of the following types of network attacks is most likely occurring?
Which of the following activities is the first stage in the incident response process?
A security administrator is implementing encryption on all hard drives in an organization. Which of the following security concepts is the administrator applying?
Which of the following aspects of the data management life cycle is most directly impacted by local and international regulations?
Which of the following can best protect against an employee inadvertently installing malware on a company system?
A few weeks after deploying additional email servers, employees complain that messages are being marked as spam. Which needs to be updated?
A network administrator deploys an FDE solution on all end user workstations. Which of the following data protection strategies does this describe?
Which of the following architecture models ensures that critical systems are physically isolated from the network to prevent access from users with remote access privileges?
A store is setting up wireless access for employees. Management wants to limit the number of access points while ensuring full coverage. Which tool will help determine how many access points are needed?
The internal audit team determines a software application is no longer in scope for external reporting requirements. Which of the following will confirm management’s perspective that the application is no longer applicable?
A new corporate policy requires all staff to use multifactor authentication to access company resources. Which of the following can be utilized to set up this form of identity and access management? (Select two)
A security analyst discovers that a large number of employee credentials had been stolen and were being sold on the dark web. The analyst investigates and discovers that some hourly employee credentials were compromised, but salaried employee credentials were not affected.
Most employees clocked in and out while they were Inside the building using one of the kiosks connected to the network. However, some clocked out and recorded their time after leaving to go home. Only those who clocked in and out while Inside the building had credentials stolen. Each of the kiosks are on different floors, and there are multiple routers, since the business segments environments for certain business functions.
Hourly employees are required to use a website called acmetimekeeping.com to clock in and out. This website is accessible from the internet. Which of the following Is the most likely reason for this compromise?
An attacker used XSS to compromise a web server. Which of the following solutions could have been used to prevent this attack?
An organization is looking to optimize its environment and reduce the number of patches necessary for operating systems. Which of the following will best help to achieve this objective?
Which of the following should be used to select a label for a file based on the file's value, sensitivity, or applicable regulations?
Users at a company are reporting they are unable to access the URL for a new retail website because it is flagged as gambling and is being blocked.
Which of the following changes would allow users to access the site?
Which of the following is best used to detect fraud by assigning employees to different roles?
A client demands at least 99.99% uptime from a service provider's hosted security services. Which of the following documents includes the information the service provider should return to the client?
The Chief Information Security Officer wants to put security measures in place to protect PlI. The organization needs to use its existing labeling and classification system to accomplish this goal. Which of the following would most likely be configured to meet the requirements?
Which of the following technologies must be used in an organization that intends to automate infrastructure deployment?
An organization's web servers host an online ordering system. The organization discovers that the servers are vulnerable to a malicious JavaScript injection, which could allow attackers to access customer payment information. Which of the following mitigation strategies would be most effective for preventing an attack on the organization's web servers? (Select two).
An attacker posing as the Chief Executive Officer calls an employee and instructs the employee to buy gift cards. Which of the following techniques is the attacker using?
A bank insists all of its vendors must prevent data loss on stolen laptops. Which of the following strategies is the bank requiring?
The Chief Information Security Officer (CISO) requires that new servers include hardware-level memory encryption. Which of the following data states does the CISO want to protect?
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 002.1X for access control. To be allowed on the network, a device must have a Known hardware address, and a valid user name and password must be entered in a captive portal. The following is the audit report:
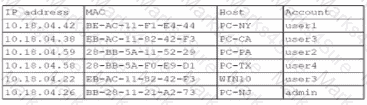
Which of the following is the most likely way a rogue device was allowed to connect?
Which of the following digital forensics activities would a security team perform when responding to legal requests in a pending investigation?
An organization is implementing a COPE mobile device management policy. Which of the following should the organization include in the COPE policy? (Select two).
An employee clicks a malicious link in an email that appears to be from the company's Chief Executive Officer. The employee's computer is infected with ransomware that encrypts the company's files. Which of the following is the most effective way for the company to prevent similar incidents in the future?
Which of the following methods to secure credit card data is best to use when a requirement is to see only the last four numbers on a credit card?
An attorney prints confidential documents to a copier in an office space near multiple workstations and a reception desk. When the attorney goes to the copier to retrieve the documents, the documents are missing. Which of the following would best prevent this from reoccurring?
A security administrator observed the following in a web server log while investigating an incident:
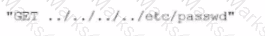
Which of the following attacks did the security administrator most likely see?
After an audit, an administrator discovers all users have access to confidential data on a file server. Which of the following should the administrator use to restrict access to the data quickly?
Security controls in a data center are being reviewed to ensure data is properly protected and that human life considerations are included. Which of the following best describes how the controls should be set up?
Which of the following prevents unauthorized modifications to internal processes, assets, and security controls?
Which of the following architectures is most suitable to provide redundancy for critical business processes?
During an investigation, an incident response team attempts to understand the source of an incident. Which of the following incident response activities describes this process?
A security team purchases a tool for cloud security posture management. The team is quickly overwhelmed by the number of misconfigurations that the tool detects. Which of the following should the security team configure to establish workflows for cloud resource security?
An administrator wants to perform a risk assessment without using proprietary company information. Which of the following methods should the administrator use to gather information?
A client asked a security company to provide a document outlining the project, the cost, and the completion time frame. Which of the following documents should the company provide to the client?
Which of the following describes the difference between encryption and hashing?
Visitors to a secured facility are required to check in with a photo ID and enter the facility through an access control vestibule Which of the following but describes this form of security control?
A company performs a risk assessment on the information security program each year. Which of the following best describes this risk assessment?
A company installed cameras and added signs to alert visitors that they are being recorded. Which of the following controls did the company implement? (Select two).
Which of the following is the best safeguard to protect against an extended power failure?
An administrator investigating an incident is concerned about the downtime of a critical server due to a failed drive. Which of the following would the administrator use to estimate the time needed to fix the issue?
A company is required to use certified hardware when building networks. Which of the following best addresses the risks associated with procuring counterfeit hardware?
Which of the following is the primary purpose of a service that tracks log-ins and time spent using the service?
Which of the following would a security administrator use to comply with a secure baseline during a patch update?
A company suffered a critical incident where 30GB of data was exfiltrated from the corporate network. Which of the following actions is the most efficient way to identify where the system data was exfiltrated from and where it was sent?
A security analyst reviews web server logs and sees the following entries:
16.22.48.102 -- 26/April/2023 22:00:04.33 GET "http://www.databaseInfo.com/index.html/* " 200
16.22.48.102 -- 26/April/2023 22:00:07.23 GET "http://www.databaseInfo.com/index.html/../ " 404
16.22.48.102 -- 26/April/2023 22:01:16.03 GET "http://www.databaseInfo.com/index.html/../images " 404
16.22.48.102 -- 26/April/2023 22:03:10.25 GET "http://www.databaseInfo.com/index.html/../passwords " 404
16.22.48.102 -- 26/April/2023 22:05:11.22 GET "http://www.databaseInfo.com/index.html/../storedSQLqueries " 404
Which of the following attacks is most likely being attempted?
An organization designs an inbound firewall with a fail-open configuration while implementing a website. Which of the following does the organization consider to be the highest priority?
A company expects its provider to ensure servers and networks maintain 97% uptime. Which of the following would most likely list this expectation?
A customer reports that software the customer downloaded from a public website has malware in it. However, the company that created the software denies any malware in its software at delivery time. Which of the following techniques will address this concern?
An IT manager informs the entire help desk staff that only the IT manager and the help desk lead will have access to the administrator console of the help desk software. Which of the following security techniques is the IT manager setting up?
Which of the following explains how a supply chain service provider could introduce a security vulnerability into an organization?
Which of the following is the most likely outcome if a large bank fails an internal PCI DSS compliance assessment?
A systems administrator is concerned about vulnerabilities within cloud computing instances Which of the following is most important for the administrator to consider when architecting a cloud computing environment?
A company wants to update its disaster recovery plan to include a dedicated location for immediate continued operations if a catastrophic event occurs. Which of the following options is best to include in the disaster recovery plan?
A systems administrator creates a script that validates OS version, patch levels, and installed applications when users log in. Which of the following examples best describes the purpose of this script?
Which of the following is the greatest advantage that network segmentation provides?
A business uses Wi-Fi with content filleting enabled. An employee noticed a coworker accessed a blocked sue from a work computer and repotted the issue. While Investigating the issue, a security administrator found another device providing internet access to certain employees. Which of the following best describes the security risk?
A security analyst reviews domain activity logs and notices the following:

Which of the following is the best explanation for what the security analyst has discovered?
A financial institution would like to store its customer data m the cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution Is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would best meet the requirement?
Cadets speaking a foreign language are using company phone numbers to make unsolicited phone calls lo a partner organization. A security analyst validates through phone system logs that the calls are occurring and the numbers are not being spoofed. Which of the following is the most likely explanation?
Which of the following allows a systems administrator to tune permissions for a file?
Which of the following explains why an attacker cannot easily decrypt passwords using a rainbow table attack?
Which of the following is most likely associated with introducing vulnerabilities on a corporate network by the deployment of unapproved software?
A security engineer needs to quickly identify a signature from a known malicious file. Which of the following analysis methods would the security engineer most likely use?
Which of the following threat actors would most likely deface the website of a high-profile music group?
A company asks a vendor to help its internal red team with a penetration test without providing too much detail about the infrastructure. Which of the following penetration testing methods does this scenario describe?
Which of the following would best prepare a security team for a specific incident response scenario?
An employee clicked a link in an email from a payment website that asked the employee to update contact information. The employee entered the log-in information but received a “page not found” error message. Which of the following types of social engineering attacks occurred?
A company needs to provide administrative access to internal resources while minimizing the traffic allowed through the security boundary. Which of the following methods is most secure?
Which of the following best describes why me SMS DIP authentication method is more risky to implement than the TOTP method?
A software developer released a new application and is distributing application files via the developer’s website. Which of the following should the developer post on the website to allow users to verify the integrity of the downloaded files?
A security audit of an organization revealed that most of the IT staff members have domain administrator credentials and do not change the passwords regularly. Which of the following solutions should the security learn propose to resolve the findings in the most complete way?
A security manager wants to reduce the number of steps required to identify and contain basic threats. Which of the following will help achieve this goal?
A technician needs to apply a high-priority patch to a production system. Which of the following steps should be taken first?
A security team receives reports about high latency and complete network unavailability throughout most of the office building. Flow logs from the campus switches show high traffic on TCP 445. Which of the following is most likely the root cause of this incident?
An organization needs to monitor its users' activities to prevent insider threats. Which of the following solutions would help the organization achieve this goal?
Which of the following should an internal auditor check for first when conducting an audit of the organization's risk management program?
A company is in the process of migrating to cloud-based services. The company's IT department has limited resources for migration and ongoing support. Which of the following best meets the company's needs?
A security analyst is reviewing the following logs:

Which of the following attacks is most likely occurring?
Which of the following would be the best solution to deploy a low-cost standby site that includes hardware and internet access?
An administrator needs to perform server hardening before deployment. Which of the following steps should the administrator take? (Select two).
An organization has recently decided to implement SSO. The requirements are to leverage access tokens and focus on application authorization rather than user authentication. Which of the following solutions would the engineering team most likely configure?
A security analyst is creating base for the server team to follow when hardening new devices for deployment. Which of the following beet describes what the analyst is creating?
An employee clicked a malicious link in an email and downloaded malware onto the company's computer network. The malicious program exfiltrated thousands of customer records. Which of the following should the company implement to prevent this in the future?
A security analyst is investigating an alert that was produced by endpoint protection software. The analyst determines this event was a false positive triggered by an employee who attempted to download a file. Which of the following is the most likely reason the download was blocked?
The marketing department set up its own project management software without telling the appropriate departments. Which of the following describes this scenario?
A company's online shopping website became unusable shortly after midnight on January 30, 2023. When a security analyst reviewed the database server, the analyst noticed the following code used for backing up data:
Which of the following should the analyst do next?
Which of the following is the act of proving to a customer that software developers are trained on secure coding?
Which of the following would best ensure a controlled version release of a new software application?
A company’s legal department drafted sensitive documents in a SaaS application and wants to ensure the documents cannot be accessed by individuals in high-risk countries. Which of the following is the most effective way to limit this access?
Which of the following examples would be best mitigated by input sanitization?
While considering the organization's cloud-adoption strategy, the Chief Information Security Officer sets a goal to outsource patching of firmware, operating systems, and applications to the chosen cloud vendor. Which of the following best meets this goal?
Which of the following should a security operations center use to improve its incident response procedure?
A company is considering an expansion of access controls for an application that contractors and internal employees use to reduce costs. Which of the following risk elements should the implementation team understand before granting access to the application?
Which of the following are cases in which an engineer should recommend the decommissioning of a network device? (Select two).
Which of the following topics would most likely be included within an organization's SDLC?
A user is attempting to patch a critical system, but the patch fails to transfer. Which of the following access controls is most likely inhibiting the transfer?
Which of the following best describe the benefits of a microservices architecture when compared to a monolithic architecture? (Select two).
A remote employee navigates to a shopping website on their company-owned computer. The employee clicks a link that contains a malicious file. Which of the following would prevent this file from downloading?
A company wants to use new Wi-Fi-enabled environmental sensors to automatically collect metrics. Which of the following will the security team most likely do?
A company decides to purchase an insurance policy. Which of the following risk management strategies is this company implementing?
An employee receives a text message that appears to have been sent by the payroll department and is asking for credential verification. Which of the following social engineering techniques are being attempted? (Choose two.)
During a penetration test in a hypervisor, the security engineer is able to inject a malicious payload and access the host filesystem. Which of the following best describes this vulnerability?
An organization has been experiencing issues with deleted network share data and improperly assigned permissions. Which of the following would best help track and remediate these issues?
Which of the following outlines the configuration, maintenance, and security roles between a cloud service provider and the customer?
During a penetration test in a hypervisor, the security engineer is able to use a script to inject a malicious payload and access the host filesystem. Which of the following best describes this vulnerability?
A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
Which of the following security concepts is accomplished with the installation of a RADIUS server?
During an investigation, a security analyst discovers traffic going out to a command-and-control server. The analyst must find out if any data exfiltration has occurred. Which of the following would best help the analyst determine this?
An administrator has configured a quarantine subnet for all guest devices that connect to the network. Which of the following would be best for the security team to configure on the MDM before allowing access to corporate resources?
A Chief Security Officer signs off on a request to allow inbound SMB and RDP from the internet to a single VLAN. Which of the following is the most likely explanation for this activity?
During a penetration test, a vendor attempts to enter an unauthorized area using an access badge Which of the following types of tests does this represent?
A new employee logs in to the email system for the first time and notices a message from human resources about onboarding. The employee hovers over a few of the links within the email and discovers that the links do not correspond to links associated with the company. Which of the following attack vectors is most likely being used?
A penetration test identifies that an SMBvl Is enabled on multiple servers across an organization. The organization wants to remediate this vulnerability in the most efficient way possible. Which of the following should the organization use for this purpose?
A systems administrator needs to provide traveling employees with a tool that will protect company devices regardless of where they are working. Which of the following should the administrator implement?
An administrator installs an SSL certificate on a new system. During testing, errors indicate that the certificate is not trusted. The administrator has verified with the issuing CA and has validated the private key. Which of the following should the administrator check for next?
A hacker gained access to a system via a phishing attempt that was a direct result of a user clicking a suspicious link. The link laterally deployed ransomware, which laid dormant for multiple weeks, across the network. Which of the following would have mitigated the spread?
A security team wants WAF policies to be automatically created when applications are deployed. Which concept describes this capability?
An organization has issues with deleted network share data and improper permissions. Which solution helps track and remediate these?
Which of the following is the most common data loss path for an air-gapped network?
A manufacturing organization receives the results from a penetration test. According to the results, legacy devices that are critical to continued business function display vulnerabilities. The devices have minimal vendor support and should be segmented and monitored closely. Which of the following devices were most likely identified?
A company plans to secure its systems by:
Preventing users from sending sensitive data over corporate email
Restricting access to potentially harmful websites
Which of the following features should the company set up? (Select two).
Which of the following should be used to ensure an attacker is unable to read the contents of a mobile device's drive if the device is lost?
Which of the following techniques can be used to sanitize the data contained on a hard drive while allowing for the hard drive to be repurposed?
A security manager created new documentation to use in response to various types of security incidents. Which of the following is the next step the manager should take?
A company is currently utilizing usernames and passwords, and it wants to integrate an MFA method that is seamless, can Integrate easily into a user's workflow, and can utilize employee-owned devices. Which of the following will meet these requirements?
After a security incident, a systems administrator asks the company to buy a NAC platform. Which of the following attack surfaces is the systems administrator trying to protect?
Which security controls is a company implementing by deploying HIPS? (Select two)
Which of the following can assist in recovering data if the decryption key is lost?
Which of the following vulnerabilities is associated with installing software outside of a manufacturer’s approved software repository?
After a recent ransomware attack on a company's system, an administrator reviewed the log files. Which of the following control types did the administrator use?
A company processes and stores sensitive data on its own systems. Which of the following steps should the company take first to ensure compliance with privacy regulations?
A systems administrator receives a text message from an unknown number claiming to be the Chief Executive Officer of the company. The message states an emergency situation requires a password reset. Which of the following threat vectors is being used?
Which of the following would most likely prevent exploitation of an end-of-life, business-critical system?
Which of the following enables the use of an input field to run commands that can view or manipulate data?
Which of the following is required for an organization to properly manage its restore process in the event of system failure?
Which of the following is a compensating control for providing user access to a high-risk website?
An administrator assists the legal and compliance team with ensuring information about customer transactions is archived for the proper time period. Which of the following data policies is the administrator carrying out?
Which of the following is a type of vulnerability that refers to the unauthorized installation of applications on a device through means other than the official application store?
Which of the following best describes the practice of researching laws and regulations related to information security operations within a specific industry?
A security administrator recently reset local passwords and the following values were recorded in the system:
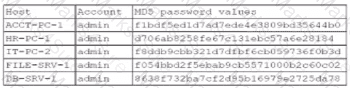
Which of the following in the security administrator most likely protecting against?
A company is redesigning its infrastructure and wants to reduce the number of physical servers in use. Which of the following architectures is best suited for this goal?
Which of the following is the best mitigation for a zero-day vulnerability found in mission-critical production servers that must be highly available?
An attacker submits a request containing unexpected characters in an attempt to gain unauthorized access to information within the underlying systems. Which of the following best describes this attack?
Which of the following solutions would most likely be used in the financial industry to mask sensitive data?
An administrator at a small business notices an increase in support calls from employees who receive a blocked page message after trying to navigate to a spoofed website. Which of the following should the administrator do?