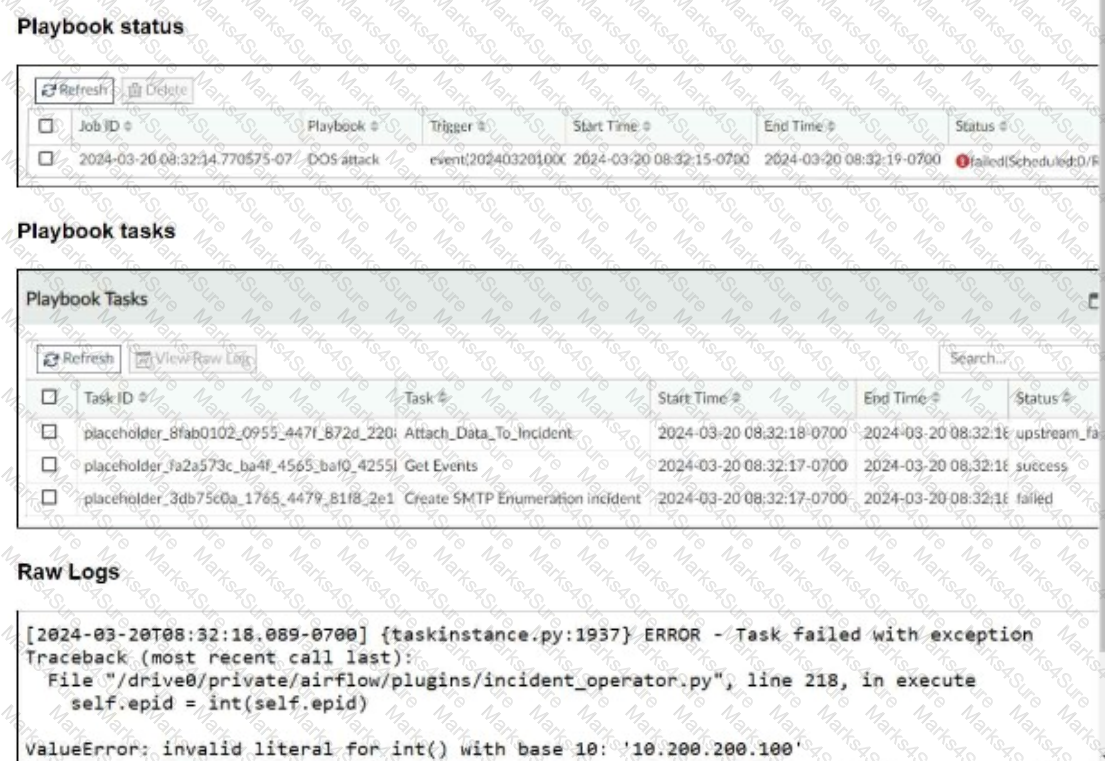
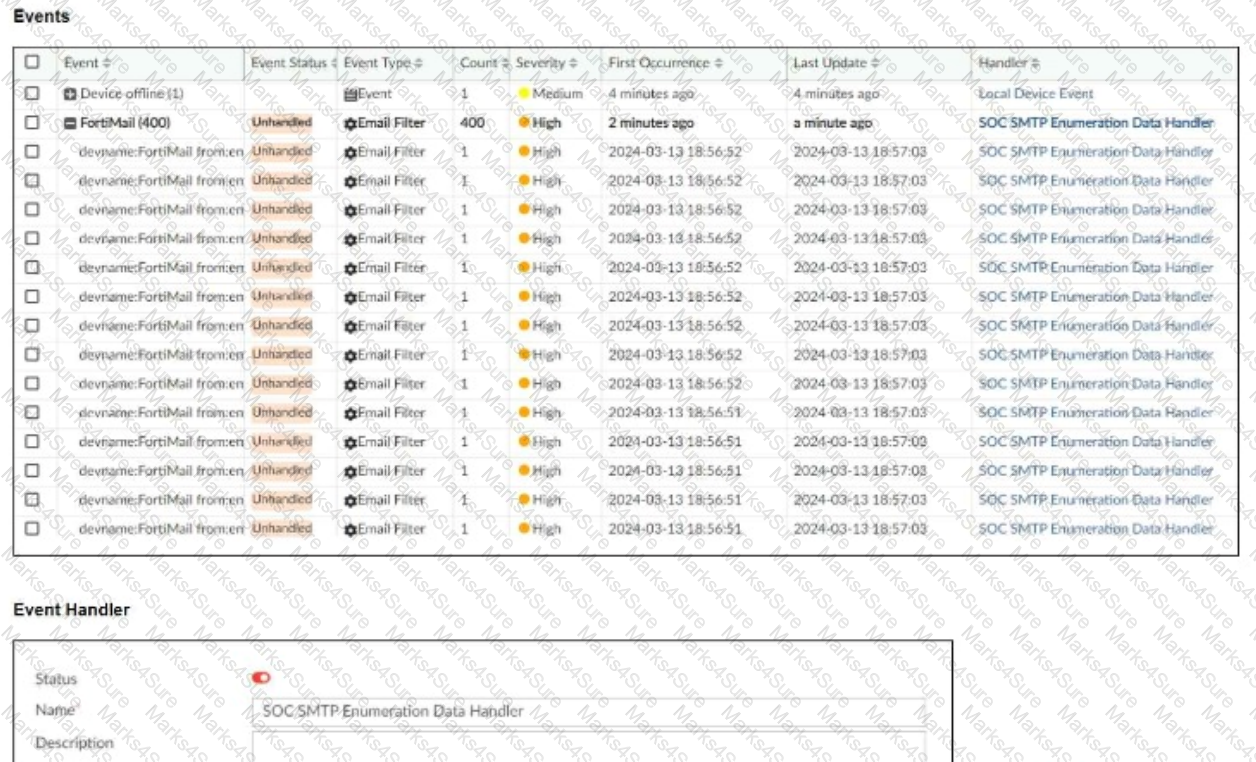
Overview of Indicators of Compromise (IoCs): Indicators of Compromise (IoCs) are pieces of evidence that suggest a system may have been compromised. These can include unusual network traffic patterns, the presence of known malicious files, or other suspicious activities.
FortiAnalyzer's Role: FortiAnalyzer aggregates logs from various Fortinet devices to provide comprehensive visibility and analysis of network events. It uses these logs to identify potential IoCs and compromised hosts.
Relevant Log Types:
[Reference: Fortinet Documentation on DNS Filtering FortiOS DNS Filter, IPS Logs:, Intrusion Prevention System (IPS) logs detect and block exploit attempts and malicious activities. These logs are critical for identifying compromised hosts based on detected intrusion attempts or behaviors matching known attack patterns., Reference: Fortinet IPS Overview FortiOS IPS, Web Filter Logs:, Web filtering logs monitor and control access to web content. These logs can reveal access to malicious websites, download of malware, or other web-based threats, indicating a compromised host., Reference: Fortinet Web Filtering FortiOS Web Filter, Why Not Other Log Types:, Email Filter Logs:, While important for detecting phishing and email-based threats, they are not as directly indicative of compromised hosts as DNS, IPS, and Web filter logs., Application Filter Logs:, These logs control application usage but are less likely to directly indicate compromised hosts compared to the selected logs., Detailed Process:, Step 1: FortiAnalyzer collects logs from FortiGate and other Fortinet devices., Step 2: DNS filter logs are analyzed to detect unusual or malicious domain queries., Step 3: IPS logs are reviewed for any intrusion attempts or suspicious activities., Step 4: Web filter logs are checked for access to malicious websites or downloads., Step 5: FortiAnalyzer correlates the information from these logs to identify potential IoCs and compromised hosts., References:, Fortinet Documentation: FortiOS DNS Filter, IPS, and Web Filter administration guides., FortiAnalyzer Administration Guide: Details on log analysis and IoC identification., By using DNS filter logs, IPS logs, and Web filter logs, FortiAnalyzer effectively identifies possible compromised hosts, providing critical insights for threat detection and response., , , ]