A developer wants to ensure that all files and folders created inside a shared folder named /GroupOODEV inherit the group name of the parent folder. Which of the following commands will help achieve this goal?
A systems administrator has been tasked with disabling the nginx service from the environment to prevent it from being automatically and manually started. Which of the following commands will accomplish this task?
A cloud engineer needs to block the IP address 192.168.10.50 from accessing a Linux server. Which of the following commands will achieve this goal?
A Linux administrator deployed a large-scale application service as a containerized pod. The Linux administrator needs to continually send the application's log file to the company’s central log store. Which of the following should the Linux administrator do to efficiently perform this task?
Which of the following directories contains binaries that only a root user should run?
Based on an organization’s new cybersecurity policies, an administrator has been instructed to ensure that, by default, all new users and groups that are created fall within the specified values below.
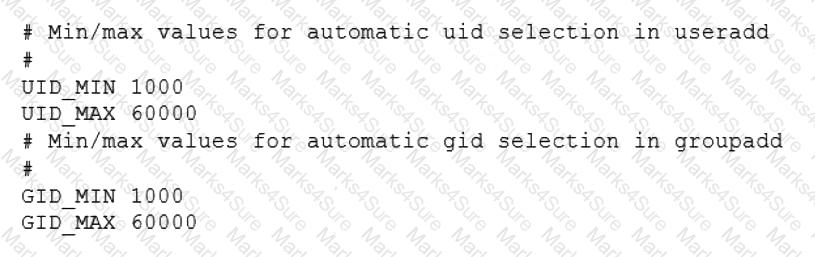
To which of the following configuration files will the required changes need to be made?
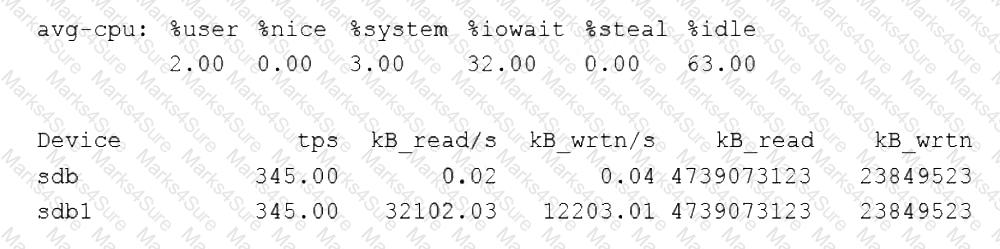
Users are reporting that a Linux server is responding slowly. A systems administrator troubleshooting the server issue sees the following:
# iostat -m 2
Linux 3.10.0-1160.66.1.el7.x86_64 (myhost) 10/19/2022 x86_64 (4 CPU)
avg-cpu: %user %nice %system %iowait %steal %idle
24.30 0.01 0.29 50.38 4.00 19.01
Device: tps MB_read/s MB_wrtn/s MB_read MB_wrtn
sdd 15.65 0.48 0.83 4936250 8513501
# df -h
Filesystem Size Used Avail Use% Mounted on
devtmpfs 16G 0 16G 0% /dev
tmpfs 16G 64K 16G 1% /dev/shm
/dev/mapper/root 35G 8.8G 26G 26% /
/dev/sda2 497M 144M 354M 29% /boot
/dev/mapper/tmp 10G 38M 10G 1% /tmp
/dev/mapper/var 15G 13G 2.2G 86% /var
/dev/mapper/varlib 650G 397G 254G 62% /var/lib
/dev/mapper/varlog 15G 9.5G 5.5G 64% /var/log
/dev/mapper/varaudit 15G 72M 15G 1% /var/log/audit
Which of the following is most likely the issue?
An administrator accidentally deleted the /boot/vmlinuz file and must resolve the issue before the server is rebooted. Which of the following commands should the administrator use to identify the correct
version of this file?
An administrator is running a web server in a container named WEB, but none of the error output is showing. Which of the following should the administrator use to generate the errors on the container?
A Linux systems administrator needs to compress a file named passwords.txt. The compressed file should be saved as passwords.txt.gz. Which of the following commands should the administrator use to accomplish this task?
The group owner of the / home/ test directory would like to preserve all group permissions on files created in the directory. Which of the following
commands should the group owner execute?
Due to performance issues on a server, a Linux administrator needs to terminate an unresponsive process. Which of the following commands should the administrator use to terminate the process immediately without waiting for a graceful shutdown?
A developer needs to launch an Nginx image container, name it Web001, and ex-pose port 8080 externally while mapping to port 80 inside the container. Which of the following commands will accomplish this task?
An administrator accidentally installed the httpd RPM package along with several dependencies. Which of the following options is the best way for the administrator to revert the package installation?
A systems administrator frequently connects to a remote host via SSH and a non-standard port. The systems administrator would like to avoid passing the port parameter on the command line every time. Which of the following files can be used to set a different port value for that host?
Users are reporting that a Linux server is responding slowly. A systems administrator troubleshooting the server issue sees the following iostat output, with %iowait at 50.38. Which of the following is most likely the issue?
Using AD Query, the security gateway connections to the Active Directory Domain Controllers using what protocol?
A systems administrator is tasked with installing GRUB on the legacy MBR of the SATA hard drive. Which of the following commands will help the administrator accomplish this task?
A Linux administrator is trying to remove the ACL from the file /home/user/data. txt but receives the following error message:
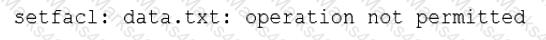
Given the following analysis:
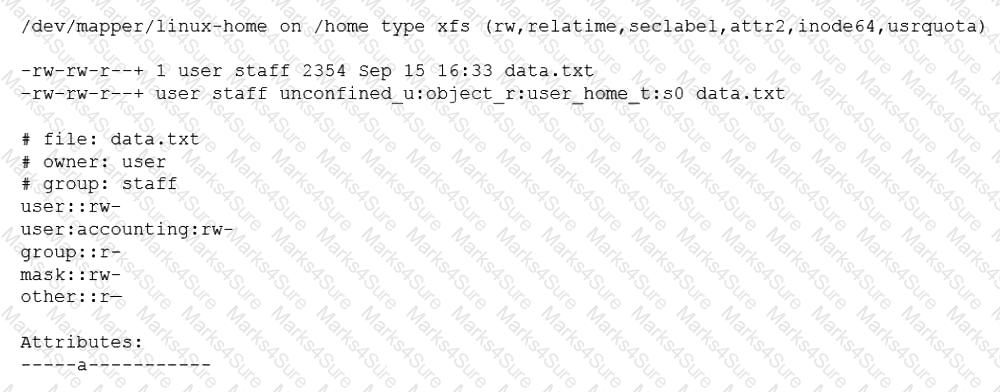
Which of the following is causing the error message?
A junior systems administrator recently installed an HBA card in one of the servers that is deployed for a production environment. Which of the following
commands can the administrator use to confirm on which server the card was installed?
Which of the following technologies provides load balancing, encryption, and observability in containerized environments?
A new file was added to a main Git repository. An administrator wants to synchronize a local copy with the contents of the main repository. Which of the following commands should the administrator use for this task?
A Linux systems administrator is configuring a new filesystem that needs the capability to be mounted persistently across reboots. Which of the following commands will accomplish this task? (Choose two.)
A systems engineer has deployed a new application server, but the server cannot communicate with the backend database hostname. The engineer confirms that the application server can ping the database server's IP address. Which of the following is the most likely cause of the issue?
A cloud engineer is installing packages during VM provisioning. Which of the following should the engineer use to accomplish this task?
Users are reporting that writes on a system configured with SSD drives have been taking longer than expected, but reads do not seem to be affected. A Linux systems administrator is investigating this issue and working on a solution. Which of the following should the administrator do to help solve the issue?
A systems administrator needs to reconfigure a Linux server to allow persistent IPv4 packet forwarding. Which of the following commands is the correct way to accomplish this task?
A Linux administrator is implementing a stateful firewall on the Linux server. Which of the following iptables options will be required to build the stateful rules? (Select two).
Employees in the finance department are having trouble accessing the file /opt/work/file. All IT employees can read and write the file. Systems administrator reviews the following output:
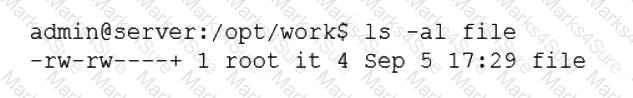
Which of the following commands would permanently fix the access issue while limiting access to IT and finance department employees?
A Linux administrator needs to remove all local firewall rules on a Linux system. Which of the following commands should the administrator run?
A systems administrator notices the process list on a mission-critical server has a large number of processes that are in state "Z" and marked as "defunct." Which of the following should the administrator do in an attempt to safely remove these entries from the process list?
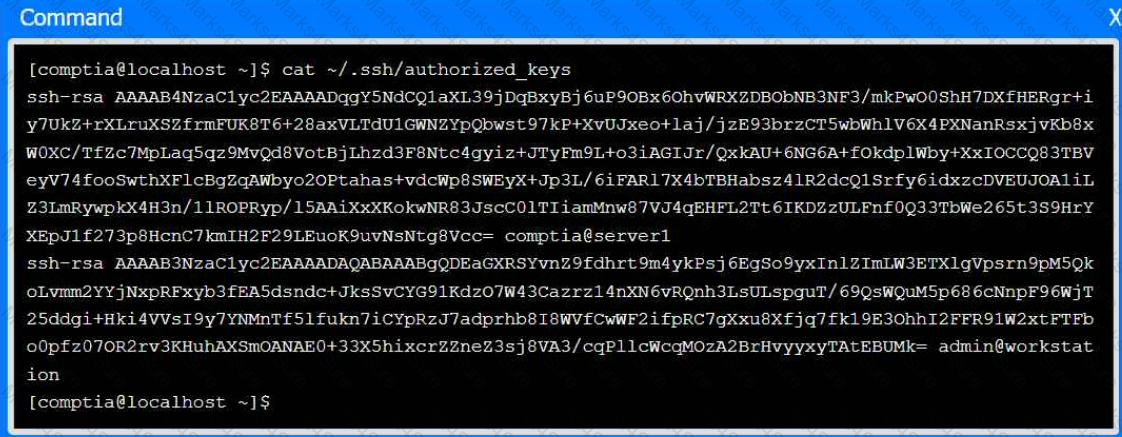
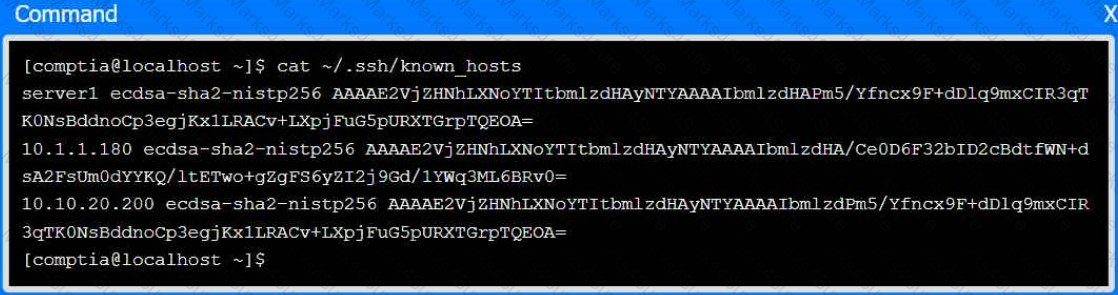
An administrator transferred a key for SSH authentication to a home directory on a remote server. The key file was moved to .ssh/authorized_keys location in order to establish SSH connection without a password. However, the SSH command still asked for the password. Given the following output:

Which of the following commands would resolve the issue?
A systems administrator needs to check if the service systemd-resolved.service is running without any errors. Which of the following commands will show this information?
A technician just fixed a few issues in some code and is ready to deploy the code into production. Which of the following steps should the technician take next?
A systems administrator wants to upgrade /bin/ someapp to a new version, but the administrator does not know the package name. Which of the following will
show the RPM package name that provides that binary file?
A Linux administrator is tasked with moving files in a database server. The administrator must not overwrite any existing files. Which of the following commands would indicate that the file already exists?
Which of the following files holds the system configuration for journal when running systemd?
An administrator is trying to diagnose a performance issue and is reviewing the following output:
System Properties:
CPU: 4 vCPU
Memory: 40GB
Disk maximum IOPS: 690
Disk maximum throughput: 44Mbps | 44000Kbps
Based on the above output, which of the following BEST describes the root cause?
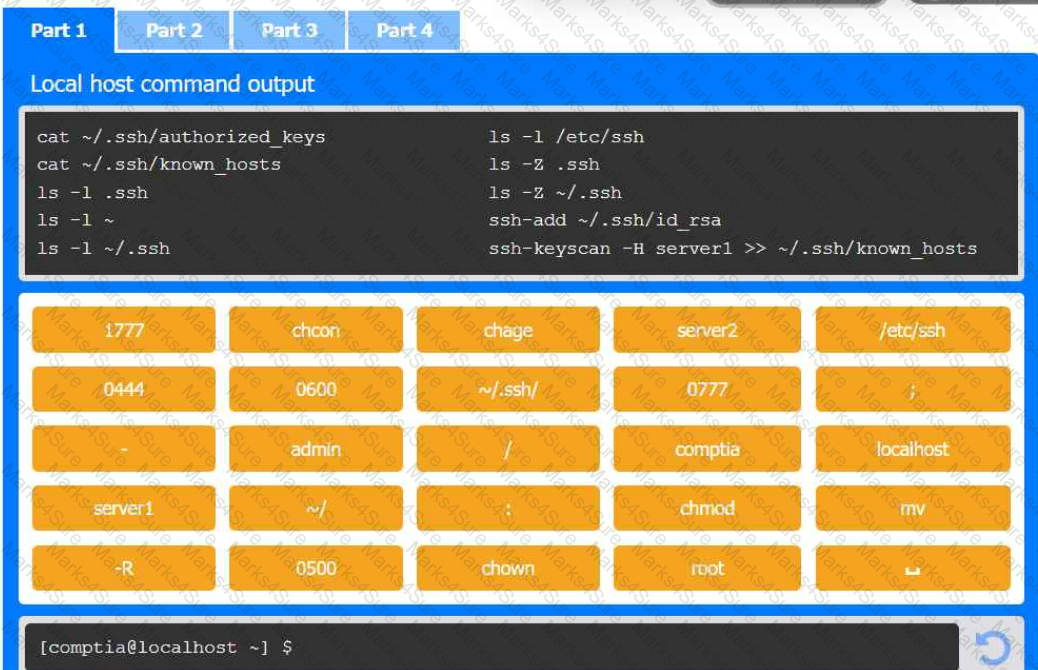
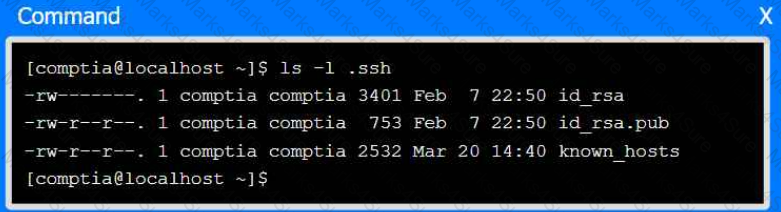
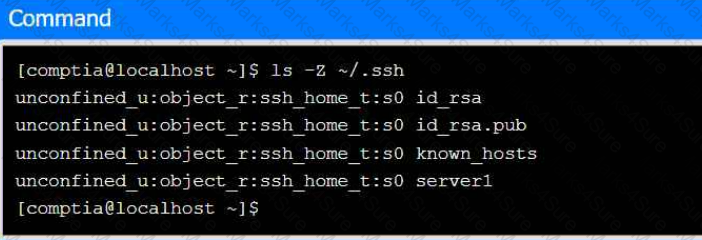
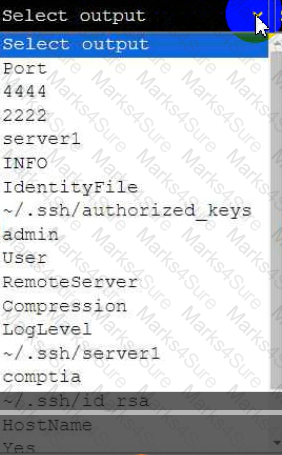
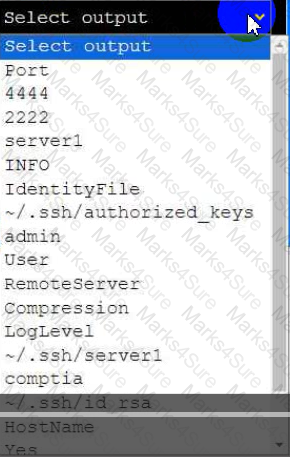
A senior administrator has placed a private key for user admin in your home directory.
The server you need to remotely access is server1 and SSH is listening on port 2222.
INSTRUCTIONS
Part 1
Review the command output and build the correct command to place the private key
into your SSH folder.
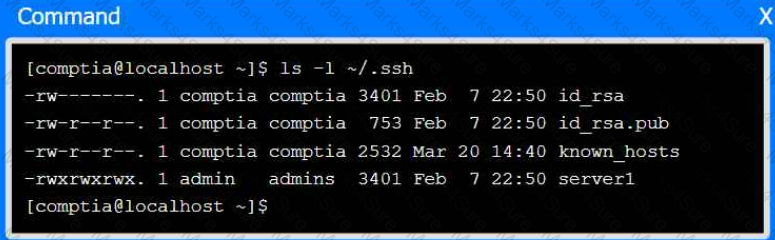
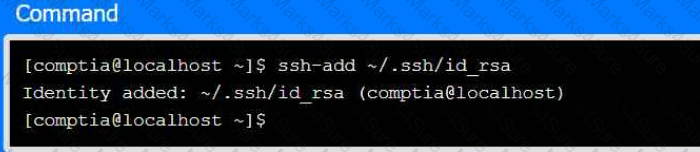
Part 2
Review the command output and build the correct command to set the file
permissions.
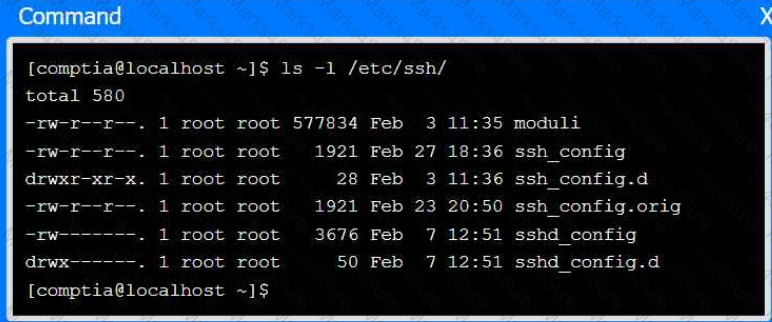
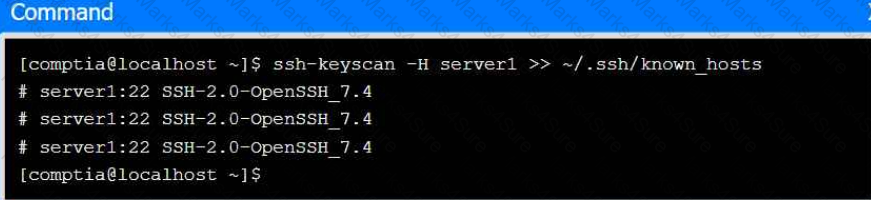
Part 3
Review the command output and build the correct command to set the correct
ownership.
In each part, click on objects to build a complete command. Command objects may
be used more than once, but not all will be used. Use _ as the spacebar. Click the
arrow to remove any unwanted objects from your command.
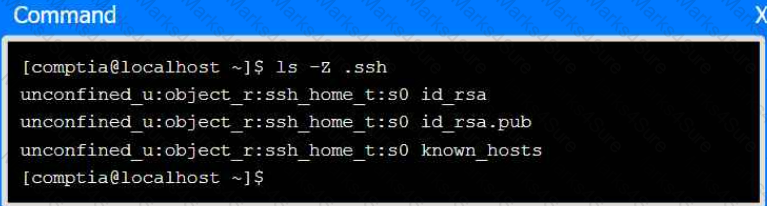
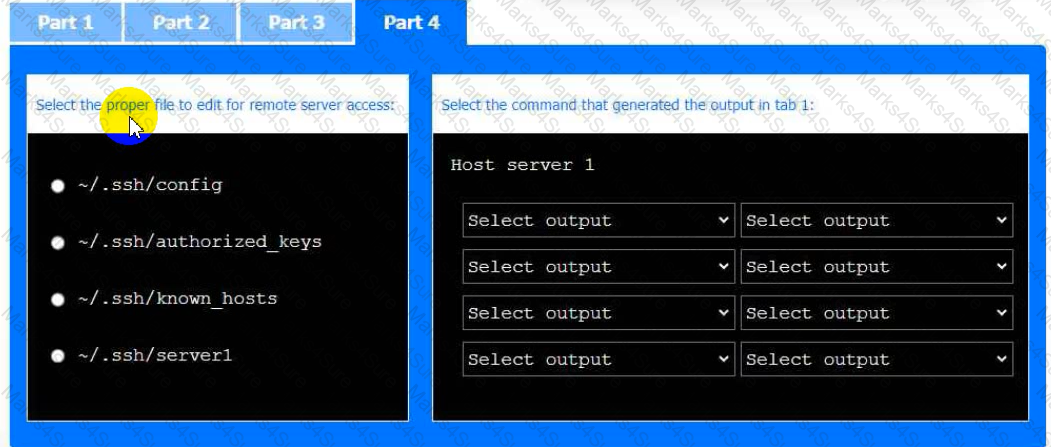
Part 4
Select the proper file to edit for remote server access. Then, build the correct
configuration output based on the server name, ports, and files.
A Linux administrator would like to measure possible packet loss between a workstation and a remote web application that is running on port 443. Which of the following would be the best command for the administrator to use to display this information?
A Linux administrator needs to determine if prerequisites are met. One of the application requirements is to install Perl on a system. Which of the following commands would accomplish this task?
An administrator needs to get network information from a group of statically assigned workstations before they are reconnected to the network. Which of the following should the administrator use to obtain this information?
One leg of an LVM-mirrored volume failed due to the underlying physical volume, and a systems administrator is troubleshooting the issue. The following output has been provided:
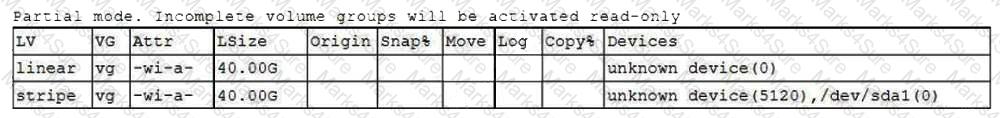
Given this scenario, which of the following should the administrator do to recover this volume?
A Linux administrator was asked to run a container with the httpd server inside. This container should be exposed at port 443 of a Linux host machine while it internally listens on port 8443. Which of the following commands will accomplish this task?
A junior administrator is setting up a new Linux server that is intended to be used as a router at a remote site. Which of the following parameters will accomplish this goal?
A Linux systems administrator receives a notification that one of the server’s filesystems is full. Which of the following commands would help the administrator to identify this filesystem?
A Linux administrator needs to harden a system and guarantee that the Postfix service will not run, even after a restart or system upgrade. Which of the following commands allows the administrator to fulfill the requirement?
A Linux administrator needs to transfer a local file named accounts . pdf to a remote / tmp directory of a server with the IP address 10.10.10.80. Which of the following commands needs to be executed to transfer this file?
When trying to log in remotely to a server, a user receives the following message:
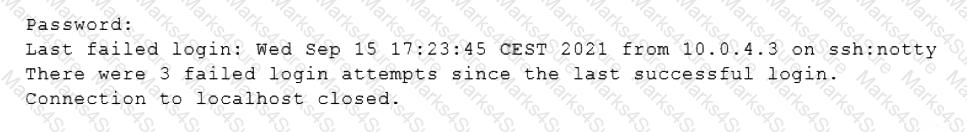
The server administrator is investigating the issue on the server and receives the following outputs:
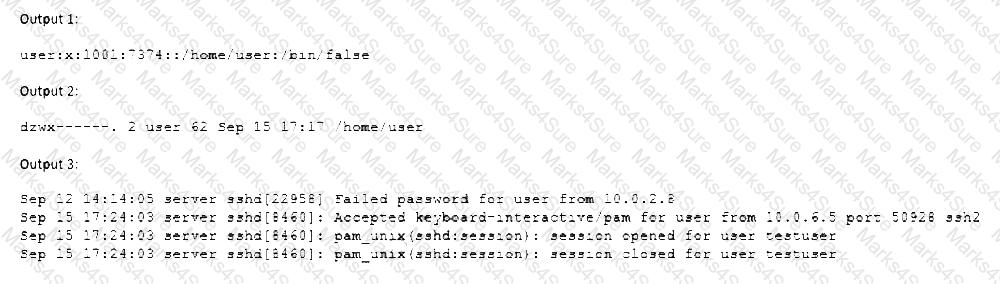
Which of the following is causing the issue?
A Linux administrator wants to set the SUID of a file named dev_team.text with 744 access rights. Which of the following commands will achieve this goal?
A Linux system is failing to start due to issues with several critical system processes. Which of the following options can be used to boot the system into the single user mode? (Choose two.)
A Linux administrator is creating a primary partition on the replacement hard drive for an application server. Which of the following commands should the administrator issue to verify the device name of this partition?
A Linux system is having issues. Given the following outputs:
# dig @192.168.2.2 mycomptiahost
; << >> DiG 9.9.4-RedHat-9.9.4-74.el7_6.1 << >> @192.168.2.2 mycomptiahost
; (1 server found)
;; global options: +cmd
;; connection timed out; no servers could be reached
# nc -v 192.168.2.2 53
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Connection timed out.
# ping 192.168.2.2
PING 192.168.2.2 (192.168.2.2) 56(84) bytes of data.
64 bytes from 192.168.2.2: icmp_seq=1 ttl=117 time=4.94 ms
64 bytes from 192.168.2.2: icmp_seq=2 ttl=117 time=10.5 ms
Which of the following best describes this issue?
A systems administrator receives the following errors via email from the system log:
go
XFS (loop0): Metadata CRC error detected at xfs_agi_read_verify+0xcb/0xfe
XFS (loop0): First 128 bytes of corrupted metadata buffer
XFS (loop0): metadata I/O error in "xfs_trans_read_buf_map" at daddr 0x2 len 1 error 74
A few minutes later, the administrator starts receiving reports that some of the images in the company's website are not loading properly. The systems administrator runs some commands and receives the following outputs:
css
Output 1
NAME FSTYPE UUID MOUNTPOINT
sda ext4 02ae47-fe457-45bc /
sdb xfs 347c7056 /var/www/html
Output 2
DocumentRoot "/var/www/html"
Output 3
httpd.service - The Apache HTTP Server
Loaded: loaded (/usr/lib/systemd/system/httpd.service; enabled; vendor preset: disabled)
Active: active (running) since Sun 1991-05-24 16:12:43 UTC; 30y ago
Main PID: 252 (httpd)
Which of the following would be the appropriate steps to take to solve this issue?
A user is cleaning up a directory because it has more than 100,000 files that were generated from an experiment. When the user tries to remove the unneeded experiment files, the user receives an error:
arduino
cannot execute [Argument list too long]
Which of the following should the user execute to remove these files?
A systems administrator is enabling LUKS on a USB storage device with an ext4 filesystem format. The administrator runs dmesg and notices the following output:

Given this scenario, which of the following should the administrator perform to meet these requirements? (Select three).
A junior administrator updated the PostgreSQL service unit file per the data-base administrator's recommendation. The service has been restarted, but changes have not been applied. Which of the following should the administrator run for the changes to take effect?
A systems administrator needs to remove a disk from a Linux server. The disk size is 500G, and it is the only one that size on that machine. Which of the following commands can the
administrator use to find the corresponding device name?
A systems administrator wants to back up the directory /data and all its contents to /backup/data on a remote server named remote. Which of the following commands will achieve the desired effect?
The development team wants to prevent a file from being modified by all users in a Linux system, including the root account. Which of the following commands can be used to accomplish this objective?
The users of a Linux system are unable to use one of the application filesystems. The following outputs have been provided:
bash
$ cd /app
$ touch file
touch: cannot touch 'file': Readonly file system
Output 2
/dev/sdcl on /app type ext4 (ro,relatime,seclabel,data=ordered)
Output 3
/dev/sdcl /app ext4 defaults 0 0
Output 4
[302.048075] Buffer I/O error on dev sdcl, logical block 0, async page read
[302.048490] EXT4-fs (sdcl): Attempt to read block from filesystem resulted in short read while trying to re-open /dev/sdcl
Which of the following actions will resolve this issue?
A systems administrator is receiving complaints about slow performance and system crashes. The administrator suspects memory and CPU issues. Which of the following is the first action the administrator should take to troubleshoot and resolve these issues?
A Linux administrator is implementing a CI/CD process for the company’s internal accounting web application. Which of the following best defines the purpose of this process?
A systems administrator configured firewall rules using firewalld. However, after the system is rebooted, the firewall rules are not present:
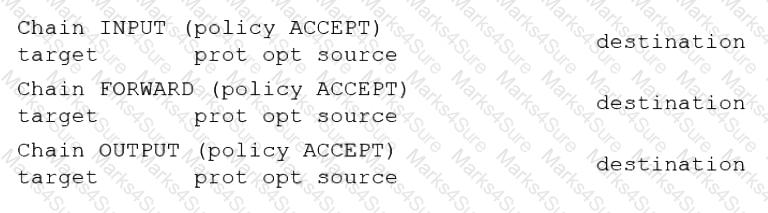
The systems administrator makes additional checks:
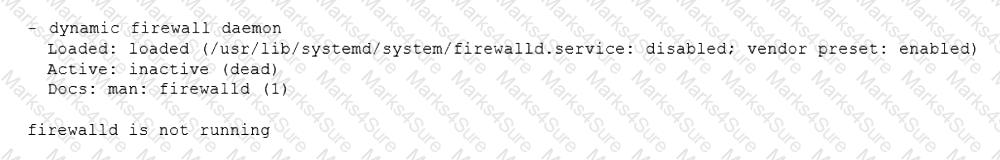
Which of the following is the reason the firewall rules are not active?
The group named support is unable to make changes to the config file. An administrator is reviewing the permissions and sees the following:
S Is -1 config
-rw-rw----. 1 root app 4682 02-15 11:25 config
Which of the following should the administrator execute in order to give the support group access to modify the file while preserving the current ownership?
An administrator would like to list all current containers, regardless of their running state. Which of the following commands would allow the administrator to accomplish this task?
A Linux engineer finds multiple failed login entries in the security log file for application users. The Linux engineer performs a security audit and discovers a security issue. Given the following:
# grep -iE '*www*|db' /etc/passwd
www-data:x:502:502:www-data:/var/www:/bin/bash
db:x: 505:505:db: /opt/db:/bin/bash
Which of the following commands would resolve the security issue?
Application code is stored in Git. Due to security concerns, the DevOps engineer does not want to keep a sensitive configuration file, app . conf, in the
repository. Which of the following should the engineer do to prevent the file from being uploaded to the repository?
A Linux administrator needs to resolve a service that has failed to start. The administrator runs the following command:

The following output is returned
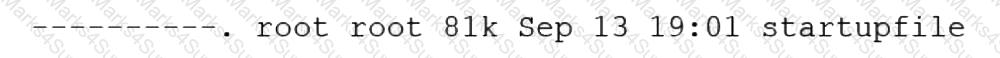
Which of the following is MOST likely the issue?
A Linux administrator wants to find out whether files from the wget package have been altered since they were installed. Which of the following commands will provide the correct information?
A new application container was built with an incorrect version number. Which of the following commands should be used to rename the image to match the correct version 2.1.2?
A Linux administrator needs to correct the permissions of a log file on the server. Which of the following commands should be used to set filename.log permissions to -rwxr—r--. ?
Which of the following can be used as a secure way to access a remote termi-nal?
A systems engineer deploys a new application server, but the server cannot communicate with the back-end database hostname. The engineer confirms that the application server can ping the database server's IP address. Which of the following is the most likely cause of the issue?
While troubleshooting server issues, a Linux systems administrator obtains the following output:
yaml
total used free shared buff/cache available
Mem: 3736 3538 33 2 48 25
Swap: 2047 1824 223
Which of the following best describes the state of the system?
Users in the human resources department are trying to access files in a newly created directory. Which of the following commands will allow the users access to the files?
A Linux user reported the following error after trying to connect to the system remotely:
ssh: connect to host 10.0.1.10 port 22: Resource temporarily unavailable
The Linux systems administrator executed the following commands in the Linux system while trying to diagnose this issue:
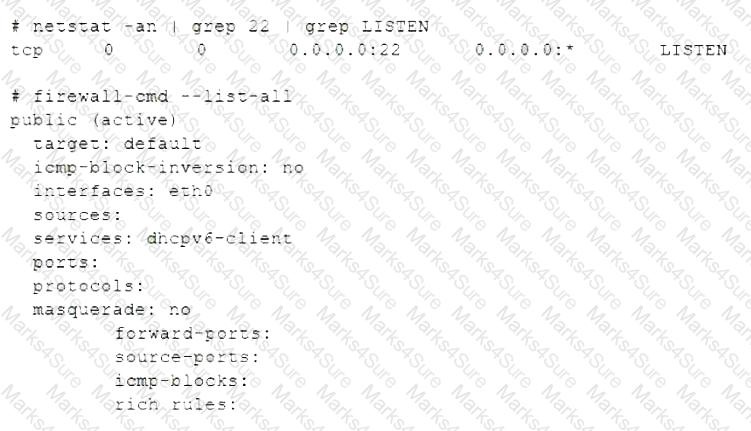
Which of the following commands will resolve this issue?
A developer has been unable to remove a particular data folder that a team no longer uses. The developer escalated the issue to the systems administrator. The following output was received:
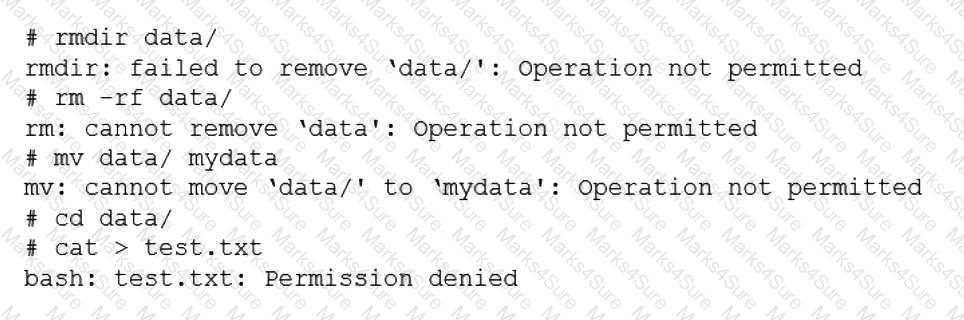
Which of the following commands can be used to resolve this issue?
A Linux system is getting an error indicating the root filesystem is full. Which of the following commands should be used by the systems administrator to resolve this issue? (Choose three.)
An administrator attempts to rename a file on a server but receives the following error.

The administrator then runs a few commands and obtains the following output:
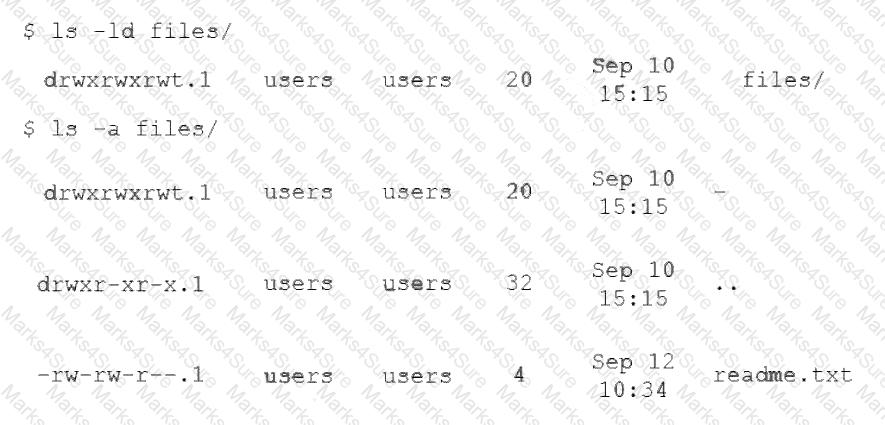
Which of the following commands should the administrator run NEXT to allow the file to be renamed by any user?
A Linux administrator is reviewing changes to a configuration file that includes the following section:
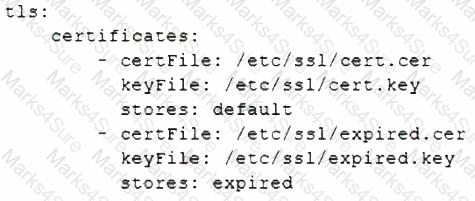
The Linux administrator is trying to select the appropriate syntax formatter to correct any issues with the configuration file. Which of the following should the syntax formatter support to meet this goal?
A Linux administrator intends to start using KVM on a Linux server. Which of the following commands will allow the administrator to load the KVM module as
well as any related dependencies?
A systems administrator is checking the system logs. The administrator wants to look at the last 20 lines of a log. Which of the following will execute the command?
A Linux systems administrator needs to add additional code to code that resides within a repository without changing the original code. Once completed, the additional code will be merged into the main branch. Which of the following commands should the administrator use first?
After installing some RPM packages, a systems administrator discovers the last package that was installed was not needed. Which of the following commands can be used to remove the package?
A hardened physical Linux system allows regular, unprivileged users to remotely connect to the server using SSH only. No sudo tool has been installed. Which of the following should the Linux administrator use to perform administrative tasks on this host? (Select two).
A Linux systems administrator is troubleshooting an I/O latency on a single CPU server. The administrator runs a top command and receives the following output:
%Cpu(s): 0.2 us, 33.1 sy, 0.0 ni, 0.0 id, 52.4 wa, 0.0 hi, 0.2 si, 0.0 st
Which of the following is correct based on the output received from the exe-cuted command?
A user is asking the systems administrator for assistance with writing a script to verify whether a file exists. Given the following:
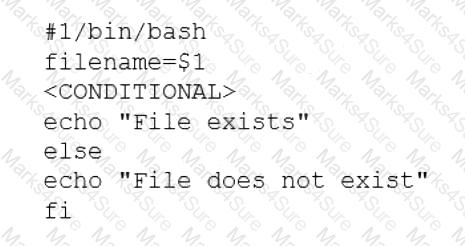
Which of the following commands should replace the
To harden one of the servers, an administrator needs to remove the possibility of remote administrative login via the SSH service. Which of the following should the administrator do?
A systems administrator identifies multiple processes in a zombie state. Which of the following signals would be best for the administrator to send to the PPID?
A security team discovers that a web server has been running with elevated privileges and identifies it as a security violation. Which of the following items needs to be added to the webserver.service file to remediate the issue?
A Linux system is failing to boot. The following error is displayed in the serial console:
[[1;33mDEPEND[Om] Dependency failed for /data.
[[1;33mDEPEND[Om] Dependency failed for Local File Systems
...
Welcome to emergency mode! After logging in, type "journalctl -xb" to viewsystem logs, "systemct1 reboot" to reboot, "systemct1 default" to try again to boot into default mode.
Give root password for maintenance
(or type Control-D to continue}
Which of the following files will need to be modified for this server to be able to boot again?
A user generated a pair of private-public keys on a workstation. Which of the following commands will allow the user to upload the public key to a remote server and enable passwordless login?
Joe, a user, is unable to log in to the Linux system. Given the following output:

Which of the following commands would resolve the issue?
A Linux administrator has set up a new DNS forwarder and is configuring all internal servers to use the new forwarder to look up external DNS requests. The administrator needs to modify the firewall on the server for the DNS forwarder to allow the internal servers to communicate to it and make the changes persistent between server reboots. Which of the following commands should be run on the DNS forwarder server to accomplish this task?
A network administrator issues the dig www.foo.com command and receives an NXDOMAIN response. Which of the following files should the administrator check first?
A systems administrator receives reports that several virtual machines in a host are responding slower than expected. Upon further investigation, the administrator obtains the following output from one of the affected systems:
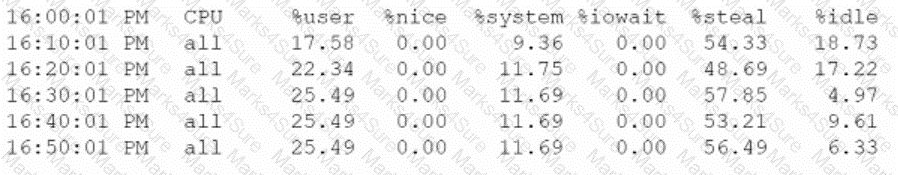
Which of the following best explains the reported issue?
A Linux administrator is investigating the reason a systemd timer is not running every night at midnight. The administrator sees the following unit file:
[Unit]
Description=Execute backup every day at midnight
[Timer]
OnCalendar=--01 00:00:00
Unit=backup.service
RandomizedDelaySec=10800
[Install]
WantedBy=multi-user.target
Which of the following modifications should the administrator make in the unit file? (Select two).
A Linux administrator needs to expand a volume group using a new disk. Which of the following options presents the correct sequence of commands to accomplish the task?
A systems administrator was tasked with assigning the temporary IP address/netmask 192.168.168.1/255.255.255.255 to the interface eth0 of a Linux server.
When adding the address, the following error appears:
# ip address add 192.168.168.1/33 dev eth0
Error: any valid prefix is expected rather than "192.168.168.1/33".
Based on the command and its output above, which of the following is the cause of the issue?
An administrator changed the default port of an SSH server to 2222 on myhost, and clients are not able to connect. The administrator runs some commands and receives the following output:
vbnet
Copy code
$ ssh -p 2222 myhost
ssh:connect to host myhost on port 2222: No route to host
Which of the following commands should be run on myhost?
Ann, a security administrator, is performing home directory audits on a Linux server. Ann issues the su Joe command and then issues the Is command. The
output displays files that reside in Ann's home directory instead of Joe's. Which of the following represents the command Ann should have issued in order to list Joe's files?
A systems administrator is reviewing the following output on the text editor that is being used to update the company's internal database records:
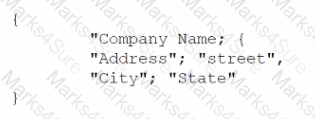
Which of the following extensions should the systems administrator use when saving the file?
A Linux engineer receives reports that files created within a certain group are being modified by users who are not group members. The engineer wants to reconfigure the server so that only file owners and group members can modify new files by default. Which of the following commands would accomplish this task?
A systems administrator is investigating a service that is not starting up. Given the following information:
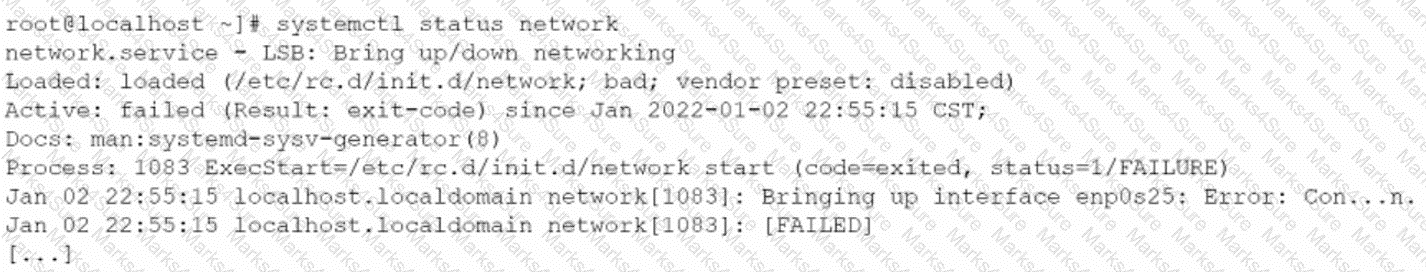
Which of the following systemd commands should the administrator use in order to obtain more details about the failing service?